Quick Summary:
The reliance on applications is growing by the day in this digital environment. Everything we do in our daily lives, from getting up in the morning to ordering breakfast, relies on technology. Android and iOS are two popular mobile operating systems. This blog will discuss the security vulnerabilities that both operating systems have. It will compare Android vs. iOS based on various security factors, including vulnerabilities, privacy concerns, and marketplace security. It also provides security suggestions for both iOS and Android.
Mobile gadgets have become an integral part of our daily life. Because mobile apps have access to so much of our data, selecting a secure platform for app development is critical. It’s vital to use a secure platform to protect against assaults like SQL injection, CSRF, and Cross-site scripting. Because cyber attackers are starting to pay attention to mobile platforms, they should be the focus of security. The following statistics back up this claim. According to the report,
In 2021, the mobile platform will account for 30% of all cyber vulnerabilities & zero vulnerabilities.
Exploited, zero-day vulnerabilities attacks against mobile points increased by 446 %.
In addition, 75 percent of phishing sites are targeted at mobile devices.
Whether Android or iOS is more secure has raged for decades. The outcome of this discussion is independent of either platform’s popularity. According to StatCounter, Android devices are considered unsecured, with 71.43 percent of the market versus 27.85 percent for iOS.
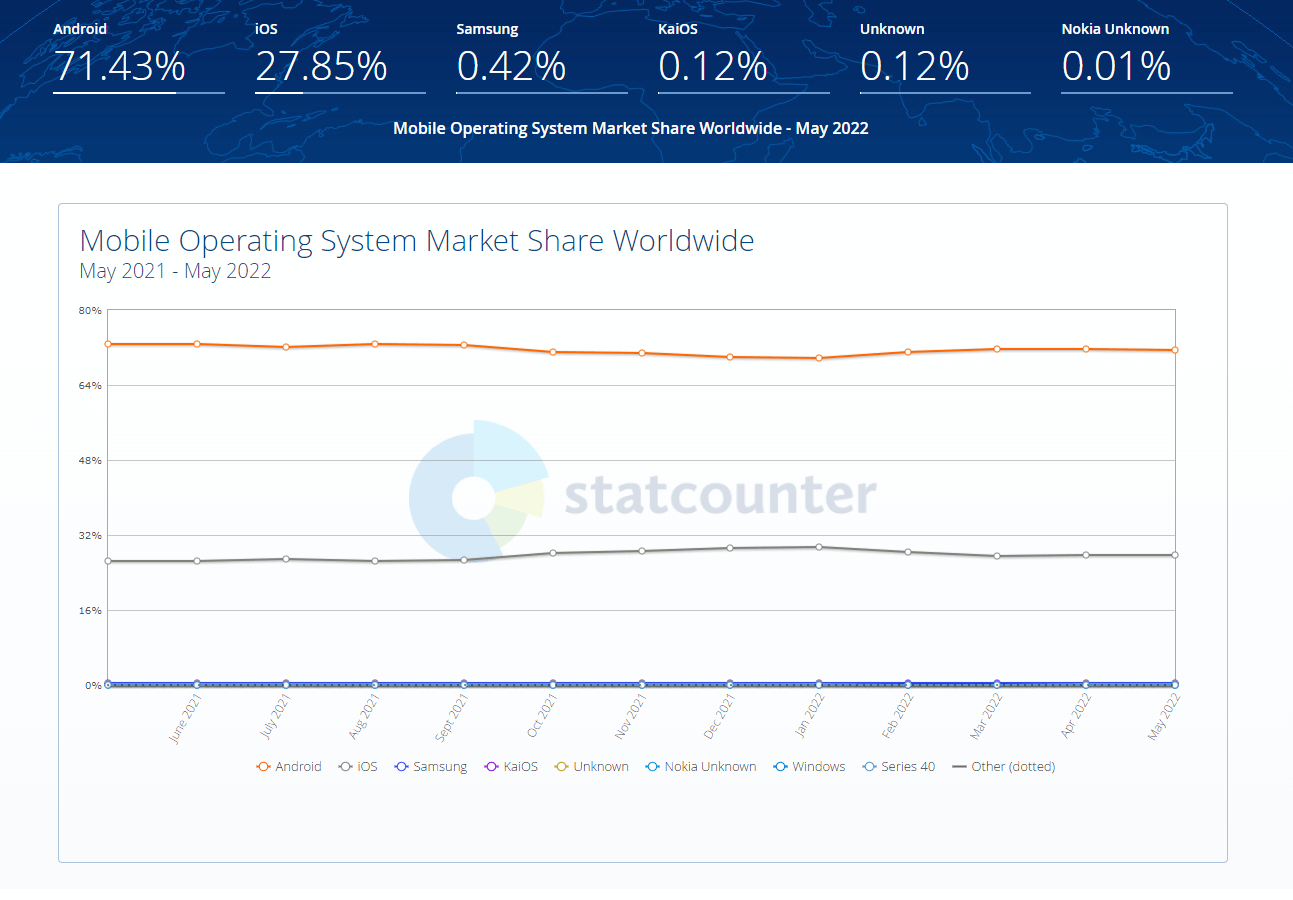
Companies are focusing on developing apps due to the pandemic, which has increased the number of opportunities for mobile apps, necessitating the need for mobile app security. Consider the security differences between Android and iOS.
Why iOS is considered to be more secure than Android
When compared to Android devices, iOS devices are unquestionably the safest. Because iOS is a closed system, many people consider it safer. When it comes to distributing code to developers, Apple is highly stringent. Owners of iPhones and iPads running iOS cannot customize their devices. This will also put cyber criminals at a disadvantage, as the closed source structure of iOS makes it difficult for hackers to uncover exploitable flaws.
Because Android is open-source, it allows developers to customize their handsets as they see fit. Giving this independence, however, exposes the system to weaknesses. When the update is applied to the operating system, however, the previously present vulnerability in the script enables hackers to exploit it.
Another factor for Android’s security vulnerabilities is its widespread use. Android is an attractive target for hackers due to its popularity. As a result, Android is vulnerable to various cyber threats, including malware and viruses.
Security Features and Limitations of iOS
Below are some of the cybersecurity advantages and disadvantages of iOS:
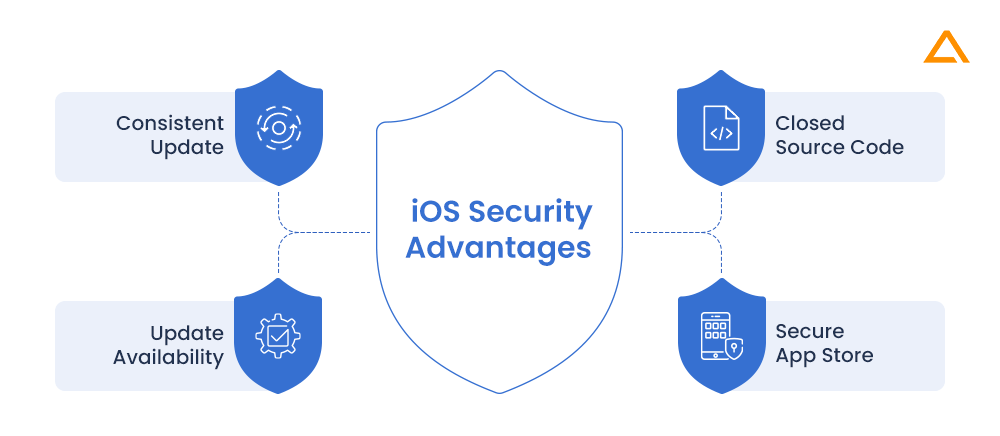
According to the findings, iOS 5 is the most robust iOS upgrade. Only three severe flaws were discovered in this upgrade throughout its release year. As a result, it is the most secure update on the list. While not every version has been as confident as others, the following are some general iOS security advantages:
-
Consistent Update
iOS updates are released regularly, indicating that security flaws are constantly patched.
-
Closed-source code
It is difficult to detect vulnerabilities due to the proprietary software nature of the software.
-
Update availability
Every iOS device released recently gets access to the most recent upgrades.
-
Secure App Store
On Android smartphones, anyone may publish an app. However, Apple only has one app store where they can monitor the apps’ quality and deny them
Also Read: iOS App Development Best Practices
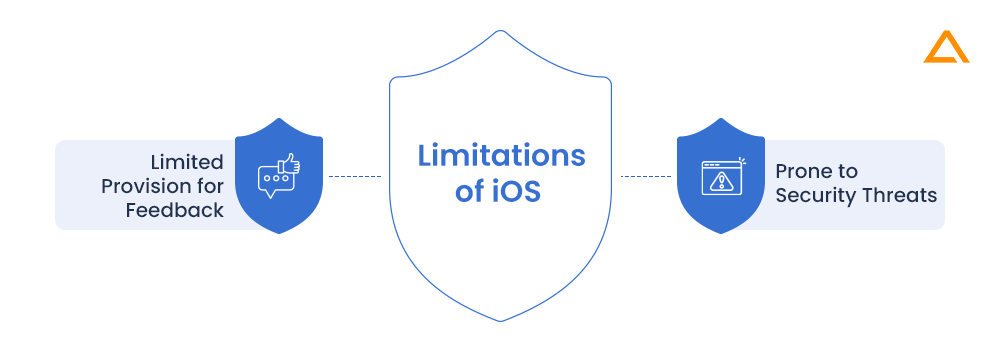
Let’s check in on the limitations of iOS now that we’ve seen the features:
-
Limited provision for feedback
Due to the closed source code nature of iOS, it is difficult for the users, developers, as well as test engineers to provide feedback of detected security flaws.
-
Prone to security threats
Although, iOS is more secure compared to Android, it is still vulnerable to the security flaws such as memory corruption and execution code overflows.
Planning to Hire iOS Developers?
Our skilled team of iOS developers at Aglowid can develop scalable & feature-rich iOS apps for your business niche
Security Features and Limitations of Android
The most popular mobile operating system on the planet is Android. And the most recent version of Android has achieved the highest security rating. The current emphasis on security by Android is beginning to bear fruit.
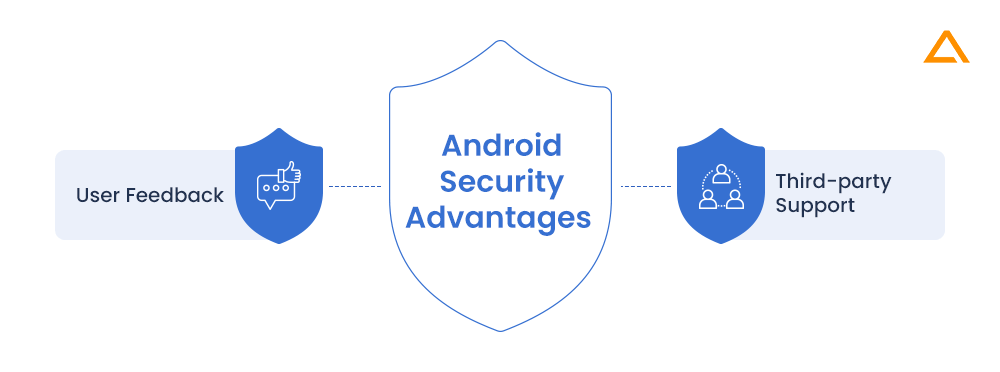
Some of the most important security features for Android are listed here:
-
User Feedback
Android has a big user base. A diverse group of people utilizes it all around the world. It’s used to detect and report Android vulnerabilities.
-
Third-party support
Android makes use of a variety of third-party security apps.
Now that you’re familiar with the benefits of Android, let’s take a look at their limitations:
-
Open-Source Code
Being Open-source in nature, Android is targeted by various malicious users who can easily exploit security vulnerabilities and zero-day vulnerabilities.
-
Limitation in Updates
Most Android Devices guarantee only 2 years of updates. And in many cases, the company’s updates are released so late that the validity of devices getting updates is long gone.
-
Loosely Regulated Marketplace
Unlike iOS, Android has various marketplace available, each having different standards of accepting applications. This makes it easy for attackers to publish the malicious app.
Also Read: – Android App Development Libraries
Android vs. iOS: Vulnerabilities
Let’s look at the security flaws in Android and iOS mobile apps in this part.
Mobile app security is a major topic in the Android ecosystem. It is more vulnerable to data breaches than iOS because of its open-source nature. Due to the fragmentation of Android, newer version updates take longer to reach all clients. Let’s look at some of the most typical Android cyber security vulnerabilities:
-
Android Fragmentation Risk
One of Android’s most serious security issues while developing safe solutions is fragmentation. It might be challenging for Android phones to design an application that works across all operating system versions. In addition, consumers may not always upgrade their mobile phones, leading to inconsistency. Many security patches may fail to reach clients as a result of this. However, it is worth emphasizing that the most vulnerable mobile devices are those that have not been updated.
-
Tailoring the Operating system
Tailoring the operating system is one of the most serious security issues that Android users face. As a result of the security vulnerability, modifying an operating system may result in significant problems. A more user-friendly operating system can be tailored. However, if you tend to change the operating system by incorporating third-party layers and launchers, you may want to reconsider.
-
Unauthorized Source
Because Android is open-source, anyone can create dangerous apps and deploy them as legitimate apps. Because Android apps aren’t restricted to Google Play, they can be found on third-party app stores (though this isn’t permitted). Users download apps from unauthorized websites to avoid paying for them.
-
Application Permission
The majority of Android users have no idea what permissions an app requires. People also don’t hesitate to push the Accept button. So, what makes this risky? By granting certain permissions, you allow the app to access sensitive data on your device. Consequently, when it comes to developing Android apps, developers should strive to create apps that require the least amount of permission. It’s also critical to raise user awareness about the consent they’re giving.
On the other hand, Apple controls the iOS mobile operating system, giving it influence over the apps in the Apple App Store. Due to these limitations, they can provide specific out-of-the-box security solutions. Let’s look at some of the security flaws in iOS apps:
-
Mobile Remote Access Torjans (mRATs)
This remote access trojan jailbreaks the devices, eliminating all built-in security mechanisms and installing malicious software that allows the attacker to take control of the victims’ machines. There is no single antivirus solution that can guarantee protection from such threats. When the jailbreak may be readily concealed with the support of mobile device management, the situation becomes even more problematic. There is a requirement for a technique to detect if the device is jailbroken or not while the surveillance activity is taking place. There are other places on the internet, such as xCon, where you may learn how to circumvent MDM detections.
-
Man in the middle attack (MITM)
Mobile devices have become more attractive targets for attackers in both personal and professional lives. Because all communication takes place on the attacker’s network, they can listen in on or intercept your conversations. When you connect your device to an insecure wifi network, you risk becoming a attack victim.
Unfortunately, consumers can only see the alert and warning on PCs and desktops, as the mobile screen is too small to validate the URL in the browser.
Using a VPN to shield and secure your communication is the best possible method to defend yourself from these attacks. The VPN should only be active for the best user experience when you need it.
-
Zero-day vulnerabilities
Zero-day vulnerabilities are just discovered and are yet to be made public. There is a rush to expose the vulnerabilities, and vulnerabilities researchers earn up to $500K for finding these vulnerabilities.
These vulnerabilities are widely used to silently install attacks like mRATs on a device that uses a remote exploitation technique. With the help of using remote exploitation techniques, these vulnerabilities lead to the installation of attacks such as mRATs on a device. Once on the device, the attacker may be able to steal passwords, corporate data, emails, and keylog all keyboard and screen activity (screen scraping). They might even use the phone as a botnet to steal contacts or text messages by listening in on chats and meetings through the microphone (SMS texts).
AV systems can’t guard against new assaults because they rely on known attack patterns to detect them. To locate and limit the effect of zero-day mobile exploits, organizations require a system that can detect any unusual behavior from an app, a device, or a network.
-
Malicious Certificate
An intruder can load an application with malicious programs using a counterfeit certificate, which means the application won’t have to go through Apple’s verification process and can be downloaded directly to the device.
Developers and enterprise certificates are two different types of third-party certificates Apple offers. Developer certificates enable developers to test applications before moving them to the production phase of the development process. IOS checks the trustworthy certificates behind the scenes before approving an application. On the other hand, Enterprise certification permits a company to build its unique market.
For example, a malicious program can be created, and an infection certificate can be obtained. They can then persuade the victim to download their seemingly harmless app, infecting their smartphones without their knowledge.
Also Read: iOS App Performance Optimization
Android vs. iOS: Privacy
Most smartphone apps request personal information, which, if misused, might compromise your privacy. When comparing the security of Android and iOS smartphones, it was discovered that iOS is more secure. According to the Symantec analysis, Android apps, in comparison to their iOS counterparts, request more permissions. Another intriguing data is that Android requests 89 percent of potentially dangerous permissions, whereas iOS requests only 39 percent. According to artechica, Android collects roughly 1.3TB of data in 12 hours in the United States alone, while iOS collects up to 5.8GB. To work effectively, applications require permission from users. However, a vigilant eye on your grant permissions is a good idea.
Android vs. iOS: Marketplace Security
Compared to the Apple store, you may choose from a wider range of apps in the Google app store. This has many advantages, but it can also be a disadvantage. Even though Android is making substantial modifications to prevent malware-infected apps from reaching the market, malware is still present in some high-ranking apps. If the software is downloaded from a third-party app store, the situation becomes much more complicated.
Looking for Android App Developers?
Hire Professional Android App Developers from Aglowid to develop highly scalable mobile app
Android security tips
Although the level of security provided by Android varies by device, there are always actions you can do to secure your personal information.
-
Monitor app permission
Because programs frequently request permission to conduct specific tasks, you should check your privacy options now to ensure that applications do not have any unneeded rights.
-
Use antivirus software
Antivirus software is recommended for protecting your phone from many types of cyber-attacks.
-
Always update
As time passes, any secure operating system becomes more vulnerable to cyberattacks. To maintain a secure layer against cyber threats, it is essential to update as needed.
-
Use safe browsing
When using Android, it is suggested that you utilize Chrome and enable safe browsing mode to maximize your security.
-
Use passcode
Your phone must have a unique passcode to access it to keep your important data secure.
Also Read: – Best Android Development Tools (ADT) List to Know in 2025
iOS security tips
Even though Apple takes numerous precautions to protect data, it isn’t always sufficient. Users must be alert as well. To protect your iPhone, follow these guidelines.
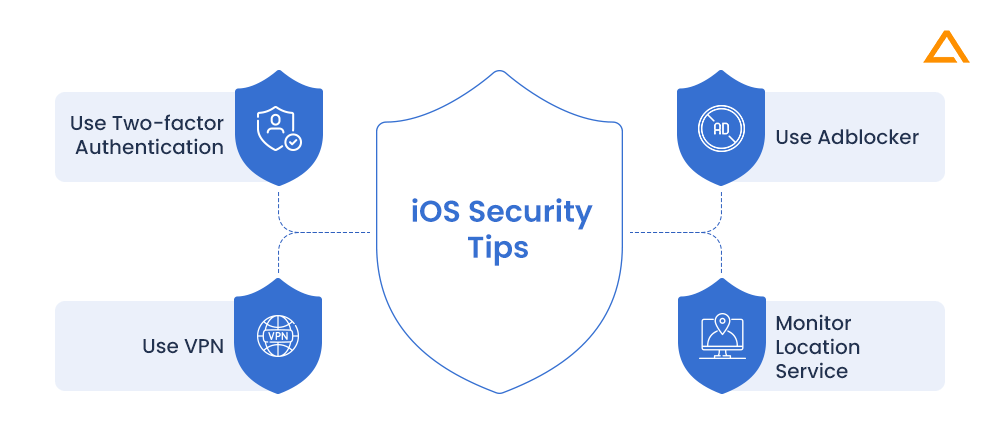
-
Use Two-factor authentication
Enabling two-factor authentication for apps with highly sensitive data adds an extra degree of security. This implies that even if your credentials are stolen, your sensitive data will remain private.
-
Use VPN
A VPN (a virtual private network) might help you disguise your Ip and other sensitive information when you use the internet. You can browse the internet safely in this manner.
-
Monitor location service
Certain apps will push you to leave location tracking turned on indefinitely. You shouldn’t do this if you don’t trust an app. Allow location tracking only once if you must, forcing the program to seek permission every time it wishes to learn your location.
-
Use adblocker
Among the most popular ways for malware to spread is through advertisements. Using an iOS ad blocker to secure your phone and improve your browsing experience is essential.
Wrapping up!
Because cybercriminals quickly advance cyberattacks, the threat landscape is the same whether you use iOS or Android. It’s understandable to have a debate regarding Android vs. iOS security. On the other hand, the growing threat is unavoidable.
The use of social engineering in these attacks is very alarming. Because anyone can be a victim of cyber-attacks thanks to well-crafted phishing attempts, practicing cyber hygiene and being attentive is the best way to ensure security.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites.
Also Check:




 Say
Say