Quick Summary: The key objective of the SDLC lifecycle in 2021 should be mobile app security. Cybersecurity breaches and attacks are becoming more common in this digital age. Establishing trust is crucial in today’s age of technology and computers. Password protection, Asymmetric Keys, End-to-End encryption, approved certificate, and other ways can all be used to build confidence.
Over the last few years, mobile apps have become an integral part of almost everyone’s life. Whether it’s booking tickets, ordering food, paying bills, buying commodities, or banking. Our lives are dependent on mobile applications. Mobile devices are used for practically all activities, including watching the news, checking emails, instant messaging, making online purchases, and doing financial transactions. Businesses may obtain useful information about users using these apps, such as their location, usage statistics, phone number, likes, dislikes, and other relevant metrics, which can help them make accurate decisions to improve their services. The data on these mobile devices can be damaging to the user if it falls into the wrong hands. First, let’s understand what is mobile app security
What Is Mobile App Security?
Mobile App Security Testing focuses on the security posture of mobile apps on various platforms like Android, iOS, Windows. This covers applications that run on both Mobile and Tablet. It involves assessing applications for security issues in the context of the platforms at which they are designed to run, the framework that is developed with, and the anticipated set of users.
Mobile applications are a crucial part of a business online presence and many businesses rely on mobile apps to connect with users from around the world. An application breach can be related to many issues like storing user’s data without encryption on the local database, session token change, and much more.
Due to the current situation, the reliance on the application has grown even more due to the remote work. According to Forrester’s state of application security report 2021, web applications are the common form of external attack.
Impact of Weak Mobile App Security: Key Areas
Now that we understand what is mobile app security, let’s see how it affects the various areas of our lives. Following are common areas of impact.
- Customer Information
- Financial Information
- Cloning
- Revenue Loss
- Brand Confidence
Customers trust the organizations to test their applications according to security measures before launching the application in the market. However, the following stats reveal shocking facts.
These mobile app security statistics are enough to give motivation to the attacker for exploiting loopholes available in the applications. Attackers can exploit any or all the areas from unsecured codes. Let’s take a deeper look into how mobile app security affects the described areas.
Customer Information
An attacker can gain login credentials to any device or website, for example, Email, Banking, Social Networking, etc. On 4th January 2021, Telecommunication giant T-Mobile announced it has been hacked. Although any personal or financial data was not accessed “customer proprietary network information (CPNI) as defined by the Federal Communications Commission (FCC) rules was accessed. The CPNI accessed may have included the phone number, a number of lines subscribed to on [user] account and, in some cases, call-related information collected as part of the normal operation of [user] wireless service.”
Financial information
In cases where a one-time password is not required, hackers can obtain credit and debit card data and use them to perform bank transactions. Kaspersky Lab researchers uncovered a new variant of the banking Trojan known as Ginp, which is capable of stealing user credentials and credit card information from a user’s device. It can affect banking processes thanks to its ability to handle the device’s SMS feature. Its code was discovered to be influencing 24 Spanish bank apps.
Cloning
Hackers obtain access to the app’s codebase to build unlawful clones or simply steal the company’s intellectual property. The more popular an app becomes, the more copies it will draw on app marketplaces. For example, Fortnite and PUBG Mobile became popular and were not available on Google Play, but due to their high popularity, many clones quickly became available, to the point that Google had to notify consumers that the official Fortnite was not available on Google Play.
Revenue Loss
Premium features of an application are a source of revenue for the owner of apps, especially utility and games. It’s possible to access the premium feature of an application by exploiting the loopholes available in the application. In 2016, the mobile security firm Bluebox disclosed how hackers exploited security flaws in popular applications Hulu and Tinder to gain access to premium services and steal money from their owners. Hulu’s monthly subscriptions for their OTT streaming service were $7.99 per month at the time.
Brand Confidence
It’s not just losing sensitive data of customers that puts a toll on the brand image. The loss can come from both misuses of information as well as lawsuits from affected parties. The impact of security drills can be positive as well as negative. The positive thing about doing security drills is that customers stay loyal and trust the brand. The negative impact can be losing the customer’s confidence forever. Thus, the rationale for business apps should be considered according to the aspect.
Mobile App Security Threat
Before diving into the types of mobile app security theft let’s first understand the concept of mobile app security threat. The mobile app security threat is attacks that are intended to compromise or steal data from mobile devices such as smartphones and tablets. These threats are often malware, spyware allowing attackers to access the device. They can steal login information and create spoofed identities. These attacks can also lead to data leaks.
Types of Mobile App Security Threat
Mobile device attacks are of various types. But they are broadly categorized into 4 parts
- App-based mobile threat
- Web-based mobile threat
- Network threats
- Physical threat
App-based mobile threat
Applications are often the entry point of mobile device vulnerabilities. These attacks can occur when users download the malicious application or grant permission to access device data without checking if it is required or not. These small things often work as an entry point for attackers. It can be avoided by having just a little awareness from the user side.
Web-based mobile threat
A web-based mobile attack is usually done with phishing or spoofing. Attackers will send an email, text, msg, or link which will look like it’s from the trusted source but the message will be from the malicious source and any link or attachment that contains will be malicious. When users click the link or download the attachment the attacker can gain access to the device and can spoof the identity or steal credentials.
Network Threats
This type of mobile attack occurs when an attacker targets unsecured or free-to-use Wifi connections. In some cases, the intruder can also set up a fake free-to-use wifi network (Network spoofing) in an attempt to trick users. Once, the user connects on the spoofed network the network will ask for the user name and password, providing an opportunity to the attacker to compromise the devices and credentials.
Physical Threats
Lost, stolen, and unattended devices can open up to the user to a new array of mobile app security issues. If you don’t have a strong password, PIN, or biometric authentication, and use unencrypted apps and services. It’s a high chance that you can be hacked easily, considering the threat landscape.
Top 10 Mobile App Security Testing Checklist: OWASP
Based upon survey and feedback collected from the community, The Open Web Application Security Project foundation gave OWASP mobile security risks. Let’s explore the OWASP Top 10 Mobile App Security risk along with the solutions.
| RISK | DESCRIPTION | SOLUTION |
| Improper Platform Usage |
This threat refers to the misuse of any platform feature of android or iOS. Each of these platforms is expected to follow certain development guidelines for security purposes. Example: Misuse of iOS Touch ID feature, Incorrect use of iOS Keychain, exploitation of Android Intents |
This OWASP mobile security risk is something that must be addressed on the server side. Using the platform development guidelines, securing coding practice, and applying the right configuration setting on the server-side might help to minimize the risk. Other steps that might help are restricting apps from communicating, limited access, restrictive file permissions. |
| Insecure Data Storage |
Your mobile device may get lost or stolen and can land in the hand of the malicious attacker. Or sensitive data can be extracted by the piece of malware or the attacker can exploit the vulnerabilities that can result in a data leak and access to sensitive data. Example: Jailbreaking or rooting the device |
Create a threat model to understand what information is processed by the application and how API handles the data. Assess whether applied encryption is effective and protect the encryption keys. Implement technologies to protect against tampering by obfuscation, buffer overflow, avoid caching/ storing the data, deploy sound |
| Insecure Communication |
Mobile apps exchange data in the client-server model, so it must be transmitted over the device’s network and internet securely with the help of encryption. But if the data travels unencrypted in clear text form, anyone monitoring the network can capture all the information being sent. This traffic can be intercepted by proxies, cell towers, or by any other means that can compromise your network or device. Example: Identity Theft, Fraud, Reputational Damage |
To avoid data being misused or stolen it is advised to rely on the industry-standard encryption protocol and general practices. Set up SSL/TLS certificates from trusted certificate authorities (CA) to secure all communication channels. Alert the users if there is any invalid SSL/TLS certificate detected or if the certificate chain verification process fails. |
| Insecure Authentication |
Mobile apps must authenticate the user’s identity before allowing access. Authentication bypasses are frequently carried out by exploiting existing flaws, such as the mobile app’s backend server’s incorrect validation of service requests. Mobile apps must verify and retain user identity, particularly when transmitting sensitive data like banking information. Example: Hidden Service Request, Interface Reliance, Usability Requirments |
Avoid using local authentication methods. reassign this task to the server, and only download application data after successful authentication. Avoid using vulnerable authentication methods such as device identification. Avoid saving passwords locally, apply multi-factor authentication, and follow other general best practices |
| Insufficient Cryptography |
Cryptography and data security are strongly intertwined. One of the most prominent OWASP mobile vulnerabilities is the insecure or faulty use of cryptography. Mobile developers frequently use a hardcoded key in the source code to implement encryption and decryption on the device, leaving data security and cryptography exposed to attackers who can reverse-engineer the app. There is 2 situation in which system cryptography may get compromised.
Example: Improper Management of digital keys, Using custom or deprecated encryption protocol. |
Apply strong cryptographic standards as recommended by the National Institute of Standard and Technology (NIST) Avoid storing any sensitive data on the device |
| Insecure Authorization |
Not all users are created with equal rights and roles. Some of them can be regular users while some can be admin users. Improper authorization techniques don’t check not just who the user is, but also whether they’re authorized to access the resources they’re asking. Attackers can log in as genuine users and undertake privilege escalation attacks due to a failure to adequately enforce identification and the rights assigned to users. Example: Data theft, reputational damage |
Verify the authenticated user’s roles and privileges using strictly information from backend systems. Avoid relying on the mobile device’s role or permissions information. Backend code should verify independently that any incoming identifiers (the operations of a requested operation) associated with the request match and identity to the received identity |
| Client Code Quality |
This category is a catch-all for mobile customer problems in the field of defective code implementation in OWASP mobile security risks. An attacker can pass inputs created to a working call in an app to try to execute or to follow the behaviour of the app. It can lead to performance degradation, increased usage of memory, etc. Note that code errors must be fixed locally because the errors occur on the mobile client and differ from coding errors on the server. Several applications rely on third-party libraries to build their applications which often proves to be an entry point for the malicious invader. Example: Buffer Overflows, Insecure third-party libraries, Remote Code Execution. |
Maintain consistent and common coding patterns Write easy-to-read and well-documented code. Always confirm that the length of input buffer data doesn’t exceed the target buffer length when using buffers; Emphasize solving buffer overflows and memory leaks over “code quality issues” |
| Code Tampering |
Sometimes, app shops contain manipulated mobile apps versions. A modified application is an example in which a hacker changes the binary of the app to include malicious content, install a backdoor, etc. An attacker can re-sign these falsified applications to third-party app stores and publish the modified version. You can also send them directly to a victim through a phishing attack, to get them to download the app. Example: Unauthorized new features, ID theft, Fraud, reputation damage |
See for the build. prop the ro. build.tags=test keys that show the build of a developer or the non-official ROM Check for OTA certificates Check for several known rooted apks Check for SU binaries Attempt SU command directly
|
| Reverse Engineering |
Attackers can reverse the application and decompile it to analyze code. This is especially dangerous because the attacker can understand, inspect and modify the code to contain malicious functionalities or to convey unwanted ads. Using tools such as IDA Pro, Hopper, or other binary inspection tools, they can change the app once they understand how the app operates. Once the app is performed the way it wants, the application can be rebuilt and run. Example: String Table Analysis, Cross-function analysis, source code analysis |
The attacker must not be able to de-obfuscate code by using tools like IDA Pro and Hopper to prevent reverse engineering. A good obfuscator will have the following abilities: Narrow down the method or code that is unclear. Tune the degree of obfuscation to balance the performance impact Survive de-obfuscation from tools like IDA Pro and Hopper; Obfuscate String tables as well as methods. |
| Extraneous Functionality |
Sometimes developers may unintentionally or intentionally leave the backdoor or any malicious additional features that are not intended to be available, creating a security risk These mobile app security vulnerabilities can be exploited by an attacker from their systems without any participation from the user. They may examine the configuration files, analyze binary, etc to discover the functionalities in the back-end that can be used by cybercriminals to perform the attack. Example: Unauthorized new features, ID theft, Fraud, reputation damage |
Examine the app configuration to discover hidden switches Verify for test code Verify all API endpoints accessed to verify that these endpoints are well documented and publicly available. Examine all log statements. |
Android Mobile App Security Vulnerabilities
In the Android ecosystem, the problem of mobile app security is particularly concerning. Because it’s an open system, it’s more prone to data breaches on the operational level than iOS, which is closed, and all of its updates happen instantly. Because Android is so fragmented, new versions of the system are only slowly deployed to customers’ devices, stifling the overall security of the system. Let’s take a look at some of the android mobile app security problems.
Android Fragmentation Risks
When it comes to building a strong security solution, fragmentation is one of the main issues Android app development services encounter. Because Android apps come in multiple versions, it’s difficult for app developers to create a solution that works for all of them. Furthermore, consumers do not always upgrade their Android devices to the most recent version, causing certain security measures to fail. It’s also worth noting that Android devices that haven’t been updated are more vulnerable to infection and malware attacks.
Application Permissions
It’s not uncommon for Android app developers to be unaware of the various sorts and numbers of permissions that an app requires. Simultaneously, most users do not hesitate to press the “Accept” button when an app requests certain rights. So, what makes this a security risk? By providing certain permission to an app, users are authorizing the app to access private and sensitive data on their Android smartphone. As a result, when it comes to Android app development, programmers should strive to construct apps that require as minimal permissions as feasible. It’s also critical to raise awareness about app flaws and encourage users to be cautious.
Customizing the OS
Although it may appear unusual, altering the operating system is a significant security risk for Android applications. Customizing an operating system to make it more practical, comfortable, or user-friendly is fairly frequent. Some users, on the other hand, have a habit of modifying the OS by integrating launchers and customization layers. This leads to security flaws, which is why customizing the operating system is a major issue in Android application development.
Developing Apps from Unauthorized Source
Because Android apps aren’t restricted to the Google Play Store, they can be found in a variety of places – even if they aren’t allowed. Because of Android’s open-source nature, creating an Android app is a no-cost endeavour. As a result, anyone may easily design harmful programs and distribute them online. It’s also worth noting that consumers frequently use unapproved sites to obtain apps to avoid paying for the software they want. They then unwittingly download malicious programs that assault their devices and steal their information. As a result, the world of Android mobile app development is inherently dangerous.
iOS Mobile App Security Vulnerabilities
Apple’s iOS mobile operating system is tightly controlled by Apple, which gives it control over the apps available in the Apple app store. This control gives them control allows them to provide access to the out-of-the-box security under some user restrictions. Let’s take a look at some of the iOS mobile app security vulnerabilities
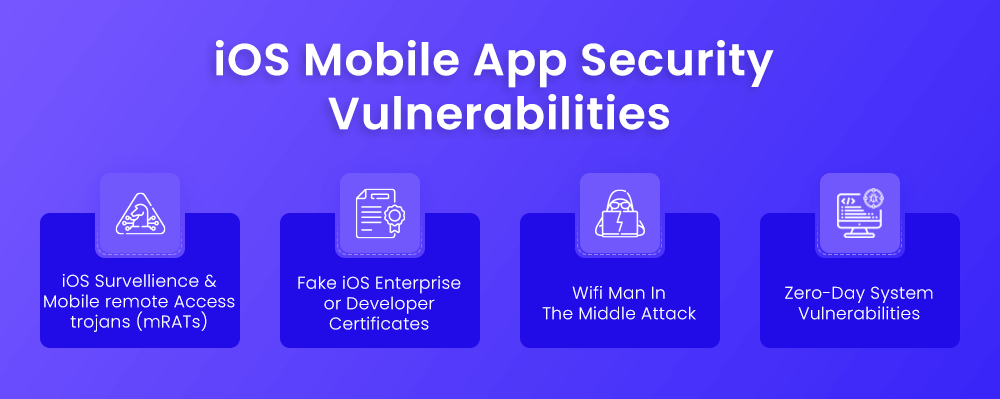
iOS Survellience and mobile remote Access trojans (mRATs)
These assaults jailbreak the smartphone, removing all built-in security features, and install mRAT software, allowing the attacker to take control of the phone. Any iOS software from any app store can be loaded on the device once it has been jailbroken. Not simply the apps that Apple has approved for their store. Cydia is a popular alternative app store, but there are many others. Users unwittingly download these apps and become infected with mRATs. There is no mobile antivirus that can defend you from these kinds of attacks. The issue is made worse by the fact that a jailbreak can be readily hidden from Mobile Device Management (MDM) solutions. Popular forums, such as xCon, for example, freely disclose strategies to avoid MDM detection. What’s needed is a mechanism to tell when a device has been jailbroken and the capacity to spot surveillance activity.
Fake iOS Enterprise or Developer Certificates
These attacks use distribution certificates to sideload an application with malware, which means it doesn’t go through the Apple App store validation process and can be downloaded straight on the device.
Apple provides 2 different kinds of third-party certificates, developer and enterprise. Developer certificates allow developers to test their apps before they are released to the public in the app store, while enterprise certificates allow businesses to create their exclusive app marketplace. Before allowing an app, iOS verifies that it is signed by a trusted certificate behind the scenes.
When an attacker can obtain a certificate for their virus (for example, by stealing or purchasing on the black market), problems arise. They can then persuade the user to download their supposedly innocent app, infecting their smartphone without their knowledge; because the program is accompanied by a certificate, it is validated and easy to install, bypassing any iOS restrictions.
Wifi Man In The Middle Attack
When a device connects to a rogue WiFi hotspot, a MitM attack happens. Because all communications run through the attacker-controlled network device, they can listen in on and even change the network’s communication.
MitM assaults have always been a worry for wireless devices, but with the widespread use of smartphones in both personal and professional lives, mobile devices have become far more appealing targets for this attack.
Unfortunately, the normal alert and warning indicators that people are accustomed to seeing on computers and laptops are far more modest on mobile devices. Because of the limited screen size on mobile devices, URLs are frequently hidden from users, who do not verify that the URL the browser is referring to is the correct one.
The best approach to protect yourself from these assaults is to use a VPN to encrypt and isolate your communications. To maximize the user experience, the VPN should be activated only when rogue hotspots and other dangerous factors are detected.
Zero-Day System Vulnerabilities
Zero-day vulnerabilities have been discovered but not yet made public. The rush to expose vulnerabilities is at full speed, with vulnerability researchers reportedly earning $500K each hole.
Using a remote exploitation technique, these vulnerabilities frequently lead to the silent installation of attacks such as mRATs on a device. Once on the device, the attacker may be able to steal passwords, company data, and emails, as well as record all keyboard and screen activity (keylogging) (screen scraping). They could also use the microphone to listen in on conversations and meetings, or they could use the phone as a botnet to steal contacts or text messages (SMS texts).
AV solutions, which rely on known attack patterns to detect attacks, are unable to protect against unknown attacks. Organizations need a solution that can identify any suspicious behavior from an app, a device, or the network to find and mitigate the impact of zero-day mobile exploits
Mobile App Security Checklist
The process of creating and delivering mobile apps differs significantly from that of traditional software development. Our mobile app security guidelines were developed by seasoned mobile app developers and testers to assist you in securing your apps for a better end-user experience.
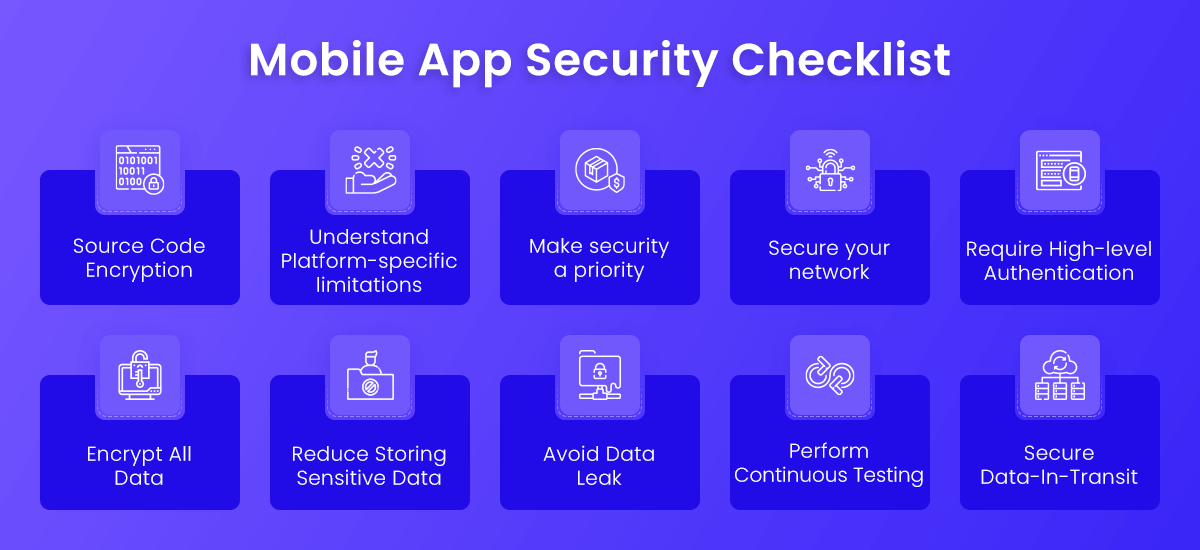
Source Code Encryption
Because the majority of code in a native mobile app is client-side, mobile malware can effortlessly trace flaws and exploits in the source code and design. Reverse-engineering is commonly used by attackers to repackage well-known programs into malicious ones. After that, they post the programs to third-party app stores to lure unwary consumers.
Threats like these might harm your company’s reputation. While developing an app, developers should be cautious and include tools to detect and address security flaws. Developers should make sure their apps are secure enough to withstand tampering and reverse engineering assaults. Encrypting the source code, which assures that it is unreadable, can be an excellent solution to protect your application against these assaults.
Understand Platform-specific limitations
When creating for different mobile operating systems, it’s best to first learn about the platform’s security features and restrictions, and then code accordingly. To properly control and distribute the program on your selected platforms, you need also consider distinct user case scenarios, encryption support, password support, and geo-location data support for the OS.
Make security a priority
Not just during the development process, but also throughout the planning phase, you must prioritize security. It’s important to note that native apps are more vulnerable than web-based programs. This is because the code will remain on the device once it has been downloaded. As a result, if you’re a developer, you should put effort into designing secure code.
Failure to test your code as a developer might result in major flaws. Hackers can quickly get information from your code if one line is incorrect. If you don’t want this to happen, you’ll need to write encrypted code that has been thoroughly tested for flaws.
Secure your network
Aside from safeguarding your code, you must also ensure the security of the servers that your mobile app connects to. You can protect your users’ data and prevent unauthorized access this way. Make that the APIs and the people who use the servers are authenticated. You can safeguard the data transmitted from the client to the server and database by doing so.
By employing an encrypted connection or connecting to a virtual private network, you can improve the security of your network. If neither of these methods is feasible, you may want to consider containerization as an alternative security approach. This technology allows you to create encrypted containers that are ideal for securing important documents.
Require High-level Authentication
Security breaches occur due to a lack of high-level authentication. App developers should make sure that only strong alphanumeric passwords are accepted. Furthermore, it is preferable to make it essential for users to change their passwords regularly. Biometric authentication using fingerprints or a retina scan can be used to increase the security of, particularly sensitive apps. To avoid security breaches, it is advised that users be encouraged to ensure authentication.
Encrypt All Data
Encrypting the code of your app isn’t enough. Data that is transmitted between your app and your server must also be encrypted. Encryption ensures that even if data is taken, hackers will be unable to use it. They can only see letters and numbers when they access it.
Reduce Storing Sensitive Data
To avoid hazards, make sure to reduce data storage to a bare minimum while creating your program. Never save confidential data on a mobile device or your server if at all possible. As a result, the risk levels will only rise. However, if you must save data, you must do so in encrypted data containers.
Avoid Data Leak
Users must consent to certain permissions before they can interact with your app. Regrettably, they don’t always follow these instructions, allowing unscrupulous businesses to profit from their personal information. You should implement advertising and data permissions responsibly to ensure that your app users’ data is not exposed to third-party vendors and hackers. Many app developers nowadays transfer user data to malicious vendors without the user’s awareness. You don’t want to be one of them.
Perform continuous Testing
Unfortunately, some programmers ignore this step. They are no longer concerned with testing as long as their apps are published on the App Store. If you want your app to stand out not only in terms of functionality but also in terms of security, you must test it before and after it is released. Your app’s code should be tested and reviewed regularly to guarantee that it is secure. Fix the flaws once they’ve been found.
Secure Data-In-Transit
The sensitive information sent from the client to the server must be safeguarded against data theft and privacy breaches. It is strongly advised to employ an SSL or VPN tunnel, which assures that user data is safeguarded by tight security procedures.
How To Improve Mobile App Security: Best Practices
Mobile app security best practices ensure that the app is risk-free and does not reveal the user’s personal information. Before the software is posted to an app store for public consumption, the developer must guarantee that all security tests are completed. Hackers are primarily interested in public-facing applications, which are frequently the only communication link between customers and the firm. The majority of public-facing applications are created to be compatible with practically every device on the market. This method, however, puts the program subject to attacks and manipulation. The most strict filtration mechanism must be maintained by developers.
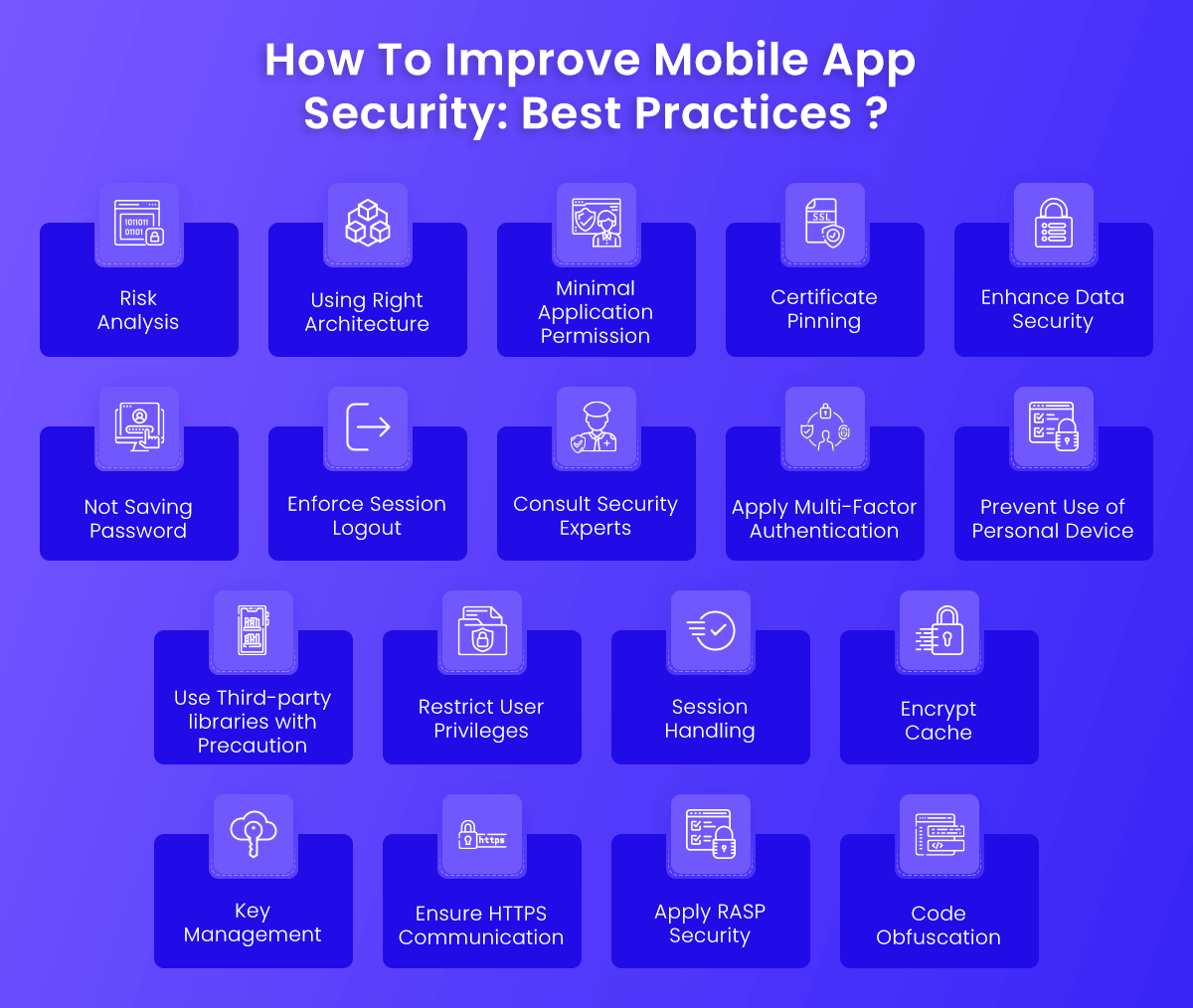
Risk Analysis
Developers might use a threat-modeling exercise to focus on specific alerts. The following are the most typical vulnerabilities faced by companies that rely on mobile apps to run their operations:
1. Data Leaks
Firewalls are prone to being breach by malicious users who can steal sensitive personal information such as credit card numbers, system passwords, and PINs. Once the firewall is breached malware can also be injected into the device.
2. Infrastructure Exposure
Sharing resources, such as a third-party API, may be required to communicate between mobile applications and the organization’s backend services. While integrating APIs, it is important to keep an eye on the process to ensure that user data is not compromised, as well as server-level security.
3. Scams
As long as mobile applications are used to conduct financial transactions, they will always be on the fraudster’s radar. When an application uses sensitive data, such as payment credentials, PINs, and passwords associated with apps and credit cards, etc., there is always a risk. On the prowl are criminals who use a variety of attack methods, including SMS grabbing via malware, script injection, and repackaging.
4. Regulations & guidelines
Legal and social frameworks must be adhered to for all applications to function properly. General Data Protection Regulation and Revised Payment Services Directive, for example, are just a few of the regulations that apply in Europe, while several other guidelines apply globally.
Using Right Architecture
The first thing to consider is whether the application is released on the commercial store or distributed through the organization’s distribution channel. The applications are released through private organization channels are less likely to get exploited. There are various methods available for mobile application security like application management through UEM and standalone situations.
There are three kinds of architectural options available for mobile app development. Native, Hybrid, and pure web-based. Each of these frameworks has there own pros and cons where one has to compromise either performance or security. For example. If the cached content is reduced and discarded more often to boost security but it can harm the performance of the application.
Along with this other factors should also be kept in mind before deciding the architecture. Another point to keep in mind is device-side and server-side checks. Often malicious actor tends to breach the device by messing with these applications on devices.
Minimal Application Permission
Apps with permissions have more freedom and power to perform their tasks more efficiently. As well as allowing for hacker attacks, they also make apps vulnerable to them. No application should ask for permissions outside of its functional area, unless necessary. They should not reuse existing libraries, but instead, create new ones that selectively seek permission.
Certificate Pinning
Certificate Pinning is a security procedure that protects applications connected to unsecured networks from Man in the Middle attacks. Although the technique has its advantages, it is not without its drawbacks as well. As traffic inspection becomes more difficult, it may not be able to support network detection and response tools. It’s also possible to run into compatibility issues. Some browsers do not support certificate pinning, making it difficult for hybrid applications to function properly
Enhance Data Security
Users should be able to avoid falling into the hands of hackers by establishing data security policies and standards. This can involve employing well-implemented data encryption while transferring information across devices, as well as firewalls and other security technologies as needed. You can use the Android and iOS guidelines as a guide.
Not Saving Password
Many programs ask users to remember passwords so that they don’t have to type them in every time they log in. These passwords can be collected in the event of a smartphone theft to acquire access to personal information. Similarly, if the password is saved in an unencrypted format, it is quite likely that it will be collected. To avoid this, developers should not save passwords on mobile devices. Instead, they should be saved on the app server so that users who are affected can modify them by logging in to the server even if their mobile device is gone.
Enforce Session Logout
Users frequently forget to log out of the website or application they are using. This can be dangerous if the app is a financial or payment app. As a result, for greater security, payment apps tend to stop a user’s session after a specific period of inactivity or on every logout. Even if their customers are highly educated, developers must enforce a session logout on all corporate and consumer-centric apps.
Consult Security Experts
No matter how experienced your in-house team is, an external point of view is always beneficial and can give a different perspective. There are several companies available in the market that can help identify the loopholes and reduce the chances of getting compromised. It should be encouraged by the companies that their application should get the security features of their apps assessed by the third-party service provider. \
Apply Multi-Factor Authentication
When a user logs into an app, Multi-Factor Authentication adds an extra layer of security. The multifactor authentication approach also protects against weak passwords that can be readily discovered by hackers, jeopardizing an app’s security. Multifactor authentication entails entering a secret code in addition to the password to log into a device or app. This code can be delivered via SMS, email, Google Authenticator, or biometrics. Hackers may be able to guess weak passwords if the software does not enforce multi-factor authentication.
Prevent Use of Personal Device
Many firms choose to ask their staff to bring their computers or smart devices for development to save the overhead expense of purchasing systems. This might expose the network to a slew of vulnerabilities gathered on an employee’s device. This is how malware and Trojans spread from one device to another. As a result, it’s critical to have a security strategy in place to avoid such behavior. Each device connected to an office network should be properly inspected with a firewall, antivirus, and anti-spam software before being allowed to connect, or it should not be allowed to connect at all.
Use Third-party libraries with precaution
Using third-party APIs can reduce the coding effort for developers and can provide ease of application development process. But this can be a risky option too as it opens door to various vulnerabilities. For example, The GNU C library had a security flaw that allows buffer overflow which could be remotely exploited by attackers resulting in a crashed device. It lasted for eight years before a fix was issued in 2016 by the open-source community that contributes to the GNU Project. As a result, to protect apps against assaults, developers should limit the use of a few libraries and design a policy for managing libraries.
Restrict User Privileges
The more rights a user is granted, the greater the risk of an app’s security being undermined. Hackers can cause unthinkable damage to an app if a user with a large number of rights is compromised. Similarly, an app should not request rights on a device for functions it does not require, such as reading SMS or accessing the DCIM folder.
Session Handling
On mobile devices, session handling takes substantially longer than on a desktop, increasing server overhead. Using a token instead of a device ID is a far more secure solution. Tokens can be revoked at any time and are more secure if a device is lost or stolen. Session expiration should also be considered by developers. Enabling remote data erasing for lost or stolen devices is another useful safety feature to retain in the app.
Encrypt Cache
The cache is a software component that stores data on the user’s device for a limited period. This prevents data retrieval from taking too long. If the data in the cache isn’t secured, hackers can readily access it. When a session ends, the app’s data is not always removed, and the cache is not always cleared. Hackers can utilize these cache files to access user data or the server if they fall into the wrong hands.
Key Management
Encryption requires good key management. Developers should avoid hard coding keys because they compromise the app’s security. The device is easily controllable if the key is stolen. Keys should be kept in a secure location and not on the device of the user. MD5 hash and SHA1 are two of the most commonly used cryptographic techniques for this. Developers should implement the most up-to-date encryption standards and APIs, such as 256-bit encryption with SHA-256 hashing.
Ensure HTTPS Communication
Encryption requires good key management. Developers should avoid hard coding keys because they compromise the app’s security. The device is easily controllable if the key is stolen. Keys should be kept in a secure location and not on the device of the user. MD5 hash and SHA1 are two of the most commonly used cryptographic techniques for this. Developers should implement the most up-to-date encryption standards and APIs, such as 256-bit encryption with SHA-256 hashing.
Apply RASP Security
It stands for runtime application self-protection, which defends an app against runtime attacks by increasing visibility into hidden flaws.
It’s a piece of security software that connects with the app or its runtime environment and constantly intercepts calls made to the app by potential attackers. The RASP layer monitors incoming traffic in real-time and prevents fake calls from being placed within the app. The RASP layer, which sits between the application and the server, inspects all incoming requests. For further information, see our RASP page.
Code Obfuscation
Code obfuscation is one of the most effective ways to secure an app from hackers. It is the act of writing difficult-to-understand code for hackers. This method has grown in popularity and is used to protect code from attacks. Obfuscators are programs that convert programming code into a format that humans can’t understand. Obfuscation of code includes:
- Encrypting some or entire code
- Removing meta-data layer which contains information about APIs and libraries used
- Renaming Class and Variables
Code obfuscation technique is not widely used in iOS as its libraries are closed. On the other hand, Android has open-source libraries. Hence, android developers need to obfuscate the code.
Free Tools for mobile application security
Mobile app creators should be aware that when their apps get more popular on consumer’s smartphones, hackers become more interested. They’ll use both human and automated methods to try and exploit vulnerabilities in apps or devices, as detailed above. As a result, it is critical for developers to properly test their apps before releasing them to app stores. Fortunately, there are a variety of free mobile app security testing tools – known as application security testing or AST tools – that can assist developers in guaranteeing security. AST tools simplify the testing process since manually examining codes against old dangers takes time, and keeping track of developing threats adds another layer of complexity.
Let’s take a look at the mobile app security scanning tools.

Android Debug Bridge(ADB) (Free)
ADB (Android Debug Bridge) is a command-line program that allows you to interface with your smartphone. The ADB command allows you to perform a variety of device tasks, including installation and debugging, as well as access to the UNIX shell, which you may use to run a variety of commands on the device. It’s a client-server application made up of three parts:
- A client sends commands to your development computer and runs it. An ADB command can be used to start the client from the command line.
- A daemon(adbd) On each device, it operates as a background process and is utilized to execute the command.
- A server Controls the flow of information between the client and the daemon. On the development machine, it operates in the background.
Features
- Enable ADB Device.
- File Transfer.
- Shell Commands Execution.
- Application Management.
- Capturing Screenshots.
- Recording Videos.
- Connecting Multiple Devices.
QARK (Free | GitHub: 2.5K)
QARK, which stands for “Quick Android Review Kit,” was created by LinkedIn. The name implies that it is beneficial for detecting security problems in the source code and APK of mobile apps on the Android platform. QARK is a static Android code quality tool that provides information regarding security vulnerabilities in Android apps as well as a clear and concise summary of the issues. QARK generates ADB (Android Debug Bridge) commands that can be used to verify the vulnerability that QARK has discovered.
- Involuntarily exported components
- Vulnerable Intent to interception or eavesdrop
- Improper x.509 certificate validation
- Data Leak Activities
- Outdated API version support, with a known vulnerability
- Weak / Improper use of cryptography
Features
- Open-source tool
- In-depth information about a security vulnerability
- Report Generating
- Report Potential Vulnerability and Fix
- Highlight version related issues
- Misconfiguration and security threat scan
OWASP Zed Proxy (Free)
The Zed Attack Proxy (ZAP) was created with ease of use in mind. It was originally designed to detect vulnerabilities in web apps, but it is now commonly used for mobile application security testing by all testers. ZAP makes it easy for testers to assess the security of mobile apps by allowing users to send false messages. This type of testing entails sending a malicious message with any request or file and assessing whether or not the mobile app is vulnerable to it.
Features
- Most Popular Open-Source Android Security Testing Tool.
- ZAP is actively maintained by volunteers
- Easy to Install
- It is an international community-based tool.
- Great for manual security testing
Devknox (Free)
Devknox is the world’s first mobile app security solution. This incredible mobile app security tool helps developers to spot and correct security flaws in their code as they write it in Android Studio. It not only checks for basic security flaws in the app but also gives developers real-time tips for promptly correcting these issues. We can compare it to autocorrect for security concerns. It also takes care of your security requirements, keeping you informed about worldwide security standards.
Features
- Real-time testing
- Interactive Dashboard
- Integrated Across-Platform
- Detailed Report
- Vulnerability Tracking
MOBSF (Free | GitHub: 9.4K)
Mobile Security Framework is a mobile app security framework for mobile applications (Android/iOS/Windows) that is automated, open-source, and all-in-one. It can analyze static, dynamic, and malware data. The OWASP MSTG recommends it for static analysis. Developers can conduct an effective and quick security examination of Android, iOS, and Windows mobile applications with this Android development tool. It accepts both binary (APK, IPA, APPX) and zip source code formats. It can test Android apps dynamically at runtime and has Web API fuzzing capabilities thanks to Cap Fuzz, a Web API scanner.
Features
- Makes Pipe integrationseamless
- Supports Static Analysis
- Supports Dynamic Analysis
- Supports all platforms
- Supports both Binary and Zip source code.
- Supports Web Services.
- Supports API
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites.
Wrapping Up
While developing mobile apps, app developers must be aware of the risks posed by cybersecurity attacks and data breaches. They will be able to protect both the apps and the data within them by adopting the above-mentioned mobile app security process. These mobile app security precautions are simple to put in place. App creators and developers must take a holistic approach to app development, taking into account all of the aspects that affect app security.
Also Check:



 Say
Say