Quick Summary:
How safe is you react application? With the rapid development and deployment, do you know if vulnerabilities lurk beneath the surface? Let’s explore the intricacies of React Security landscape in this blog. From authentication to protection to XSS and CSRF attacks, fortify your understanding and shield your react from the sophisticated cyber-attacks.
In this blog, we’re going to discuss📝
In React Development, crafting user-centric applications is important. However, there is one important concept that has been overlooked in the software development lifecycle. The aspect is ensuring the security of these applications.
Security vulnerabilities in React apps can have significant consequences. Incorrect user information can leave the door open for cross-site scripting (XSS) attacks, where malicious scripts steal sensitive information or redirect users. Similarly, SQL injection vulnerabilities can be used to manipulate data and corrupt entire systems.
React Security provides essential protection against such threats. By adhering to best practices such as data trust, secure communication protocols, and dependency management, developers can build robust and reliable applications This ensures that user data remains secure, provides reliability, and it makes the app successful for a long time.
Building a React application is exciting, but don’t forget the security! Just like any good fortress, your app needs defenses against hidden threats. Let’s explore some of the most common vulnerabilities React applications face and equip ourselves with strategies to combat them effectively. This will ensure the integrity of your creation and keep user data safe.
Most Common Security Threat to a React Application
Because Reactjs is such an essential element of the tech stack, consider your company’s inescapable reactjs security risks and ramifications. And, because React.js is updated and improved regularly, the list of react security vulnerabilities is extensive. We’ll go over the six most prevalent cyber assaults on react.js in this part. Let’s take a closer look at each of them:
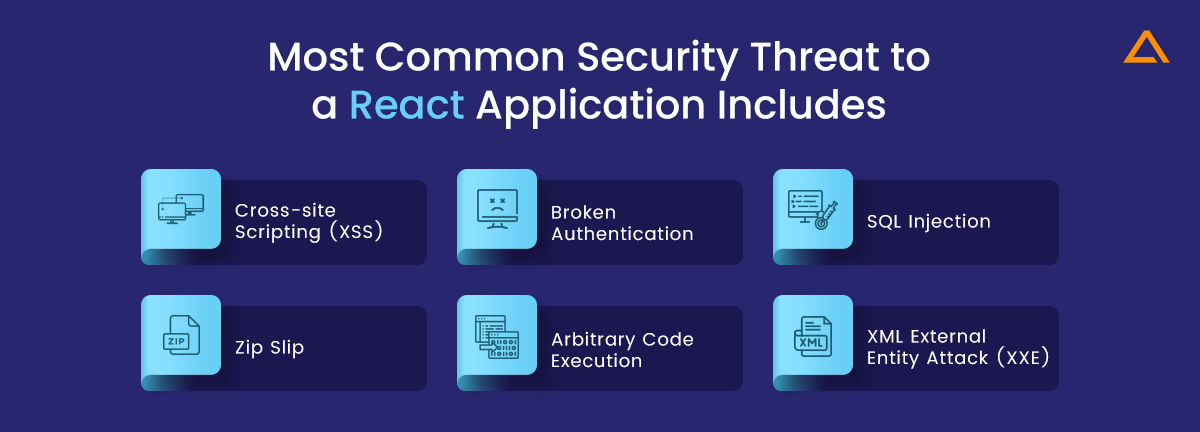
Cross-site Scripting (XSS)
Cross-site Scripting is the first of several security issues with reactjs. An injection of a malicious script into the code of a web application is referred to as XSS. This script gets picked up by the browser and interpreted as authentic. The malicious code is then executed as part of an app. The following diagram depicts the process of an attacker injecting XSS code to steal a user’s or visitor’s session cookies:
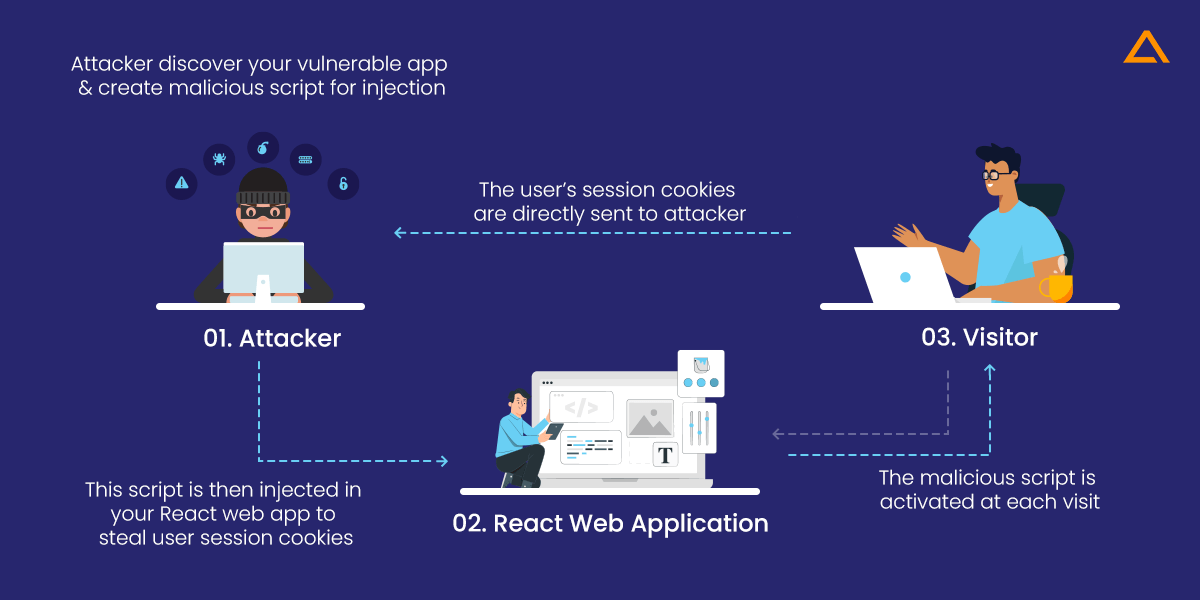
A successful XSS attack might allow the attacker to steal the user’s credentials, take sensitive data from the app’s pages, transmit the request to the server, and more.
Reactjs, like most modern frameworks, has an XSS defence built-in. SQL Injection is frequently confused with SQLi. Even though they both suggest malicious code injection, they are not the same thing. On the other hand, XSS makes the user susceptible, whereas SQLi attacks the application. There are in-built solutions for protecting XSS attacks. Regrettably, they aren’t entirely adequate. XSS is the most popular JavaScript attack to this day.
How to prevent Cross-site scripting attack
It is important to maintain the security integrity in you react application to prevent the cross-site scripting. Here’s how you can strengthen your defense.
Sanitize Input
Validate & sanitize all user input, including from the submissions and URL parameters, to strip away any potentially malicious scripts. Use React libraries such as DOMPurify to ensure safe rendering of user-generated content.
Implement Content Security Policy
Enforce a strict CSP specifying a trusted source for scripts, styles, and other features. This prevents the use of inline scripts and reduces the risk of XSS attacks by defining an approved origin for the content
Escape Output
Encode user-generated content appropriately before rendering it on the page. This prevents browsers from interpreting input as executable scripts by converting special characters in HTML entities.
Regular Security Audit
It is important to conduct routine security audits of your React application’s codebase to identify and address any potential XSS vulnerabilities. Automated tools like eslint-plugin-react can assist in detecting unsafe patterns in your code.
Understand it better with the example given below.
Let’s look at the Samy worm, which exploited the MySpace XSS vulnerability, for a better understanding. One of the most rapidly spreading viruses in history.
import React, {useState} from 'react';
import createDOMPurify from ‘dompurify’;
function App(){
const [text, setText] = useState(‘’);
function updateText(e){
setText(e.target.value);
}
return (
<div>
<input onChange={updateText} type="text" value={text} />
<div dangerouslySetInnerHTML={{__html: createDOMPurify(text)}}/ >
</div>
)
}
export default App;
Also Read: – Best React UI Framework You Should Know In 2024
Broken Authentication
An inadequate or insufficient authorization is another major problem with React.js applications. Session IDs being exposed in URLs, attackers discovering easy and predictable login details, the unencrypted transmission of credentials, valid sessions lasting after logout, and other session-related aspects are all hazards linked with broken authorization. As a result, attackers may gain access to user credentials and conduct brute force assaults.
How to prevent Broken Authentication attack
Consider these ways to strengthen protection against Broken Authentication attacks in React applications:
Implement Strong Session Management
Enforce strict meeting completion policies and implement exit procedures from users during off hours. Additionally, use secure methods for the generation and temporary storage of session tokens to prevent session hijacking.
Employ Secure Password Storage
Use industry-standard hashing algorithms (e.g., bcrypt) to securely store passwords in your database. Avoid saving your passwords in plain text or using weak hashing techniques that are easily compromised.
Role – Based Access Control
Implement RBAC to restrict access to certain features or resources based on users roles and permissions. This will ensure that users can only access to the functionalities relevant to their roles, reducing the attack surface for potential exploits.
Regular Security Audits
Conduct periodic security audits and code reviews of your authentication processes to identify and address any vulnerabilities or misconfigurations. Use specialized tools and systems for security testing to ensure full coverage.
SQL Injection
SQL Injection sometimes referred to as SQLi, is a standard web application attack. The cybercriminal aims to use logical database manipulation to gain sensitive data that should not be displayed. Attackers attempt to gain access to sensitive information to obtain phone numbers, payment information, and other information.
The attackers can use this response react security strategy to regulate access to the server, pull data, and modify database values. Hackers can potentially erase data in addition to altering it.
How to prevent SQL Injection attack?
To prevent SQL injection attacks in you react application. These are some of the key best practices that you need to keep in mind.
Use Of Parameterized Query
Instead of adding user input directly to an SQL query, use parameterized query or prepared statements provided by your database library. Parameterized queries strip SQL code from user input, preventing attackers from entering malicious SQL commands.
Input Validation & Sanitization
Validate and edit all user inputs and ensure they conform to required formats and do not contain bad characters or SQL commands. Use a library/framework that provides built-in input validation functionality to facilitate this process.
Least privilege principle
Ensure that database user accounts used by your application have the least privileges necessary to perform their required tasks. Limited access to only the necessary database operations decreases the potential impact of SQL Injection attacks.
Content Security Policy
Use CSP headers to restrict the sources from which scripts and style sheets can be loaded. This can help mitigate the impact of successful SQL Injection attacks by preventing malicious scripts from being installed.
Escaping Special Characters
If parameterized queries are not possible in some scenarios, ensure that special characters have successfully escaped user input before entering them into SQL queries. This prevents the database from misinterpreting the input as an SQL command.
Consider the following scenario, in which the owner is the current user-ID.
string query = "SELECT * FROM logondata WHERE owner = "'"
+ empID + "' AND empName = '"
+ EmpName.Text + "'";
The following query gets generated by combining both the employee ID and employee name.
SELECT * FROM logondata
WHERE owner =
AND empName = ;
The issue here is that the main code uses the concept of concatenation, which aids in the combination of those data. As the employee name, the attackers can use a string like 'empName' or 'x' = 'x'. As a result, the statement returns True for all table values. As a result, the following question becomes:
SELECT * FROM log data
WHERE owner = 'Adien.'
AND empName = 'name' OR 'x' = 'x';
Zip Slip
Zip Slip is the third item on the list of reacting security concerns. In React applications, a vulnerability is known as “zip-slip” includes exploiting the feature that allows users to upload zip files.
If the archive used to unpack the zip file is not secure, the attackers could unzip the uploaded files outside of the given directory and obtain access to the file.
How to prevent Zip Slip attack
To prevent Zip Slip attacks in your React application follows this preventive measure.
Validate file paths
When processing zip files or extracting their contents, verify the file paths and make sure they are in the directory structure you want to create. Use the secure methods provided by your programming language or framework to inspect and edit file paths before extracting them.
Use Safe Extraction Libraries
Use well-established and secure libraries that implement adequate protection against Zip Slip vulnerability for zip file extraction. These libraries typically verify file paths and prevent directory roaming attacks by default.
Restrict Extraction Paths
Limit filtering options to specific directories or locations in your application’s file system. Zip files Avoid allowing files to be extracted outside of the specified directories, to reduce the impact of Zip Slip attacks.
Implement File Permission
Set appropriate file permissions for extracted files to restrict their access and prevent unauthorized execution. Ensure that sensitive files are not accessible to unprivileged users or processes.
Arbitrary Code Execution
ACE is another one of the most significant security vulnerabilities. ACE is a software or hardware security vulnerability that allows arbitrary code execution. The capacity of an attacker to execute arbitrary code on a target process is known as arbitrary code execution (ACE). An arbitrary code execution exploits when a product or software is abused using this vulnerability. This vulnerability is particularly hazardous because it can arise in some public products, exposing all people who utilize it.
How to prevent Arbitrary Code Execution (ACE) attack?
To prevent code execution attacks on your React application blocking is essential to maintaining its security. There are several preventive measures:
Input Validation & Sanitization
Validate and sanitize all user inputs properly to prevent injection of malicious code. Use procedures for server-side validation and client-side input validation to ensure that user-supplied data follows the required formats and that no code can be executed
Content Security Policy
Use a strict CSP to reduce the risk of executing arbitrary code injection via malicious scripts or payloads. Configure the CSP to limit the sources from which scripts and other components can be installed, reducing the attack surface to those that can be exploited.
Use Trusted Libraries & Dependencies
Use only well-established and trusted libraries and dependencies in your React application. Update these dependencies regularly and patch known vulnerabilities to reduce the risk of arbitrary use of third-party code.
Enable Runtime protections
Use runtime safeguards such as sandboxing and code signing to reduce the impact of arbitrary code execution attempts. Implement tools and techniques that monitor and limit the execution of suspicious code in real time to increase the security of your application.
The WannaCry ransomware outbreak is the finest example of how these attacks work.
XML External Entity Attack (XXE)
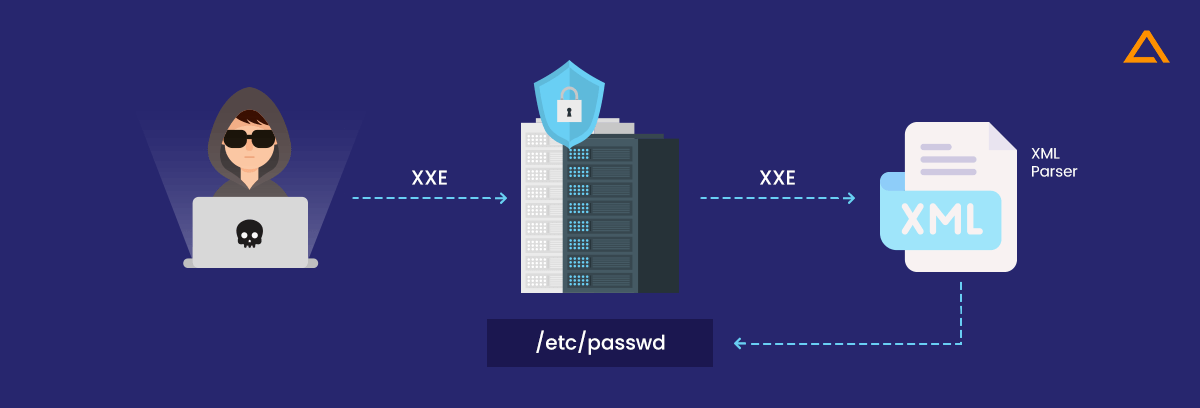
XXE is another one of the react frontend security problems. Web applications that use XML (Extensible Markup Language), a text-based language for storing and organizing data in a web app, are vulnerable to XXE assaults. An XML parser is required for converting XML into usable code. These attacks frequently target such parsers, and an attacker can use XXE to launch a CSRF or DDOS assault. The fundamental problem is that XML parsers are vulnerable to these attacks by default. Thus, it’s up to your development team to protect yourself.
How to prevent XML External Entity Attack
Consider the following preventive measures to prevent XML external entity (XXE) attacks in your React application:
Disable External Entities
Enable the parsing of external objects in the XML parser used in your application. This can be accomplished by developing a parser framework or libraries that provide mechanisms to work around external entity resolution.
Use XML Parse with XXE Protection
Use XML parsers with built-in protection against XXE attacks. Choose a well-maintained and up-to-date XML resource library that has implemented security features such as entity extension restrictions or strict parsing modes.
Input Validation
Authenticate and sanitize all XML input received from untrusted external sources. Use rigorous input validation to ensure that XML documents do not contain malicious content or issues with external resources.
Use XXE Firewalls
Use specialized firewalls or security devices that can detect and block XXE attacks in the direction of the network. This solution can provide additional protection against malicious XML payloads.
Leverage Whitelisting
Use whitelisting techniques to allow access only to known, trusted entities in XML documents. Whitelisting can help prevent unauthorized outside entities from joining and reduces the risk of XXE attacks.
Also Read: – Best React Developer Tools
14 React Security Best Practices
Here are some tips for securing react apps. These react security solutions will help resolve the issues that might arise while securing the react application.
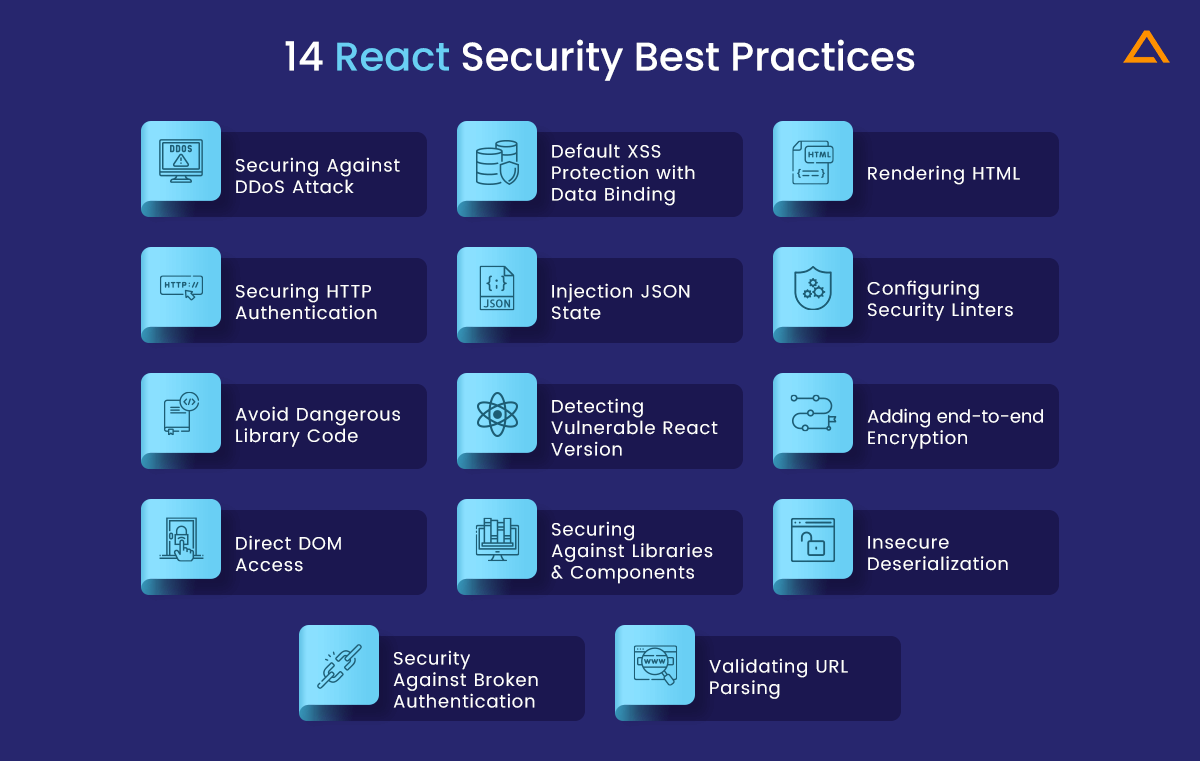
Securing Against DDoS Attack
Typically, this type of security vulnerability occurs when the program has some flaws in concealing the IPs of services or when the app isn’t secure enough.
Solution:
- Rate limits on APIs: You can limit the number of requests from a specific source to a specific IP. Axios has a complete package named Axios-rate-limit for limiting the rate of APIs
- You can use the API to add app-level restrictions
- Always make calls from the server, not from the client
- Add some validation to the app layer to make it safer
Default XSS Protection with Data Binding
To place data in your elements, you can utilize the JSX data-binding syntax { }. While utilizing default data binding with curly brackets { }, React will automatically escape values to defend against XSS attacks. It’s important to note that this protection only applies to text content, not HTML properties.
Solution:
Use this:
<div>{data}</div>
Avoid dynamic attributes values without custom validation
Don’t use this:
<form action={data}>…
You can also use reactjs content security policies as the last line of defence against XSS. If all other XSS prevention fails, CSP allows developers to control various things, such as loading external scripts and executing inline scripts. To deploy CSP, developers need to include an HTTP response header called Content-Security-Policy with the value carrying the policy.
default-src 'self'; script-src 'self'; object-src 'none'; frame-src 'none'; base-uri 'none';
Rendering HTML
Using dangerouslySetInnerHTML, you can directly enter HTML into a displayed DOM node. Any text that is introduced in this manner must be sanitized first. Before putting any values into the dangerouslySetInnerHTML prop, use a sanitization library like dompurify.
Solution:
Use dompurify when inserting HTML into DOM.
Import purify from “dompurify”;
< div dangerouslySetInnerHTML={{ __html:purify.sanitize (data)}}/ >
Securing HTTP Authentication
Suppose your app offers an authentication function that allows users to log in or create accounts. In that case, you should ensure it’s safe because client-side authentication and authorization are often vulnerable to security issues that can compromise the app’s protocols.
Solution:
Most prominently, you would’ve used one of the following methods to add authentication:
Injection JSON State
JSON data is frequently sent in conjunction with server-side rendered React pages. To avoid injection attacks, make sure to escape HTML significant values. To avoid injection attacks, always escape characters with a beginning value.
window.__PRELOADED_STATE__ = ${JSON.stringify(preloadedState).replace( /</g, '\\u003c')}
Configuring Security Linters
Install Linter settings and plugins to detect and advise on security vulnerabilities in your code automatically. Using a library like husky, set up a pre-commit hook that fails if security-related Linter concerns are identified. When new vulnerabilities in the version you’re using are discovered, you can use synk to update to a new version automatically. To discover security vulnerabilities in a codebase, use the ESLint React security config.
Avoid Dangerous Library Code
The library code is routinely used to perform potentially dangerous actions, such as directly inserting HTML into the DOM. Review library code or use linters to find hazardous uses of React’s security mechanisms.
Also Read: – Top React Chart Libraries to Visualize your Data in 2024
Solutions:
Avoid libraries with a history of putting people in danger. SetInnerHTML, innerHTML, unvalidated URLs, and other unsafe patterns exist. Use security Linters on your node modules folder to detect harmful patterns in your library code.
Detecting vulnerable React Version
Because the React library has had a few high-severity vulnerabilities in the past, it’s a good idea to stay up to date with the most recent version. To prevent vulnerable versions, use npm outdated to see the newest versions of reacting and react-dom.
Adding end-to-end Encryption
The global average cost of a data breach, according to Statista, is $4.24 million. In most situations, the data breach is triggered by online apps failing to offer End-to-End encryption. As an engineering lead, you should secure the security of your react application by implementing end-to-end encryption. This encryption is used by your application to protect the communication between its users. Transferring private information to third parties is not a good idea.
End-to-end encryption is a time-saving feature:
- Encrypt data with public and private keys despite the complex structure
- Use asymmetric algorithms such as RSA to encrypt the primary key
- The symmetric AES technique was used to encrypt the transactions
- Encryption libraries like encrptjs and cryptojs are beneficial for server-side and client-side encryption
Direct DOM Access
It’s preferable to avoid directly inserting material into DOM elements using the DOM. If you must inject HTML, sanitize it using dangerouslySetInnerHTML and dompurify before doing so.
Soultion:
Import purify from “dompurify”;
< div dangerouslySetInnerHTML={{ __html:purify.sanitize (data)}}/ >
To directly inject content using innerHTML and comparable attributes or methods, avoid utilizing refs and findDomNode() to access rendered DOM nodes.
Don’t do this:
this.myRef.current.innerHTML = attackerControlledValue;Securing Against Libraries & Components
There is always a risk associated when using third-party libraries, modules, or APIs in your React app. Sure, they aid in the speedy creation of features, but who knows if their own set of security problems could cause your react app to crash.
Solution:
- Attempt to upgrade these libraries manually to the most recent secure and stable version
- Older versions of the react secure component should be patched with newer versions
- Before incorporating any libraries into your project, make a quick check for security flaws. While you’re looking for flaws, see whether any potential fixes are offered
Also Read: – Top React Native UI Components Libraries
Insecure Deserialization
If you recall our conversation on how to defend your react web application from XXE, you’ll recall that data serialization leads to specific react js security issues. However, the deserialization of objects injected by an authorized user or an attacker results in the remote execution of programs, which might cause an application’s behaviour to change.
Solutions:
- Conduct integrity checks to ensure that no malicious objects are injected
- Think about code segregation
- Before the unauthorized construction of code objects, impose rigorous deserialization limitations
Security Against Broken Authentication
Invalid authentication processes, incorrect implementation, and failing authentication functionalities can lead to credential compromise or exploitation in your web application. Automated brute force assaults or, in some situations, authentication failure, may result from credential stuffing.
Solutions:
- Multi-factor authentication should be implemented
- Recover the passwords
- Connect the APIs
- Secure access will be provided via cloud-native authentication technologies
Validating URL Parsing
When linking material with the anchor tag a> and URLs, be wary of attackers introducing payloads that are prefixed with JavaScript. Always validate the URL using the HTTP or HTTPS protocols to avoid malicious script insertion via URL.
function validateURL(url) {
const parsed = new URL(url)
return ['https:', 'http:'].includes(parsed.protocol)
}
<a href={validateURL(url) ? url : ''}>This is a link! </a>
The allowlist/blocklist function is another method for protecting your React application. Allowlist refers to a list of all the safe and accessible URLs. While a blocklist is a list of all potential risks that will be blocked if access is requested, a whitelist is a list of all potential dangers that will not be blocked. Because keeping track of all potentially hazardous connections can be challenging, it’s a good idea to allow only known sites and block everything else. Broken authentication, XSS, arbitrary code execution, and SQL Injection can all be prevented via URL validation.
The allowlist/blocklist function is another method for protecting your React application. Allowlist refers to a list of all the safe and accessible URLs. While a blocklist is a list of all potential risks that will be blocked if access is requested, a whitelist is a list of all potential dangers that will not be blocked. Because keeping track of all potentially hazardous connections can be challenging, it’s a good idea to allow only known sites and block everything else. Broken authentication, XSS, arbitrary code execution, and SQL Injection can all be prevented via URL validation.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites.
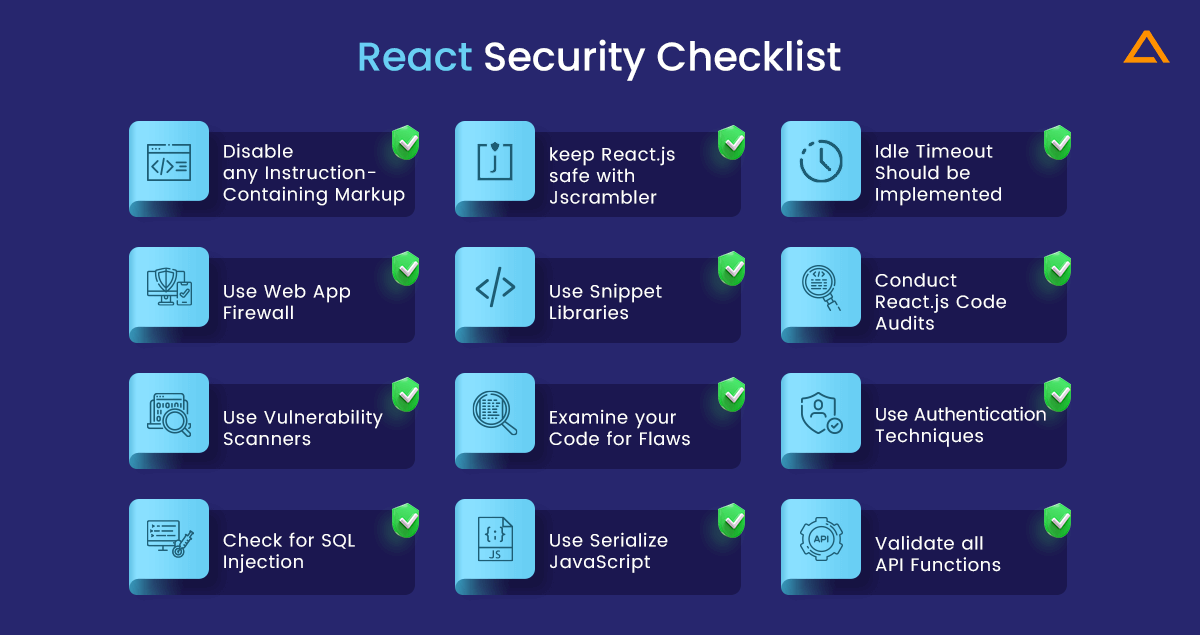
React Security Checklist
- Disable any instruction-containing markup
- With Jscrambler, you can keep reactjs safe
- Idle timeout should be implemented
- Use snippet libraries such as ES7 React, Redux, and others
- Conduct Reactjs code audits, filtering all app inputs with whitelists
- Use vulnerability scanners, a web app firewall, and serialize javascript NPM packages to improve app security
- Examine your code for flaws and potentially hazardous code, such as URLs and HTML components
- Appropriate authentication techniques should be used
- Check for SQL injection in the database
- Validate all API functions according to API Schema
Wrapping Up!
Many global corporations look for top React development companies to construct their web solutions. I hope this article has provided you with a clear picture of the most common React security vulnerabilities and the various checklists developers can use to solve them. Developers should be aware of the importance of application security for both the business and the users. You’ll have fewer typing options and more explicit code if you use React security practices. This list of React security best practices will guide you in the right direction and, in the long run, eliminate any future development issues.



 Say
Say