Quick Summary:
RASP is a security innovation that uses runtime instrumentation to identify and thwart threats utilizing data from inside the active software. Comparing it to perimeter-based security measures like firewalls is not appropriate. By keeping an eye on inputs and preventing those that may be used to commit attacks, RASP technology is supposed to increase software security. The definition of RASP, its operation, its significance, and recommended RASP practices will all be clarified in this blog.
For attackers trying to enter the corporation, applications have become a significant target. Black hat attackers know this and use it to their advantage when they discover and use an app vulnerability. Their odds of successfully committing a data breach are more than one in three. According to Contrast Security, 90% of apps are not checked for vulnerabilities throughout the development and quality assurance phases, and even more are left vulnerable during the production phase.
Network defenders must figure out how to defend against assaults on the numerous apps that are operating in the company. The applications can protect themselves by identifying and preventing real-time threats. Before further exploring the subject, let’s first clarify what RASP is.
What is RASP?
Runtime Application Self-Protection is a security system integrated into or linked to an application or runtime environment and can control application execution, identify, and solve real-time threats, according to the Gartner Glossary.
RASP can shield an application from harmful input or behavior when it starts up by examining both the context of the activity and the behavior itself by regularly observing its behavior with the app. Every time RASP operates on a server, and security is applied to the active apps.
All system calls made by the program are intercepted by RASP, which also verifies data requests made inside the application and ensures that they are safe. RASP can secure both web-based and offline apps. Because RASP’s detection and protection capabilities run on the server that the app is running on, technology has no impact on the way the application is designed. Now let’s move forward and look at the types of RASP.
Types of RASP
There are different types of RASP but most commonly the in-process RASP is used. Let’s take a look at the different types of RASP:
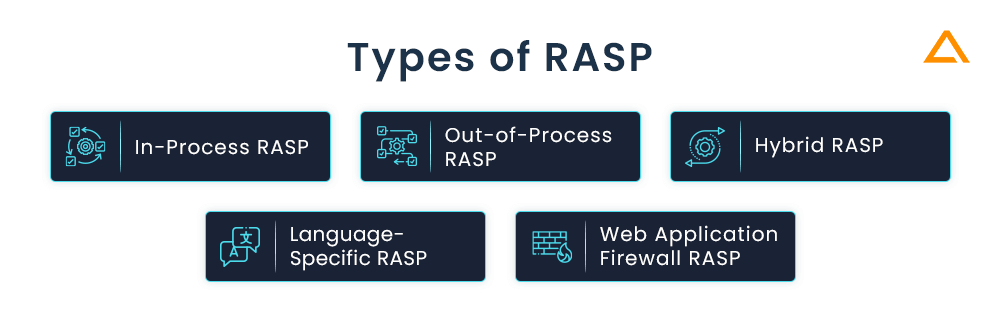
In-Process RASP: With its ability to track an application’s behaviour in real-time, in-process RASP is installed into the application process itself. This enables us to recognise and stop attacks like XSS, SQL Injection, and other OWASP Top 10 vulnerabilities. With more thorough knowledge of the status of the application at its disposal, In-Process RASP is better able to spot and stop harmful activity.
Out-of-Process RASP: As the name implies, this RASP is installed outside the application and may watch how it behaves by examining the network traffic. Because it doesn’t need changes, it is less invasive. In the cloud environment, where it may be problematic, out-of-process RASP is frequently used.
Hybrid RASP: A more complete security solution is offered by hybrid RASP, which includes both in-process and out-of-process approaches. By limiting their flaws, hybrid RASP aims to maximise the advantages of both methods. In-Process approaches are used to examine the behaviour of the application, whereas Out-of-Process techniques can be used to monitor network traffic. Many applications are frequently deployed across several platforms and technologies in complicated contexts, and hybrid RASP is frequently utilised in these situations.
Language-Specific RASP: The purpose of language-specific RASP is to safeguard programmes created in that language. To safeguard Java programmes from common vulnerabilities, for instance, Java-specific RASP would be optimised. For applications written in less popular programming languages that might not be supported by general-purpose RASP solutions, language-specific RASP can offer more focused security.
Web Application Firewall (WAF) RASP: In addition to what a typical WAF may give, WAF RASP binds with a WAF and thus can offer more security features. It can offer real-time monitoring and defence against threats on the application layer, like SQL injection and XSS. By offering comprehensive records and monitoring application activity, WAF RASP can also assist enterprises in meeting compliance requirements.
The exact requirements and limitations of the company and the application will determine which RASP solution is best for them. To make sure the RASP chosen is efficient and suitable for the organization’s goals, it is crucial to carefully assess the potential and constraints of each solution.
How does RASP works?
Instead of being a generic network- or endpoint-level defensive solution, RASP encircles and safeguards a specific application. RASP can track the intakes, outcomes, and internal status of the application it is guarding, thanks to its more focused deployment location. Developers can find vulnerabilities in their apps by implementing RASP.

RASP seizes control of the program whenever a security event happens in-app, finds the issue, and fixes it. RASP will automatically try to stop any activity if it discovers an unexpected security event, such as an attempt to call a database, execute shell commands, attempt SQL injection, open a password-protected file, or run SQL commands. You can defend your application with RASP against serious online threats, including privilege escalation, SQL injections, and cross-site scripting. As a result of its ability to immediately stop threats, RASP can be helpful for companies with limited security resources.
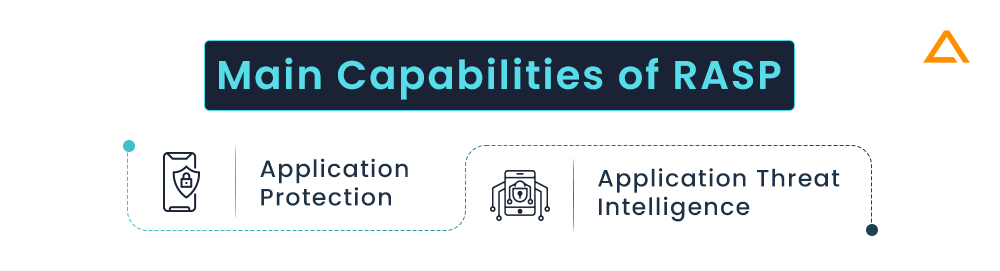
RASP has two main capabilities:
- Application Protection: Correctly thwarting attempts to exploit application flaws while preserving the usage of lawful applications.
- Application Threat Intelligence: provides security teams with visibility into the perpetrators of attacks, the methods they employ, and the apps they focus on, right down to the code level.
Why is RASP Security important?
The security of applications during runtime is frequently provided by technologies like intrusion prevention systems (IPS) and web application firewalls (WAF). Still, these technologies operate in-line while they scan network traffic and content. They cannot see app traffic and data processing as they examine user sessions and traffic to and from applications. They can utilize a significant amount of bandwidth from the security team. They are usually only used for warnings and log gathering because their defensive measures frequently don’t have the precision required for session termination. What is required is a brand-new kind of runtime environment-based application protection technology called RASP.
Also Read: How to Improve Mobile App Data Security?
Security Challenges are involved in the protection of web applications and APIs.
In developing online applications and APIs, there are several security problems. The difficulties are only the tip of the iceberg after security. To defend online applications and APIs, the following four critical security issues must be resolved:
- It is challenging to recognize genuine attacks. Every program has a set of weaknesses that can only be used with certain kinds of assaults. For one application, an HTTP request may be flawless, but it may have disastrous effects for another. Data may also appear differently than what is displayed in the program
- JSON, XML, serialization entities, and proprietary binary formats are just a few examples of modern programs’ complicated forms (and APIs in particular) use. WebSocket, produced via JavaScript in the browser, mobile applications, and many more sources are used by these requests in addition to HTTP
- Traditional technological protections are ineffective, plain, and simple. Till it gets to the application server, HTTP traffic is analyzed by WAFs to function independently of applications. And while a WAF is present in most big enterprises, many lack the personnel and knowledge to do the tweaking required to keep it working, leaving it merely in “log mode”
- There is a quick speed of software development. IaaS, PaaS, and cyberspace are growing like crazy in containers. They make a quick application and API deployment possible; however, new vulnerabilities are introduced into the code. The velocity of development, installation, and delivery has also been quickly boosted by DevOps, which has made it more difficult to guarantee the security of fast-changing software.
Now that you are clear about challenges that you can face while working with RASP, let’s take a step ahead and look at the web app security threats that you can encounter.
RASP offers protection against Cyber Attacks
RASP (Runtime Application Self Protection) is unique as it runs in the application but not on the network. Therefore allowing you to take advantage of all contextual information available within the running application, API, code, framework configuration, OWASP Top 10 vulnerabilites and more.
Attacks
- Clickjacking
- HTTP Response Splitting
- HTTP Method Tampering
- Large Requests
- Malformed Content Types
- Path Traversal
- Unvalidated Redirects
- Software Supply Chain Attacks
Injections
- Command Injection
- Cross-Site Scripting
- Cross-Site Request Forgery
- CSS & HTML Injection
- Database Access Violation
- JSON & XML Injection
- OGNL Injection
- SQL Injection
Vulnerabilities
- Insecure Cookies & Transport
- Logging Sensitive Information
- Unauthorized Network Activity
- Uncaught Exceptions
- Vulnerable Dependencies
- Weak Authentication
- Weak Browser Caching
- Weak Cryptography
Key benefits of RASP
The emphasis on a particular application that RASP has set it apart from other cybersecurity solutions. It can offer various security advantages due to this focus. Here are some of the key benefits of utilizing RASP in creating mobile apps:
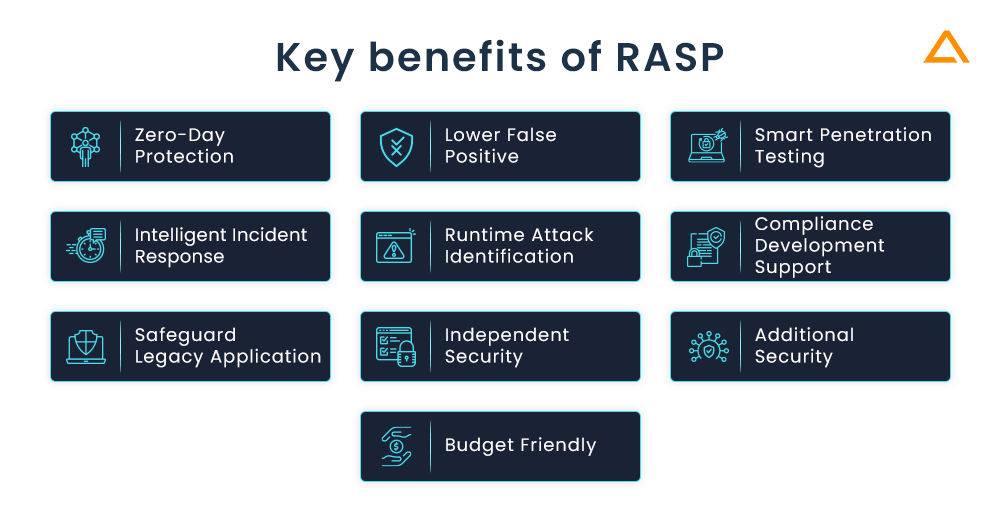
Zero-Day Protection
RASP, however, may employ signatures to recognize assaults. It extends beyond signature-based detection. by seeing unusual activity inside the protected application and acting when it occurs. With its assistance, RASP may be used to identify and thwart even zero-day assaults.
Lower False Positive
RASP has extensive knowledge of an application’s internal workings, which includes the capability to observe how a possible attack impacts the execution of the program. This vastly improves RASP’s capacity to distinguish between simple assaults and false positives. This decrease in false positives lessens the workload on security professionals and allows them to concentrate on real threats.
Smart Penetration Testing
Using RASP technology, you can conduct effective penetration testing for detecting and eliminating vulnerabilities. You can also program the software to detect anomalies and respond, apart from that you can also reprogram and test different scenarios and sections at your convenience.
Intelligent Incident Response
For smart and fast incident response RASP is used. Developers get the real-time data behavior using RASP because it allows them to get a deeper insight into the application run-time, as well as active security logging features. This empowers developers to render effective security designs with additional monitoring capabilities.
Runtime Attack Identification
Developers generally can’t collect the runtime application security data; therefore, the security must be designed based on estimation. With the integration of RASP a lot of things can be changed, using RASP allows developers to get a deep insight into application runtime security events allowing them to align with real-time events.
Compliance Development Support
RASP technology greatly supports the development aspect of applications. With various factors such as real-time data, developers can identify various vulnerabilities in the prime assets. This allows them to develop more secure and compliant applications with few vulnerabilities every time.
Safeguard Legacy Application
For any enterprise legacy applications are valuable assets. However, with the advancement in technology, it’s a difficult task to protect the legacy application. Since most legacy programs were created using outdated standards, it is challenging to protect against contemporary attacks. This problem is resolved by RASP technology, which enables you to add advanced security capabilities to the legacy software without changing its existing code.
Independent Security
When you use RASP, it will act as an automatic security system that identifies and gets rid of threats without the need for human intervention. Hence, we may conclude that it is a stand-alone security solution, where the program defends itself and rewards you with accurate security events and runtime data.
Additional Security
RASP adds an extra layer of security that strengthens security and minimizes vulnerabilities when used with the already installed WAF and IPS security settings. While the firewall guards the program from external attacks, RASP technology keeps an active eye on the runtime and removes dangers from within the app.
Budget Friendly
Considering the amount of security RASP offers it is highly cost-effective. It is a low-maintenance system that guards against threats and actively delivers logs of security occurrences for your apps. Hence, you receive enhanced security, analytics, and development advantages all in one.
Also Read: App Security – Vulnerability, Best Practices, Testing Tools & Checklist
How RASP Helps in Securing the Application
Unlike traditional web app security tools, RASP uses the app’s data and logic so it can detect, block, and report attacks. When the system detects abnormal behaviour in the application it automatically isolate and identify the issues. RASP has the ability to alert, protect, and resolve security events depending on the severity. Since RASP is a recent development in the information security world, it helps to detail where RASP fits into organization.
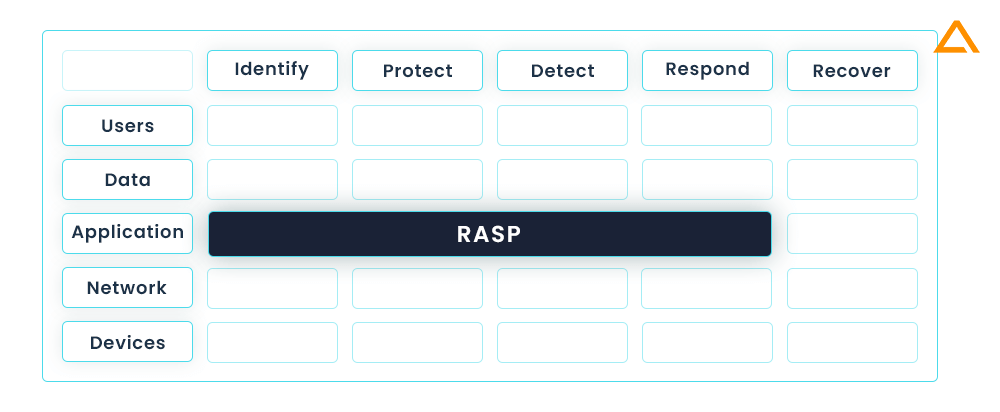
The NIST Cybersecurity Framework is kept in mind while creating the above diagram. The NIST matrix is widely recognised set of guidelines for improving cybersecurity risk management with the NIST Cybersecurity Framework. Here is how RASP helps in each of the five functions of the framework.
| Functions | Description |
| Identify | By monitoring its behaviour RASP can detect the potential threats for any suspicious activities. |
| Protect | By preventing the attacks in real-time, RASP reduces the risk of compromise. |
| Detect | By analyzing its behaviour and alerting security personnel when suspicious activity is detected, RASP can help and protect your application. |
| Respond | RASP an help you by automatically responsing to the attack by blocking malicious activity or providing alerts to the security personal so that they can take appropriate action. |
| Recover | By providing detailed logs of the attack, RASP will help you recover from attacks by providing detailed logsof attack. These logs can help you identify vulnerabilities and strength the application’s security. |
RASP offers regular checks, realistic threat detection and prevention, greater visibility and control, and helps integrate with the NIST Cybersecurity Framework to give an extra layer of security to your application.
How to Deploy RASP Solution?
As the newest development in the software solutions, RASP is a software solution not a network device. Therefore the deployment process is also different from traditional security solutions. There are two basic models for deploying RASP. These models doesn’t only differs technically but also in which teams take ownership and control over RASP.
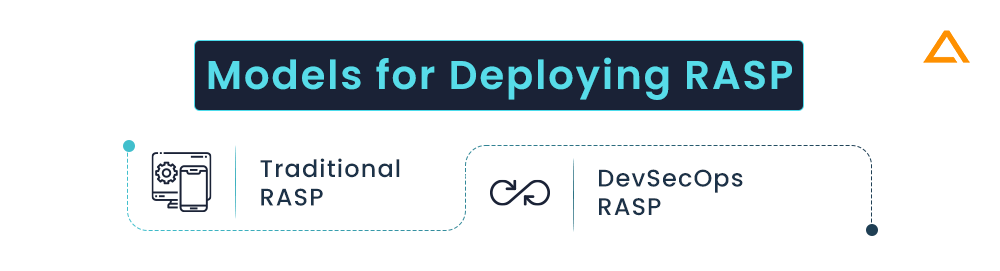
Let’s begin with the first one Traditional RASP.
Traditional RASP
The “conventional” firms that are just searching for a better technology to safeguard apps and APIs in their operations utilise this strategy. They will be responsible for installing, configuring, and monitoring the RASP. These firms have an operations staff that is in charge of production security. The output from the RASP may also be monitored by a security operations centre (SOC), which can also look into occurrences and take appropriate action.
Solutions such as Chef, Ansible, Puppet, and other enterprise technologies, or anything else that can operationalize executing an installer, can be used extensively in these enterprises to deploy RASP. Usually speaking, you should begin in “log mode” to ensure that protected programmes function properly. RASP can also be installed in “block mode” in test environments to increase confidence before moving to production.
As traditional RASP is covered let’s move on to the second DevSecOps RASP
DevSecOps RASP
This paradigm, as its name implies, is intended for “DevOps” enterprises that want to integrate RASP into the distribution of apps and APIs. Development, operations, and the RASP should all be handled by the same team in these organisations. The main difference is that RASP may be incorporated into APIs and apps, and it will be tested and implemented alongside other software. You can begin using RASP in “block mode” from the beginning because it is a component of the application that runs continuously.
RASP can be used in a variety of ways in these organisations. RASP can be incorporated into regular builds, integrated into software during CI/CD, added to containers like Docker and Kubernetes, and deployed using Ansible or other tools. For settings like Pivotal, AWS, Azure, and others, several products offer plugins or tiles. The optimum strategy is to incorporate RASP into the software deployment process as it is now done.
Along with this there are RASP security development modes. Now let’s move forward to them.
RASP Development Modes
According to needs, RASP can be implemented in any of the following modes, which are the ones it typically comes in:
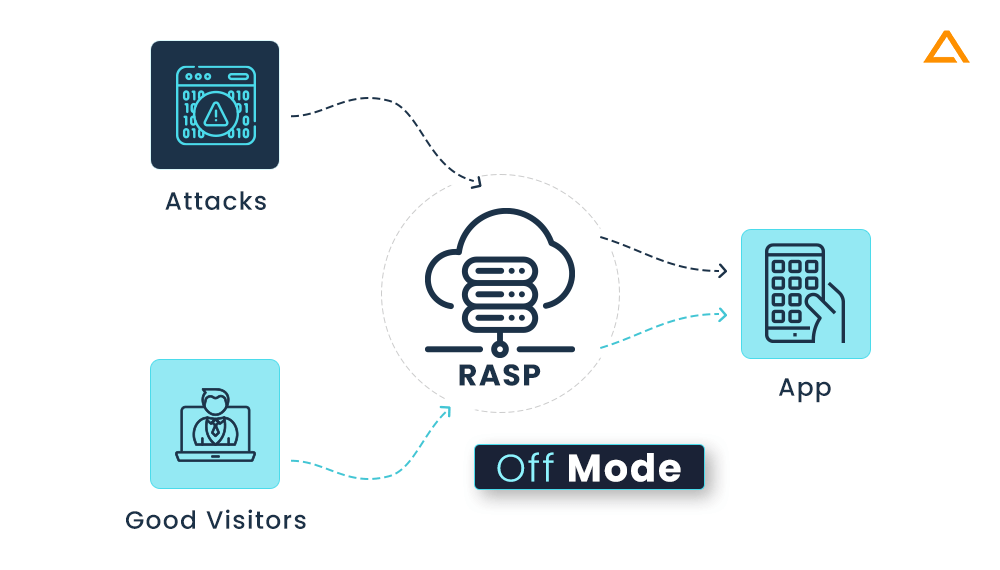
Off Mode: blocking or monitoring of calls is not possible in off mode. Without any intervention from the RASP solution, all requests are simply forwarded in this case:
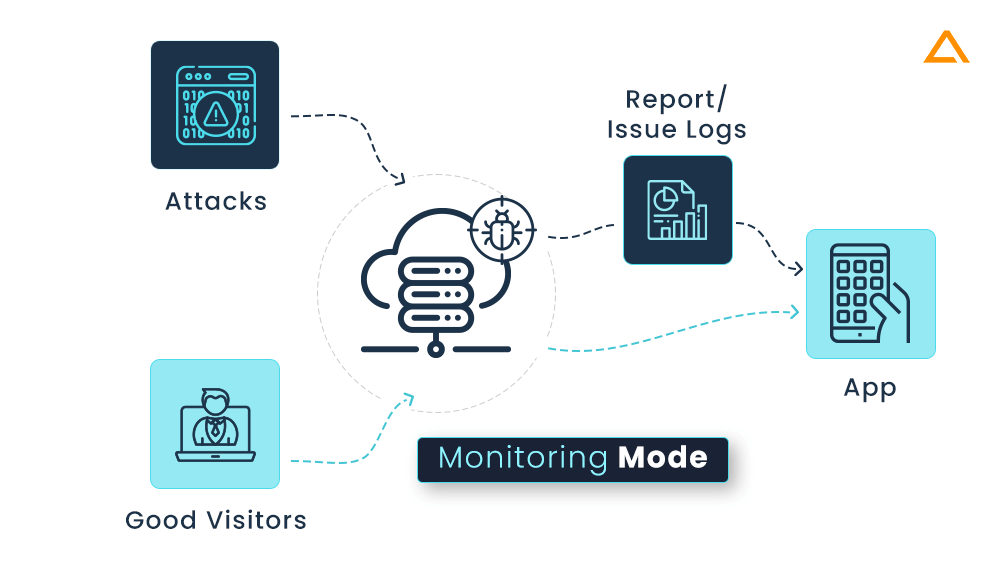
Diagnostic/Monitoring Mode: when an application is monitored by a RASP programmer for dangers, logs are kept, and alerts are sent, but no requests are blocked:
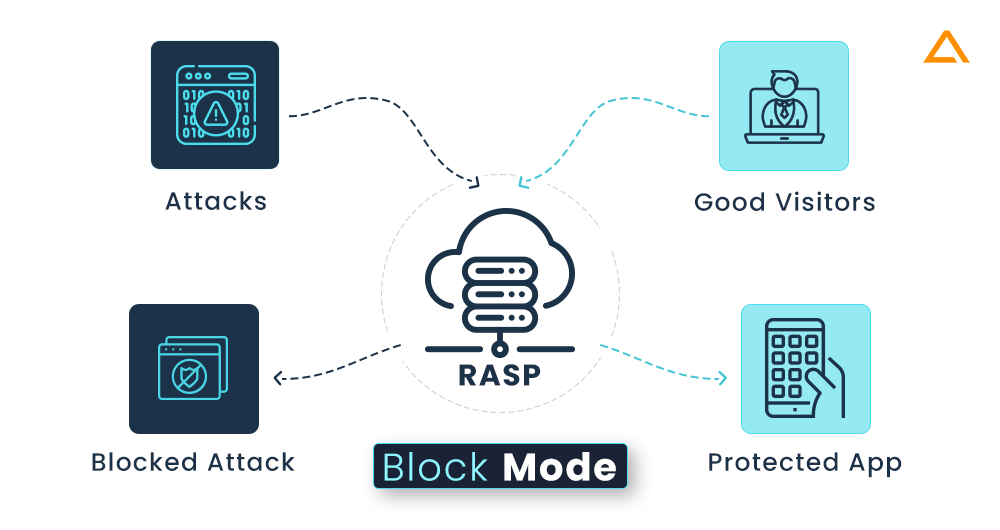
Block Mode: In this mode the RASP programme blocks any unauthorized queries:
Block at Perimeter Mode: Identical to block mode, except that here the RASP solution is given specified predefined rules & required actions to thwart assaults even before they are handled by the application. The RASP solution alerts you and disables the attack vector if it does not comply with the rules you’ve established. A RASP programme acts like a WAF in this mode.
How to Select RASP Solutions?
In this section, we’ll look at some of the main issues related to RASP deployment since each RASP solution on the market differs slightly from the others. You should test each RASP product to make sure it operates in your environment because they all operate differently:
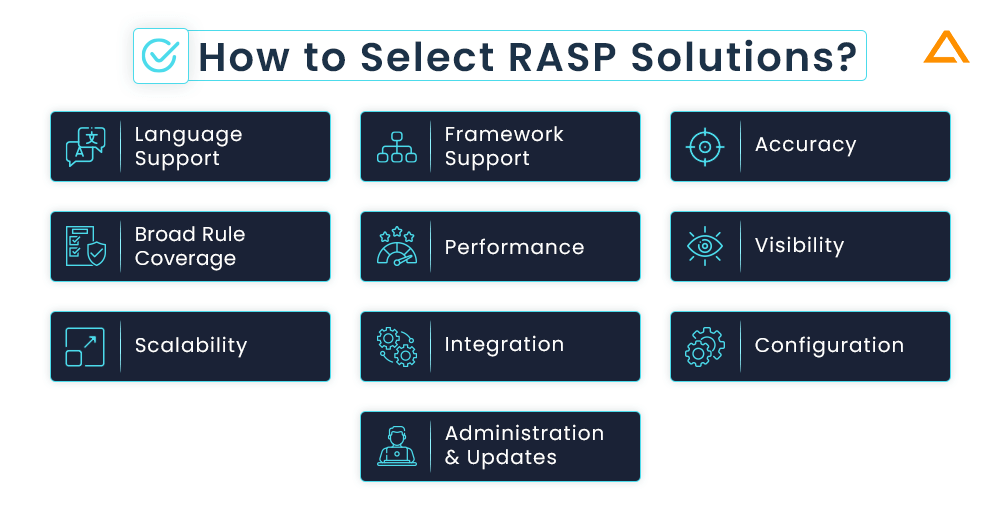
Language Support
You’ll want to confirm that the vendors you choose support the languages used in your critical apps and APIs because different vendors often only support a limited set of languages.
Framework Support
Framework coverage for applications is equally crucial to language coverage. It isn’t going to defend against attacks if your RASP doesn’t support your frameworks.
Accuracy
Using an application with a realistic collection of genuine vulnerabilities will allow you to assess correctness. Make sure to properly check that the RASP blocks exploits without obstructing application use.
Broad Rule Coverage
You’ll need to hunt for a comprehensive ruleset that addresses the assaults you are worried about. Common vulnerability classes and published vulnerabilities should both be included in this (CVEs).
Performance
From a few microseconds to several milliseconds, RASP latency varies greatly. Just compare the performance of your application with and without RASP.
Visibility
For Visibility of your RASP you should keep these questions in mind: Does you RASP solution has dashboard? Does it rely on SIEM only? What are the reports, notification and alerts does it supports?
Scalability
Verify whether RASP can expand to hundreds of APIs and thousands, or both. To see if SIEM plugins are available, check as well.
Integration
Before integrating RASP solution to your application make sure you have answer to these questions. For popular security and DevOps technologies, does RASP offer plugins? For every piece of data gathered, is there an API? Is it possible for administrators to perform operations via the API?
Configuration
Ask yourself these questions before configuring any RASP in your solution. Does RASP’s protection involve static or dynamic inspection of the application’s configuration or database schema? Can RASP be installed in block mode with the default settings without having a negative impact on applications?
Administration & Updates
Is it possible to centrally update RASP functionality and rules? Software updates are they automatic? Does RASP have features that are common in corporate software, such as LDAP connectivity, robust authentication, enterprise-grade access control, encryption of data in transit and at rest, and complete security logging?
RASP vs. WAF
Web Application Firewall & Runtime Application Self-Protection are complementary approaches to application security. Although many known threats are filtered by WAF prior they reach the application, it only serves as the first line of security. On the other hand, RSAP takes advantage of the context that extensive visibility into these apps provides to find and deal with assaults that evade Web application firewalls.

Although WAF aids in adding a layer of protection to your application, it does so by predetermined rules. In contrast, RASP aids in preventing harmful application activity from taking place inside the program itself. These technologies are distinct from one another despite being interchangeable in some situations. You can better explain both technologies with the aid of this section.
There is no assurance that a WAF can thwart the most recent types of assaults that haven’t yet been seen. A WAF will need to learn to be effective. RASP’s, on the other hand, offer a far more flexible real-time defense against a range of application-layer threats.
RASP can still keep an eye on and safeguard the program’s security even as it is being updated and developed since it leverages the application itself. Combining their strengths to offer thorough and reliable application security, WAF and RASP can complement one another. With WAF, you can determine the nature of the requests being made for your application.
In contrast, RASP examines how the program handles the requests. Therefore, if someone is using Metasploit, the app owner can see that an exploit has caused a file to be written to a location where it shouldn’t be, an executable to be run on the system, unauthorized SQL access, or some unintended assets to be packed on a web page browser-side that could result in data exfiltration.
It is important to understand this so we have reduced all this information to a tabular format. [As per, 17th IEEE International Symposium on Computational Intelligence and Informatics]
| Factors | RASP | WAF |
| Accuracy | Monitors the inbound & outbound logic, as well as logic flows, where it detects the input when it passed into the library, calls where exploitation would occur. | It works on detecting input based on pattern matching, it doesn’t take into consideration that the input entered can be malicious. |
| Reliability | Opens successfully even when the server is under a lot of traffic because the code is always instrumented. | It has a single-point failure, which is likely to fail under heavy stress, and won’t open, leaving the previously protected web application accessible. |
| Visibility | It can give developers in-depth feedback and help them fix vulnerabilities in their code. | On the other hand, WAF doesn’t provide any insightful information regarding the application. |
| Time to Value | It is not necessary to be aware of the locations of application code vulnerabilities because a virtual patch can address a vulnerability. | It requires sufficient coverage of the application and necessitates considerable testing and configuration. |
| Platforms | Can run on any Instrumented application | Can run on web applications |
| Maintenance | RASP automatically understand application changes | Gains application context regularly training, and needs Maintaince to stay in sync with application changes. |
| Network Protocol | RASP handles HTTP, HTTPS, AJAX, SQL and SOAP e | Must be able to understand the application’s network communications |
| Language Coverage | RASP requires complicated, language specific builds currently known products support .NET and JAVA | It is not bound by programming language type |
RASP best practices
As with all technology, there are recommended practices when using RASP. Best practices are also included for you to adhere to. To get as much out of RASP solutions, follow these three suggestions:
Put RASP to use as a component of your complete application security strategy
A company’s defense against current security risks shouldn’t be limited to RASP, even though RASP does a superb job of safeguarding the company from different intrusions. A comprehensive security strategy is provided while leveraging the DevOps methodology, which moves security to the left in the SDLC. With a higher possibility of attack avoidance, this helps. You might also decide to use a RASP solution with integrated WAF capabilities to leverage the benefits both tools offer, depending on the specific security requirements of your business.
Analyze the RASP solutions’ ability to fit into your DevSecOps ecosystem
Consider how a RASP product could integrate with other technologies you already use, especially DevSecOps systems, as you evaluate it. A sophisticated RASP solution may, for instance, interface with your current SIEM, Orchestration, or DAST. Through APIs, webhooks, and cutting-edge technologies, this integration enables your business to use numerous threat intelligence feeds so you can better monitor and stop attacks in real-time.
Before putting RASP solutions into use, thoroughly test them
RASP frequently results in performance difficulties with the apps it monitors because of its tight integration. Whether or not these problems are critical enough to affect users, they could be angry with the performance change. To ensure that the RASP solutions have no adverse effects on the ecosystem’s application performance, it is advisable to evaluate them thoroughly.
Common RASP use cases
You can incorporate RASP into your software in a variety of typical use scenarios. Below is a list of examples of how security administrators, DevOps teams, and developers use RASP to tackle some of the issues that application security is now facing:
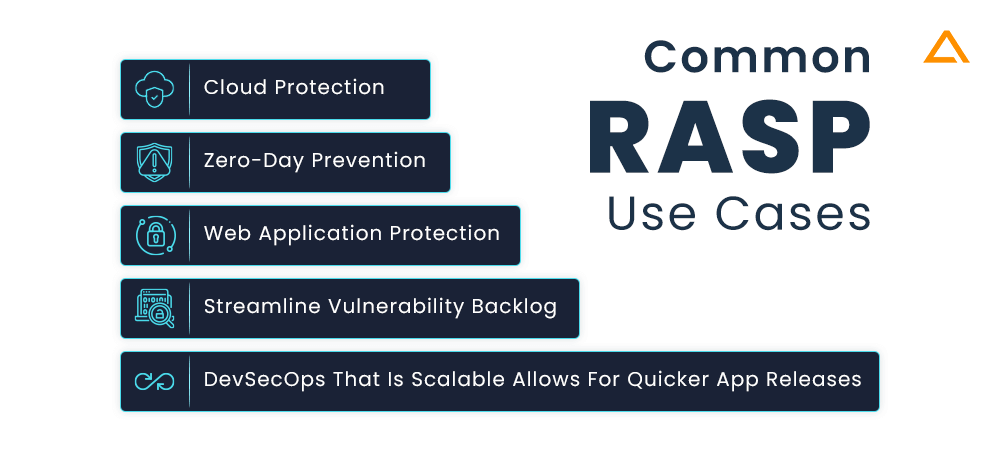
Streamline Vulnerability Backlog
Pre-production vulnerabilities are found using application security testing (AST) techniques. Nonetheless, the backlog keeps growing in the majority of businesses over time. Programs frequently have known vulnerabilities when they are launched into production but nonetheless perform essential business and transactional operations. Since RASP can neutralise the threat in the event of an attack in production, more than 95% of the backlog may ultimately not need to be remedied or rectified by developers. results in substantial resource and expense savings as well as increases in efficiency.
Devsecops That Is Scalable Allows For Quicker Application Releases
The lifetime of software development and application security frequently clash. RASP delivers security more smoothly if it is put directly into the automated DevOps funnel using Continuous Integration and Continuous Development tools, ensuring that controls are always “baked” into every release by default. Without worrying about security flaws, organisations may release applications into production more quickly. By fostering increased trust and communication between teams and reducing operational friction, this skill aids in the alignment and fluidity of SecDevOps and DevSecOps.
Web Application Protection
Online apps and APIs are essential parts of every enterprise, but they can be exposed to a variety of threats. Because they are accessible over the public Internet, these programmes frequently include weaknesses that can be used against them. An business can lower the risk of cyberattack and reduce the system vulnerabilities of its web-facing infrastructure by implementing RASP to safeguard these apps and APIs.
Zero-Day Prevention
A patch cannot be implemented until it has been created and made available, even though an organisation may have procedures in place to do so for essential applications and systems. RASP can be used to defend against zero-day vulnerabilities for a company’s essential applications, which could include online applications and APIs.
Cloud Protection
As applications run on the leased environment, it can be difficult to fully secure the cloud infrastructure. Using RASP in cloud will provide with the high-level of security in a large infrastructure-agnostic form.
RASP Tools
RASP is similar to other technologies in that it has a wide range of tools accessible on the market. The tools for RASP that are most often used nowadays are listed below:

Imperva Real-time Application Self Protection (RASP)
Imperva’s RASP is integrated into an app runtime environment that can defend against OWASP’s Top 10 Vulnerabilities and Zero-Day Attacks. It is also very accurate and requires no tuning. Additionally, you gain protection from route traversals, malformed contents, unvalidated redirection, big requests, clickjacking, and HTTP response and method manipulation. With Imperva, you are protected from injections including cross-site scripting, command injection, SQL injection, and CSS and HTML injection.
Fortify
Fortify Application Defender from Microfocus lets you keep an eye on your apps while defending them in real-time against flaws and frequent assaults. While safeguarding production apps against zero-day attacks, it distinguishes between appropriate requests and harmful threats in.NET and Java programs. Its end-to-end app security solutions cover all phases of your development lifecycle. In addition to providing line-of-code information, Fortify also provides logging visibility and exploits data for online apps. Additionally, it enables you to comply with security requirements, reports a vulnerability, and record triggers to log management or SIEM without modifying the source code.
Sqreen
To identify an attack that may take advantage of flaws in the manufacturing process, Sqreen’s RASP makes use of the whole request environment. Furthermore, it avoids false positives while mitigating serious assaults. It provides zero-day coverage and protects your application against the Top 10 OWASP Vulnerabilities, including XSS, SSRF, SQL injections, and others. It never makes use of signatures and patterns that are simple to break and can fast adapt to your application stack.
Wrapping up!
Application Security has long been a topic of discussion. It has been divided into development and operations, with testing being key and protection being crucial in the latter. It is simple to acquire insight into how attacks operate using sophisticated defense tools and techniques. With the aid of RASP, you can identify and fix the vulnerability without needing to make any modifications to the application. Since attackers are increasingly focusing on apps, businesses need to have sophisticated, multi-layered application security policies that protect consumer data. RASP allows businesses to integrate more thorough app security measures directly into running applications, precisely identifying and preventing dangerous threats in real-time. Because of this, RASP may be useful in an organization’s toolbox for application security.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites
Also Check:


 Say
Say