Quick Summary: All tasks that introduce development teams to a safe software development life cycle are included in application security. Its ultimate purpose is to improve security practices by identifying, fixing, and, ideally, preventing security vulnerabilities in applications.
The App Development Lifecycle is incomplete without application security. In this quickly evolving digital economy, it should be the primary focus. App usage increased as a result of the pandemic.
The global average time spent every day was 4.2 hours, up to 30% compared to two years prior. – App Annie
As per Edgescan’s report, 50% of internal application vulnerabilities are classified as high or critical risks, while 32% of internet-facing vulnerabilities are classified as high or critical risks.
What is Application Security (AppSec or App Security)?
As part of the App development process, application security identifies, repairing, and preventing security flaws. Adding application security mechanisms at various stages of the development lifecycle is part of this.
Previously, security was implemented after the design and development of the product. Security, on the other hand, is now being pushed to the front of the development line. As a result, designing and testing applications with security in mind have become a must.
Why Is Application Security Necessary?
Because today’s apps are frequently available on multiple networks and are connected to the cloud, they are more vulnerable and prone to security issues. Not only on the network level but also within applications, there is increasing pressure to provide security.
The fundamental reason for this is that attackers are now more than ever targeting applications. Application security testing can address flaws in the system, allowing attacks to be prevented.
Let’s take an attack on LinkedIn as an example.
Application: LinkedIn
Cyber Attack Date: June 2021
Impact: 700 Million Users.
In June 2021, a data scraping incident involving 700 million LinkedIn users was reported on the dark forum ‘RaidForums,’ affecting more than 90% of the site’s users.
Before publishing information on around 500 million clients, an attacker known as “God User” performed data scraping techniques by compromising API.
Then they published a 700 million client database as a follow-up.
While LinkedIn claimed that the incident was a violation of its terms of service rather than a data breach. No sensitive, private personal data was exposed, a scraped data sample posted by God User contained information (email addresses, phone numbers, geolocation records, genders, and other social media details) , giving malicious actors plenty of data to craft convincing, social engineering attacks as warned by UK’s NCSC.
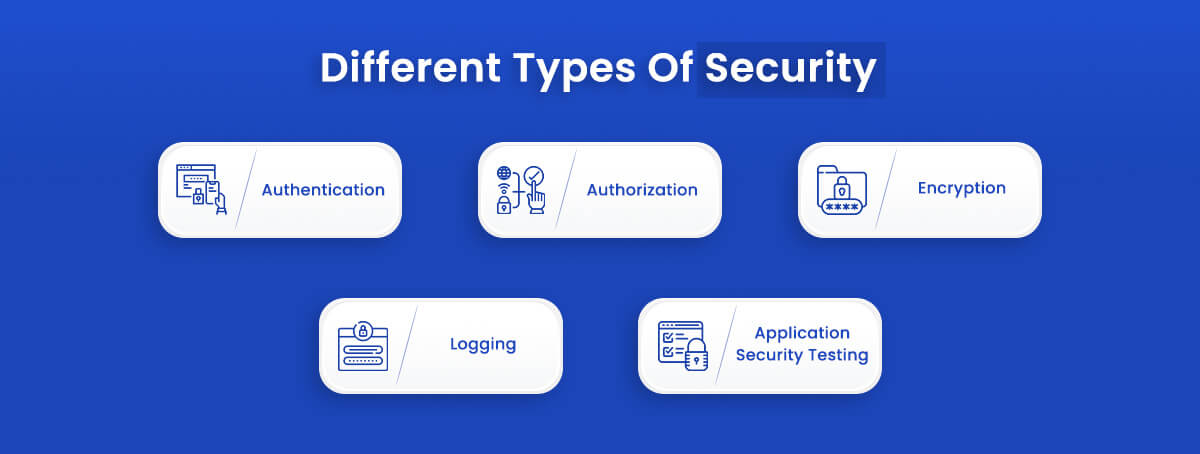
Different Types Of Application Security
Different application security features include authentication, authorization, encryption, logging, and application security testing. Keeping these points in mind, developers can craft the application with fewer vulnerabilities.
Authentication
Authentication is the procedure for verifying that a user is who they claim to be. You can hire application developers to design a protocols that ensures only authorized personnel access.
A logging mechanism is used to do this, which requires users to enter a username and password. Multi-factor authentication is another option.
Multi-factor authentication, as the name implies, necessitates the use of more than one authentication element.
Something you own (a cellphone), something you know (a password), and something you are could all be factors (facial recognition, Iris scan, Thumb Print).
Authorization
After the user has been authenticated, the user’s identity is guaranteed. The phrase “authorization” refers to the process of determining access levels and privileges.
To make application creation and management easier, Modern OS relies on a well-designed permission process. User type, credentials, verification, and needed roles are all critical considerations.
Encryption
Other security measures can prevent the data from being accessed or utilized once the user has been authorized and is using the program.
For example, consider a cloud-based application in which communication comprises sensitive data between end-users and the cloud, which is encrypted at the time. Encryption is used to keep data safe.
Logging
Users are first authenticated and then authorized, as we’ve seen. As a result, in the event of an application security breach, logging can assist in determining who accessed the data and how.
The time-stamped record of whatever aspect of the application was accessed and by whom can be found in the application logs.
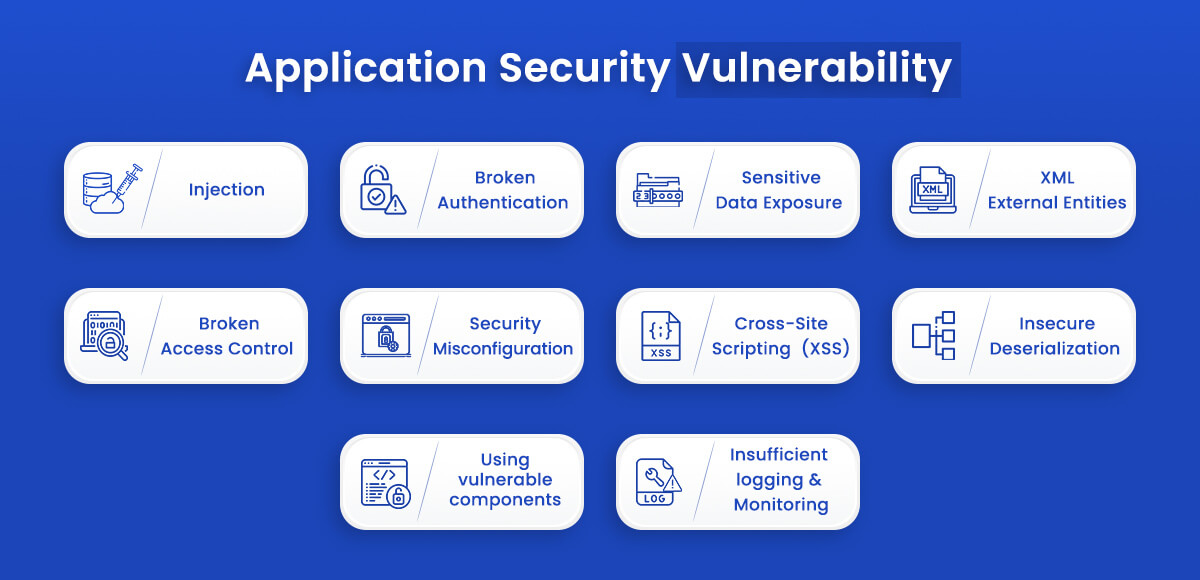
Application Security Vulnerability
Let’s take a look at OWASP top 10 App security vulnerability list
Injection
When untrusted data is provided to an interpreter as part of a command or query, injection vulnerabilities such as SQL, NoSQL, LDAP, and OS injections occur.
The attacker’s abusive data may trick the interpreter into performing an undesired command or accessing illegal data.
Broken Authentication
Authentication and session management features in applications are constructed improperly, allowing attackers to steal passwords, keys, or session tokens or exploit other technical flaws to temporarily or permanently assume other users’ identities.
Sensitive Data Exposure
Many web applications and APIs fail to protect sensitive data such as financial, healthcare, and other types of information. As a result, attackers may use such vulnerable data to commit credit card fraud, identity theft, or Phishing, among other things.
Without an extra layer of protection, such as encryption at rest or in transit, sensitive data can be compromised, necessitating special care while communicating over the web.
XML External Entities
Attackers can use insecure XML processors to exploit weak code and dependencies if they upload XML or the destructive content in the XML document.
Many improperly configured XML processors evaluate external entity references in XML documents.
Using a file URL handler, internal file share, internal port scanning, and a denial of service attack, external entities can be exploited to expose internal files.
Broken Access Control
Restrictions on what authenticated users can and cannot do are frequently ignored. As a result, attackers can utilize these weaknesses to get unauthorized access to unauthorized functionality and data, including gaining access to another user’s account, seeing sensitive files, modifying other user’s data, changing access rights, and more.
Security Misconfiguration
The most prevalent problem is security misconfiguration. Insecure default configurations, incomplete or ad hoc configurations, exposed cloud storage, misconfigured HTTP headers, and verbose error messages exposing sensitive information are significant causes of this. Therefore, all operating systems, frameworks, libraries, and programs must be configured securely and patched/upgraded regularly.
Cross-Site Scripting (XSS)
When an application puts untrusted data on a new page or alters the content of an existing page with user-supplied data, XSS issues occur.
Using a browser API for HTML or JavaScript creation. Attackers can employ XSS to execute scripts in the victim’s browser, which can use to hijack user sessions, deface websites, or redirect users to a malicious website.
There are two common XSS flaws. First, when malicious code is injected directly into an application, this is known as Stored XSS. Second, the malicious script is mirrored from an application onto the user’s browser in Reflected XSS.
Insecure Deserialization
Deserialization that isn’t secure can lead to remote code execution (RCE). They can be utilized in replay attacks, injection attacks, or privilege escalation attacks, even if they don’t result in RCE.
Deserialization is tough to exploit; off-the-shelf techniques won’t work unless they’re altered somewhat.
Using components with known vulnerabilities
Libraries, frameworks, and other software components, for example, have the same privileges as apps. An assault on the susceptible component can result in catastrophic data loss and perhaps a server takeover if it is exploited.
Applications and APIs that use components known to be vulnerable can compromise app security and make it an easy target for hackers. While many vulnerabilities have previously been exploited, it’s not always straightforward to uncover new ones. Others necessitate a significant amount of time and effort to create a specialized exploit.
Insufficient logging & Monitoring
Every major incident is founded on the exploitation of insufficient logging and Monitoring. To achieve their goals without being caught, attackers rely on a lack of surveillance and fast response.
Inadequate logging and Monitoring, along with a lack of or inefficient integration with incident response, allows attackers to continue attacking systems, maintain persistence, switch to other systems, tamper with data, and delete it.
The majority of breach studies reveal that breach detection takes more than 200 days and that external parties are more likely to detect breaches than internal Monitoring.
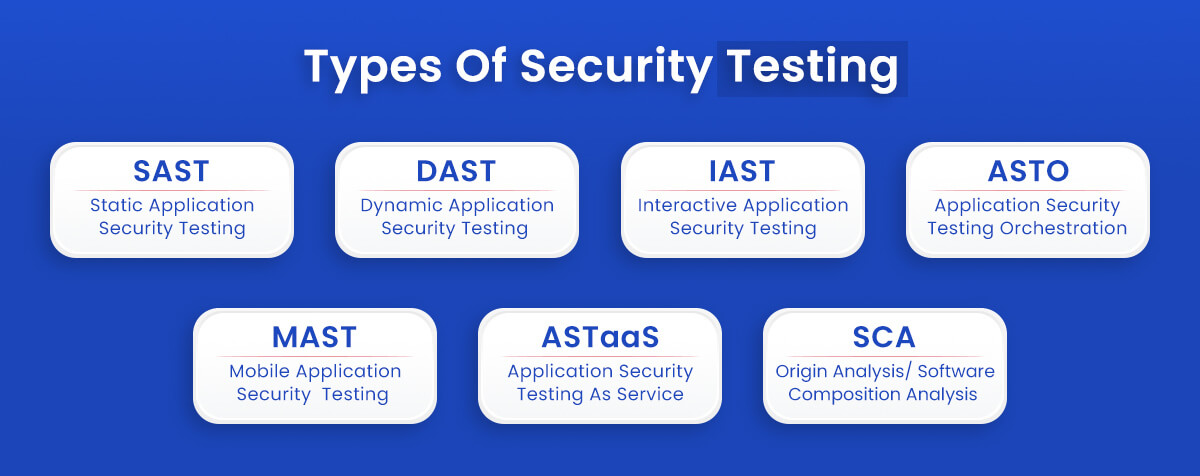
Types Of Security Testing
Bugs & flaws in software are all too familiar:
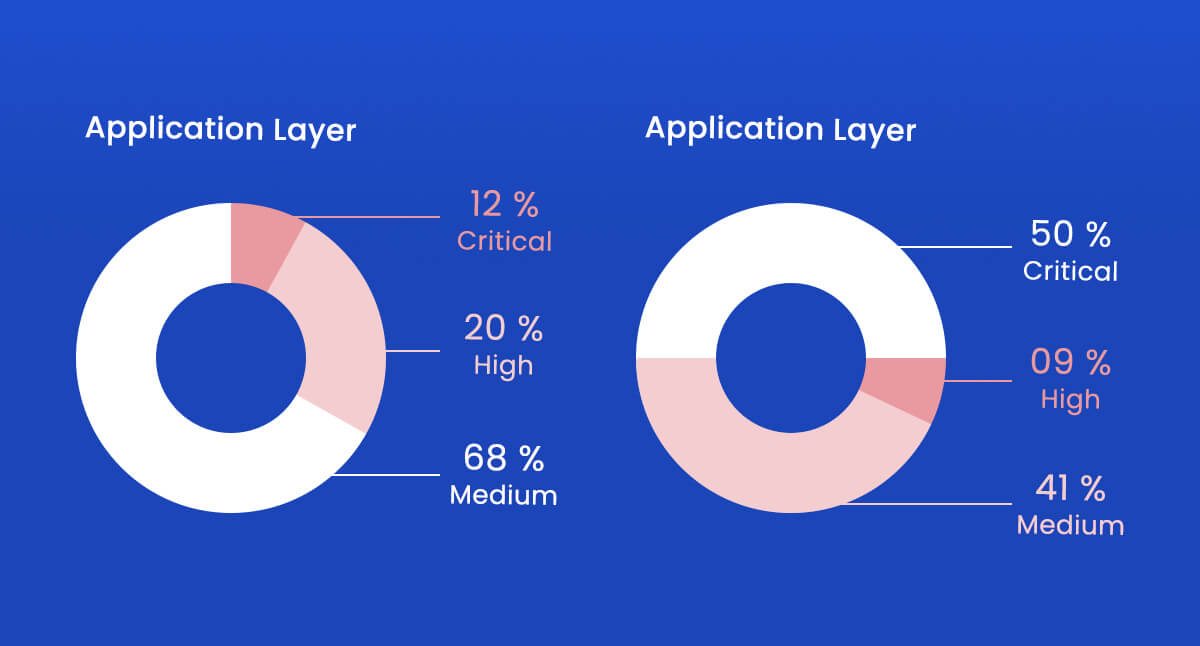
90% of all vulnerabilities are found in the application layer. – Department of Homeland Security
Therefore, one of the main reasons for employing application security testing (AST) solutions is the prevalence of software-related issues.
However, it can be difficult for information technology (IT) leaders, developers, and engineers to know which technologies handle vulnerabilities with the expanding number of application security testing solutions available.
This is the first in a series of blog posts on application security testing tools that will help you go through the multitude of options by categorizing the various sorts of AST tools available.
Static Application Security Testing(SAST)
SAST tools are similar to white-hat or white-box testing. The tester has access to information about the system or program being tested, such as an architecture diagram and source code, among other things.
SAST tools scan source code (at rest) for flaws that could lead to security vulnerabilities and report them.
Numerical mistakes, input validation, race circumstances, path traversals, pointers and references, and other faults can be checked by source-code analyzers on non-compiled code.
On constructed and compiled code, binary and byte-code analyzers do the same thing. Some tools only run on source code, while others only run on compiled code, while still others run on both.
Dynamic Application Security Testing (DAST)
Contrary to SAST tools, DAST tools are used for black-hat or black-box testing, in which the tester has no prior knowledge of the system. Instead, they detect circumstances in an application’s operating state that signal a security vulnerability.
For example, DAST tools detect flaws with interfaces, requests, responses, scripting (i.e., JavaScript), data injection, sessions, authentication, and more by running on operating code. Fuzzing is a technique used by DAST tools to throw known faulty and unexpected test cases at an application in huge numbers.
The dynamic component of DAST’s name refers to the fact that the test is conducted in a dynamic environment. Unlike SAST, which searches an application’s code line by line while idle, DAST testing occurs while the application is in use.
This isn’t to suggest that testing isn’t carried out while the app is in use. However, while DAST can be used in production, most testing is done in a quality assurance environment.
Interactive Application Security Testing(IAST) & Hybrid Tools
Hybrid techniques have been used for a long time, but IAST was just recently coined to identify and debate them. Static and dynamic analysis approaches are combined in IAST tools. They can check whether known code flaws can be exploited in a live application.
IAST tools employ application and data flow information to develop complex attack scenarios and recursively use dynamic analysis results. While a dynamic scan is run, the tool will learn things about the application depending on how it responds to test cases.
Some tools will use this information to generate more test cases, which will, in turn, generate more information for further test cases, and so on. IAST tools are good at eliminating false positives.
They operate well in Agile and DevOps contexts, where traditional stand-alone DAST and SAST tools can take too much time throughout the development cycle.
Application Security Testing Orchestration (ASTO)
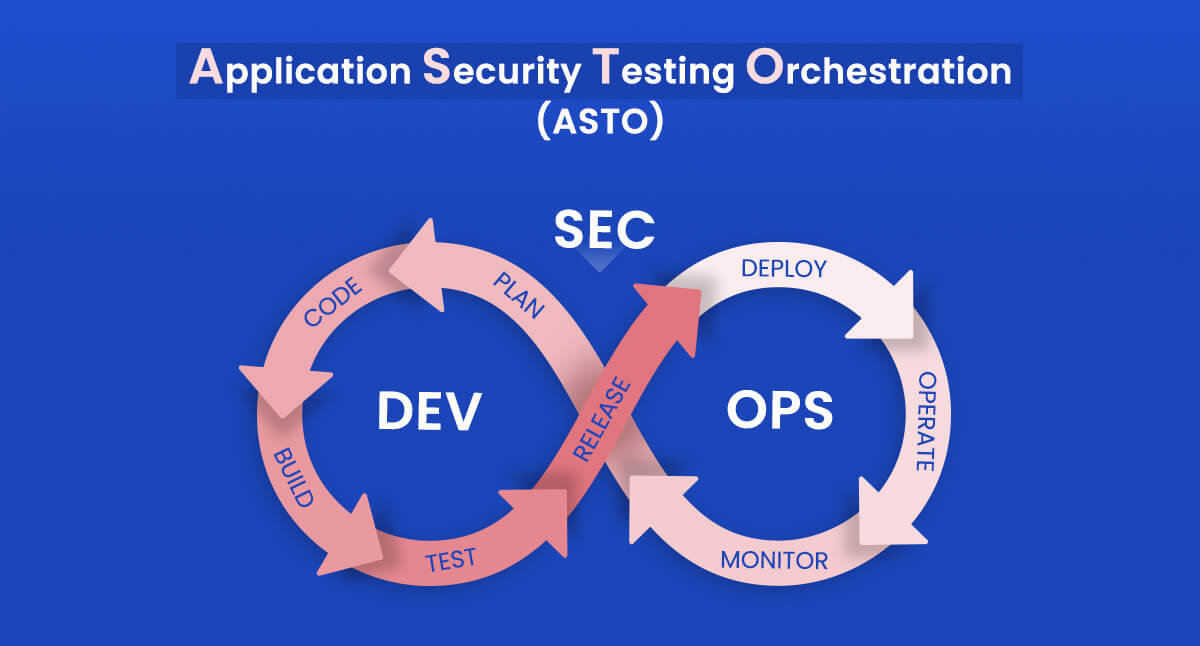
The term application security testing orchestration (ASTO) was introduced by Gartner’s 2017 Application Security Hype Cycle.
“Application security testing orchestration (ASTO) integrates security tooling across a software development life cycle (SDLC), usually as part of DevSecOps initiatives,” according to the report.
The goal of ASTO is to have a centralized, coordinated administration and reporting system for all of the AST tools in an ecosystem. It’s too early to tell if the word and product lines will stick around, but ASTO fills a need as automated testing becomes more common.
Engineers, Ops, and security teams are doing their best to achieve a highly secure software development lifecycle and effective DevSecOps practices. Application security testing orchestration is critical in assisting teams in centralizing the management of these tools and the data they produce. This enables businesses to ensure that all potential hazards are identified and addressed as soon as possible.
Correlation Tools
False positives are a significant problem in application security testing. By providing a central repository for data from different AST tools, correlation tools can help eliminate some noise.
Different AST tools will produce different results. Therefore, correlation tools can aid with the validation and prioritizing of findings and remediation workflows by correlating and analyzing results from various AST tools. While code scanners are included in specific correlation tools, they are mainly used to import data from other sources.
Test Coverage Analyzers
Test-coverage analyzers determine how much of a program’s entire code has been examined. The findings can be given as statement coverage (% of lines of code examined) or branch coverage (% of available paths tested).
Acceptable levels of coverage for large applications can be defined ahead of time and then compared to the findings given by test-coverage analyzers to speed up the testing and release process.
These tools can also discover if specific lines of code or logic branches cannot be reached during program execution, which is inefficient and can be a potential vulnerability.
Mobile Application Security Testing (MAST)
The top ten mobile threats, according to OWASP, are as follows:
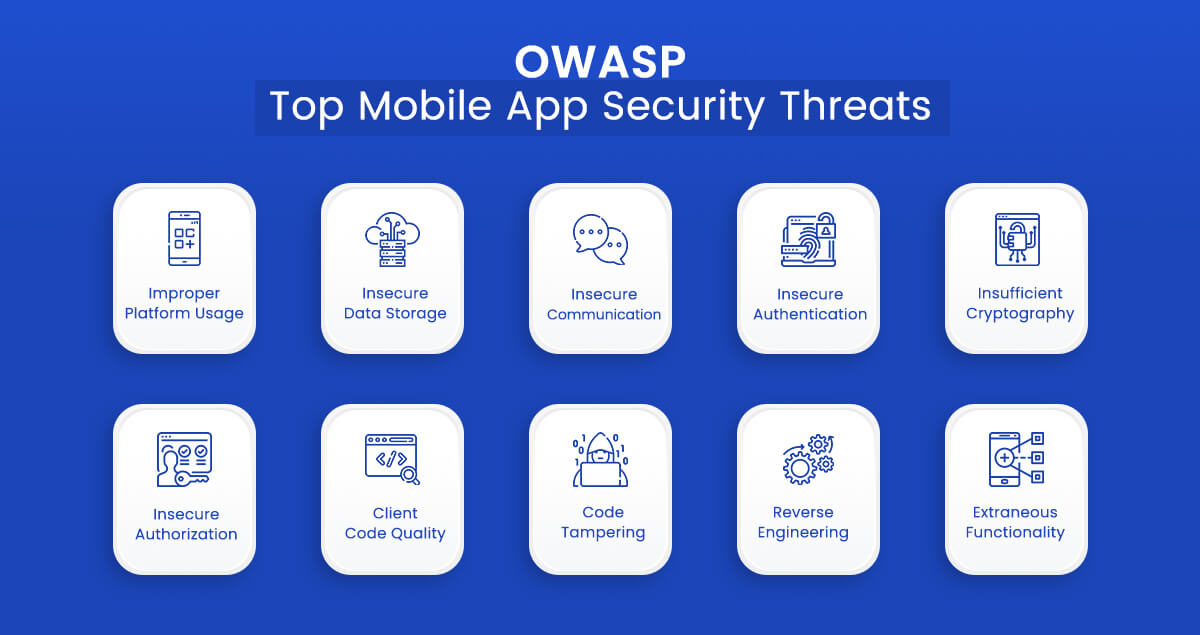
- Improper Platform Usage
- Insecure Data Storage
- Insecure Communication
- Insecure Authentication
- Insufficient Cryptography
- Insecure Authorization
- Client Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
MAST Tools combines static, dynamic, and forensics analysis into one package. They perform some of the same services as traditional static and dynamic analyzers, but they also let you run mobile code through them.
In addition, MAST tools contain particular functionality that targets concerns unique to mobile applications, such as device jailbreak or rooting, spoofed WI-FI connections, certificate management, validation, data leakage protection, and more.
Application Security Testing As Service(ASTaaS)
With ASTaaS, you pay someone to perform security testing on your application, as the name implies. In addition, static and dynamic analysis, penetration testing, application programming interfaces (APIs), risk assessments, and other services are frequently included in the package. As a result, traditional applications, particularly mobile and online apps, can benefit from ASTaaS.
The introduction of cloud applications, where resources for testing are easier to manage, has accelerated the adoption of ASTaaS.
Global public cloud investment is expected to reach $332.3 billion in 2021, up from $270 billion in 2020 by 23.1%. – Gartner
In addition, increased adoption of technologies like virtualization, edge computing, and containerization is driving up cloud investment.
Origin Analysis/ Software Composition Analysis (SCA)
Manual inspection-based software-governance systems are prone to failure. Software Composition Analysis (SCA) tools look into software to determine where all of the components and libraries came from.
These tools are quite good at detecting and uncovering flaws in common and popular components, primarily open-source components. They do not, however, detect weaknesses in custom-made components produced in-house.
SCA components are more powerful in finding popular libraries and components of Open-source. They work by comparing known modules found in code to a list of known vulnerabilities.
The SCA tools find components with known and documented vulnerabilities and will often advise if components are out of date or have patches available.
SCA tools get their information from the NIST National Vulnerability Database and Common Vulnerabilities and Exposures (CVE). Many commercial SCA products leverage the commercial VulnDB vulnerability database and some public and proprietary sources.
SCA tools can work with source code, byte code, binary code, or a combination of all three of them.
Database Security Scanning
Even though databases aren’t typically considered part of an application, application developers frequently rely on them, and databases can significantly impact applications. Scanners for database security Updated patches and versions, weak passwords, configuration mistakes, access control list (ACL) issues, and other issues should all be checked.
In addition, some technologies can mine logs for unusual patterns or actions, such as administrative overreach. The tools investigate the database’s internal settings for possible exploitable flaws in addition to performing some exterior activities such as password cracking.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites.
The following functions are used by database scanning programs to find vulnerabilities:
check/verify:
- passwords
- default account vulnerabilities
- logon hours violations
- account permissions
- role permissions
- unauthorized object owners
- remote login and servers
- system table permissions
- extended stored procedures
- cross-database ownership chining
- authentication
- login attacks
- stale login ids
- security of admin accounts
Application Security Testing Tools
Here both commercial and Free tools are listed in alphabetical order. First, let’s dig into the app security testing tool.

Arxan Application Protection
Araxan is proprietary protection capable of protecting apps from tampering, Reverse Engineering, API Exploits, and other attacks that can put your Business and Clients at risk. Additionally, this tool can be used for Runtime Application Self Protection(RASP).
- Target Audience: Experienced developers
- App Focus: RASP
- Packaging: Mac, Windows, Android, iOS, Linux
- Pricing: Contact Vendor
BurpSuite Professional
Burp Suite is a prominent penetration testing tool that has been dramatically expanded and improved over time. All tools use a typical architecture for handling and displaying HTTP messages, persistence, authentication, proxies, logging, and alerting.
In addition, more automatic and manual testing tools and connectivity with other frameworks like Jenkins and a fully-documented REST API are available in the commercial editions.
ITCS Rank #7
- Target Audience: Experienced Developers
- App Focus: Web app penetration testing and vulnerability scanner
- Packaging: Mac, Windows, Linux, JAR
- Pricing: Version ranges from free to $4000 per year, with a 60-day free trial.
IBM Security AppScan
Security AppScan is part of IBM’s extensive security product offering. There are three versions available: Source, Standard, and Enterprise. The software’s capacity to import data from human code reviews, penetration testing, and even competitor’s software vulnerability scanners has earned its reputation.
In addition, a mobile version is available for scanning iOS and Android apps.
ITCS Rank #4, Gartner MQ Leader
- Target Audience: Large Enterprise
- App Focus: Application code scanning, Including Mobile, Static and Dynamic Methods.
- Packaging: SaaS and On-Premises
- Pricing: 30-day free trial, Contact Vendor.
Klocwork
Static application scanning, continuous code integration, and a code architecture visualization tool are among the features offered by Klockwork. In addition, it has built-in inspection tools for various security standards, including CERT, CWE, and OWASP.
As a result, code injections, cross-site scripting, memory leaks, and other dangerous coding practices can all be detected.
ITCS Rank #9
- Target Audience: Developers
- App Focus: Static Code Analyzer
- Packaging: SaaS
- Pricing: Free trial.
Veracode
Veracode provides a comprehensive set of security testing and threat mitigation services, all of which are housed on a single platform. It’s used to identify flaws and estimate hazards in both development and production environments.
The product has a large following and has been around for a long time. Hundreds of thousands of different apps have been tested with it. Veracode may be used for small and big installations, and users commonly cite its superior ease of use.
ITCS Rank #1, Gartner MQ Leader
- Target Audience: Developers
- App Focus: Static and Dynamic code scanning
- Packaging: SaaS
- Pricing: Contact Vendor
App Security Best Practices
Let’s take a look at some of the most effective app security practices.
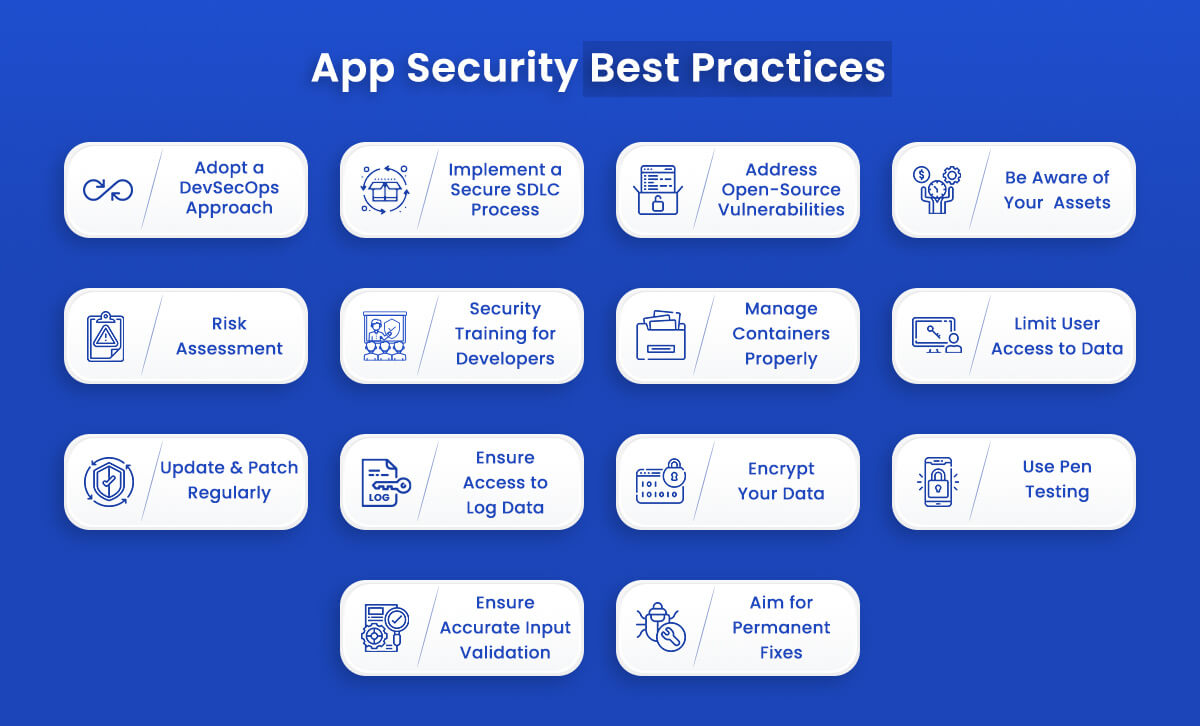
Adopt a DevSecOps Approach
DevSecOps strives to detect security flaws from the start, preventing security issues in the first place and resolving them as quickly as possible if they do occur.
In addition, DevSecOps helps the development team identify security issues throughout the software development process, from design to implementation.
Implement a Secure SDLC Management Process
The secure software development lifecycle management process (SSDLC) outlines the product life cycle from the standpoint of product security.
This product assures that item at various stages of their lifecycles:
- Employees with security training deploy and maintain the system.
- A built-in security system
- Delivered safely to consumers
SSDLC takes a holistic approach to product development, starting with the concept and continuing through all development activities until the product is thoroughly and safely disseminated in the market as a mature product and to the conclusion of its lifecycle.
Address Open-Source Vulnerabilities
While using open-source tools offers several benefits, including cost efficiency, they also expose you to significant vulnerabilities. Open-source software has ongoing Monitoring of vulnerabilities, regular updates, and patching of several security issues. All these things can lead to the exploitation of the software.
Be Aware of Your Assets
Knowing all of an organization’s assets is the first step toward understanding its security condition because you can’t secure what you don’t know. Therefore, it’s crucial to know precisely which assets make up your application and software development architecture.
Risk Assessment
Think like an attacker to estimate the risk. But, first, make sure you’ve covered all of your bases:
- Make a list of all the things you need to keep safe.
- Determine your threats and how to contain and isolate them.
- Identify the attack vectors that could compromise your application
- To detect and prevent attacks, make sure you have the appropriate security measures in place
- Determine if you require extra or alternative tools
Security Training for Developers
Because developers are in charge of the software’s development, they must receive security training. This training should be tailored to the role and security requirements of each developer.
Manage Containers Properly
You must use a digital signature tool to guarantee that your Docker image is signed and confirmed (Ex: Docker content trust).
To protect the utilization of containers through the standard integration pipeline, it’s critical to execute automatic scans for automatic vulnerabilities.
Limit User Access to Data
One of the best ways to improve security is to restrict user access to data. Keep the following points in mind :
- Determine who needs access to the specific resource.
- Create Access Rules and Policies
- Ensure that access privilege remains updated by removing active credentials once access is no longer required.
Update and Patch Regularly
One of the most efficient ways to keep your software security is to install software updates and patches. However, it’s critical to prepare ahead for each new update, as this necessitates creating the exemplary architecture to avoid API compatibility concerns when upgrading to new versions.
Ensure Access to Log Data
Having access to log data from your daily operations is vital for any incident response plan. The accumulation and interpretation of such data in the period leading up to the incident will directly impact security and may also be relevant for subsequent investigation. Without access to the log data, you will be powerless when a security incident occurs.
Encrypt Your Data
One of the best app security best practices is encrypting data in rest and transit. Basic encryption should be included, among other things, with SSL Certificate. It is recommended to save sensitive data in encrypted form. When stored in plain text, it can lead to Man-in-the-middle-attack (MITM). Therefore, always use robust encryption algorithms.
Use Pentesting
While automated tests discover the majority of security flaws before they are launched, there may still be gaps that have gone unreported. Therefore, it is worthwhile to hire a professional pentester to test the application to reduce this risk.
This type of ethical hacker tries to break into the program to uncover vulnerabilities and possible attack vectors to protect the system from an actual attack. The pentester must be a third-party specialist who isn’t affiliated with the project.
Ensure Accurate Input Validation
Always have validation while getting data from the user. Input data must be syntactically and semantically correct. Let’s understand this with the example of a password.
The data should be of specific length have the expected number of characters and digits. While validation is recommended, it’s not always possible to apply validation.
Aim for Permanent Fixes
While analyzing CVE lists, it can seem that several types of vulnerabilities reoccur from time to time, for instance: SQL Injection, Cross-site scripting, Privilege escalation, remote code execution, and buffer overflow. Therefore, it’s always recommended to get the root cause of the problem and fixing it permanently, rather than working with a partial fix.
Application Security Checklist
Let’s look at a checklist of factors to remember when working on application security.
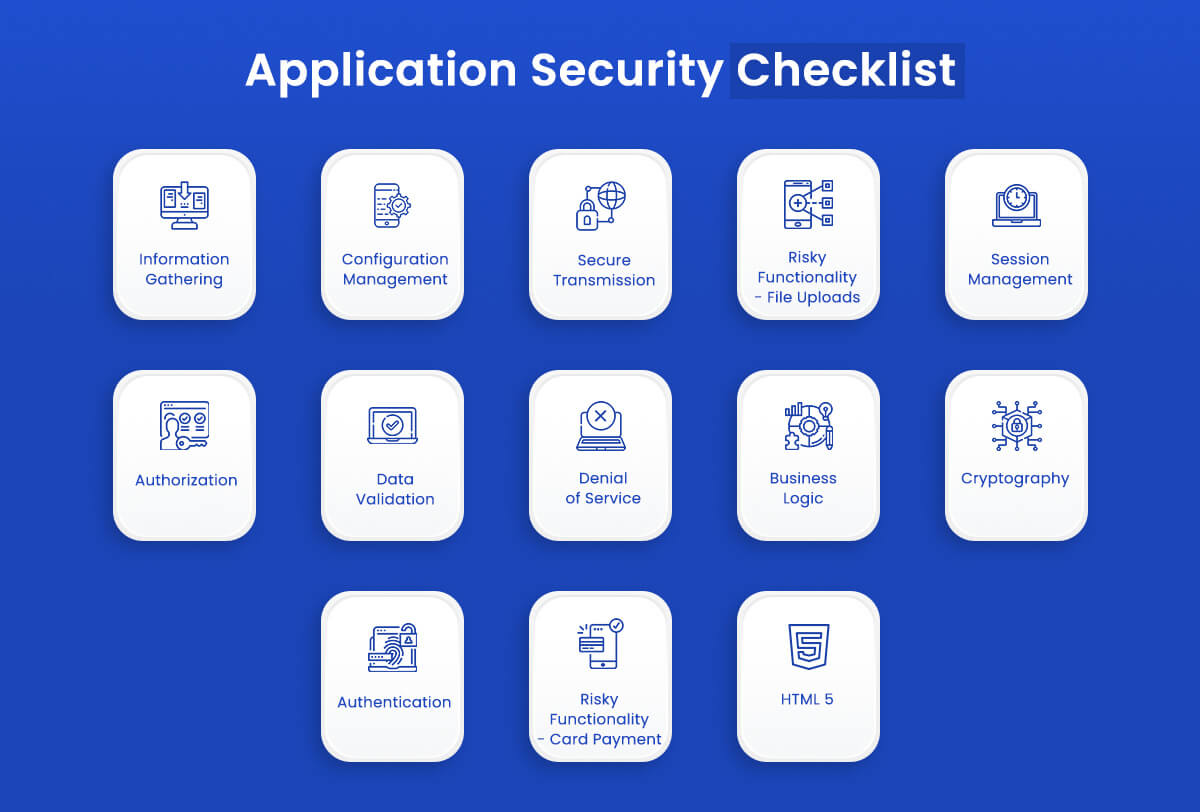
Information Gathering
- Explore the site on your own.
- Check for files that expose content, such as robots.txt, sitemap.xml, and DS Store, using a spider or crawler.
- Look for publicly available sites in the caches of significant search engines.
- Check for content discrepancies based on the User-Agent (e.g., Mobile sites, access as a Search engine Crawler)
- Fingerprinting of Web Applications
- Identify the technologies that were employed.
- Determine user roles.
- Determine the application’s entrance points.
- Client-side code must be identified, as well as multiple versions and channels (e.g., web, mobile web, mobile app, web services)
- Determine which applications are co-hosted and which are connected.
- Make a list of all hostnames and ports.
- Determine which material is hosted by a third party.
Configuration Management
- Look for commonly used administrative and application URLs.
- Examine your computer for obsolete, backup, and unreferenced files.
- Check out the HTTP methods that are supported, as well as Cross-Site Tracing (XST)
- The handling of file extensions is being tested.
- HTTP headers are checked for security (e.g., CSP, X-Frame-Options, HSTS)
- Examine for policies (e.g., Flash, Silverlight, robots)
- In a live environment, test for non-production data and vice versa.
- Inspect client-side code for sensitive information (e.g., API keys, credentials)
Secure Transmission
- Check the SSL version, the algorithms used, and the critical length.
- Check your digital certificate’s validity (Duration, Signature, and CN)
- Only the credentials for HTTPS should be examined.
- Check to see if the login form is sent over HTTPS.
- Session tokens for HTTPS should only be checked.
- Check to see if HTTP Strict Transport Security (HSTS) is turned on.
Authentication
- Test for user enumeration
- Attempt to bypass authentication.
- Password quality rules are tested for brute-force protection.
- Try out the “remember me” feature.
- On password forms/input, check for auto-complete.
- Password recovery and reset are put to the test.
- CAPTCHA is used to test the process of changing a password.
- Experiment with multi-factor authentication.
- Test for logout functionality presence
- Test for cache management on HTTP (e.g., Pragma, Expires, Max-age)
- Test for default logins
- Test for user-accessible authentication history
- Test for out-of channel notification of account lockouts and successful password changes
- Test for consistent authentication across applications with shared authentication schema / SSO
-
Session Management
- Establish how session management is handled in the application (e.g., tokens in cookies, token in URL)
- Check session tokens for cookie flags (httpOnly and secure)
- Check session cookie scope (path and domain)
- Check session cookie duration (expires and max-age)
- Check session termination after a maximum lifetime
- Check session termination after the relative timeout
- Check session termination after logout
- Test to see if users can have multiple simultaneous sessions
- Test session cookies for randomness
- Confirm that new session tokens are issued on login, role change, and logout
- Test for consistent session management across applications with shared session management
- Test for session puzzling
- Test for CSRF and clickjacking
Authorization
- Test for path traversal
- Test for bypassing authorization schema
- Test for vertical Access control problems (a.k.a. Privilege Escalation)
- Test for horizontal Access control problems (between two users at the same privilege level)
- Test for missing authorization
Data Validation
- Test for Reflected Cross-Site Scripting
- Test for Stored Cross-Site Scripting
- Test for DOM-based Cross-Site Scripting
- Test for Cross-Site Flashing
- Test for HTML Injection
- Test for SQL Injection
- Test for LDAP Injection
- Test for ORM Injection
- Test for XML Injection
- Test for XXE Injection
- Test for SSI Injection
- Test for XPath Injection
- Test for XQuery Injection
- Test for IMAP/SMTP Injection
- Test for Code Injection
- Test for Expression Language Injection
- Test for Command Injection
- Test for Overflow (Stack, Heap, and Integer)
- Test for Format String
- Test for incubated vulnerabilities
- Test for HTTP Splitting/Smuggling
- Test for HTTP Verb Tampering
- Test for Open Redirection
- Test for Local File Inclusion
- Test for Remote File Inclusion
- Compare client-side and server-side validation rules.
- Test for NoSQL injection
- Test for HTTP parameter pollution
- Test for auto-binding
- Test for Mass Assignment
- Test for NULL/Invalid Session Cookie
Denial of Service
- Test for anti-automation
- Test for account lockout
- Test for HTTP protocol DoS
- Test for SQL wildcard DoS
Business Logic
- Test for feature misuse
- Test for lack of non-repudiation
- Test for trust relationships
- Test for the integrity of data
- Test segregation of duties
Cryptography
- Check if data that should be encrypted is not
- Check for wrong algorithms usage depending on the context
- Check for weak algorithms usage
- Check for proper use of salting
- Check for randomness functions
Risky Functionality – File Uploads
- Test that acceptable file types are allowed
- Test that file size limits, upload frequency, and total file counts are defined and are enforced
- Test that file contents match the defined file type
- Test that all file uploads have Anti-Virus scanning in place.
- Test that unsafe filenames are sanitized
- Test that uploaded files are not directly accessible within the webroot
- Test that uploaded files are not served on the same hostname/port
- Test that files and other media are integrated with the authentication and authorization schemas
Risky Functionality – Card Payment
- Test for known vulnerabilities and configuration issues on Web Server and Web Application
- Test for default or guessable password
- Test for non-production data in a live environment and vice-versa
- Test for Injection vulnerabilities
- Test for Buffer Overflows
- Test for Insecure Cryptographic Storage
- Test for Insufficient Transport Layer Protection
- Test for Improper Error Handling
- Test for all vulnerabilities with a CVSS v2 score > 4.0
- Test for Authentication and Authorization issues
- Test for CSRF
HTML 5
- Test Web Messaging
- Test for Web Storage SQL injection
- Check CORS implementation
- Check Offline Web Application
Source: OWASP
Wrapping Up:
Application security is a dynamic ecosystem of technologies and processes that is always changing. To keep one step ahead of hostile attackers, ensure your application security policies are top-notch. Malicious attackers are changing and taking on new shapes as applications do. Your application security policies must keep up to protect against current threats like unsecured API endpoints, unvalidated API payloads, and client-side attacks injecting malware into unprotected scripts, among others.
“Build Realistic & Reliable App with Us”
Aglowid Holds Strong Portfolio in Enterprise-Grade Mobility Solutions
Also Check:




 Say
Say