Quick Summary:
Web app security is a crucial aspect of any service or business in this digital world. Many businesses solely depend on web applications for their business. Hackers are also learning new ways to exploit web applications and APIs as businesses upgrade by moving online. Attackers are constantly looking for new vulnerabilities in a web application, and a single successful attack can result in significant reputational and financial loss.
It’s critical to focus on web application security because online apps have grown to play a crucial role in our daily lives over the past few years. Web applications significantly impact everyone’s lives in today’s digital environment. Things can be done more quickly and with fewer resources by using web applications.
Online applications function identically on all platforms, which improves a company’s potential to attract more users. Regrettably, web apps open new entry points for hackers to compromise client and database systems.
Because of improvements in build and deployment techniques and the inherent security risk associated with browser-based apps, developers now have additional responsibility for protecting the code of the new web applications they release. In the past, many programmers worked under the assumption that hackers would need to go further to find and exploit weaknesses in code. This turned out to be a bad decision. Developers must change their thinking and assume responsibility for protecting apps before release.
If it still needs to be clarified, why it is important to secure web? Let’s talk numbers:
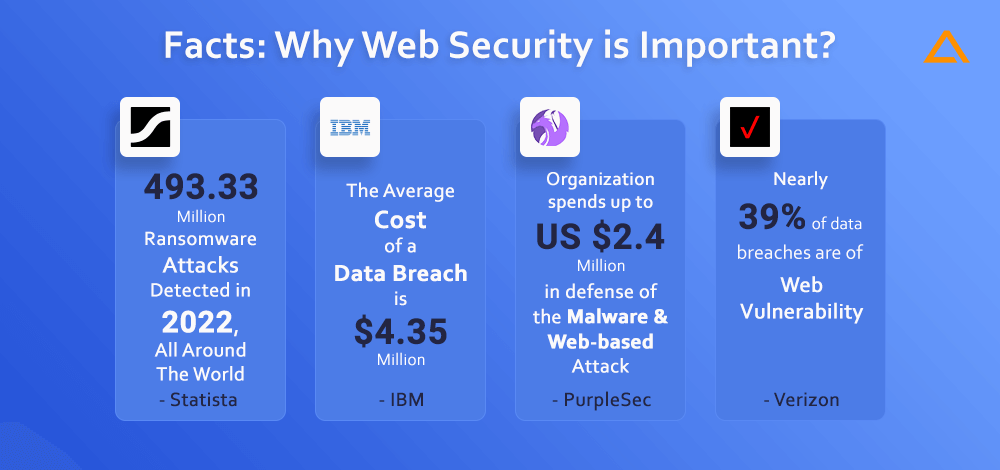
- According to IBM, the average cost of a data breach is $35 million
- Two of the most costly attacks are malware and web-based attack, on an average the organization spends up to US $2.4 million in defense- PurpleSec
- According to Verizon’s Data Breach Investigation Report, nearly 39% of data breaches are of web vulnerability
Now that you have a clear idea about why web server security is important Let’s ease into the web application vulnerabilities, their mitigations, and tips and tricks for web application security.
Rise of Web Security
Although web security is a crucial component of the SDLC cycle, many businesses need more knowledge to secure web applications better. Anybody can create a website with the help of many CMS technologies, including WordPress, Joomla, and other website builders. Most business owner overlook the possibility of web applications being entry point for various vulnerabilities to serve malicious purpose.
Because there are more web application assaults, web app security has become more important. Due to the growing usage of the internet for communication, storing sensitive information, and financial transactions, the internet is becoming increasingly crucial in our daily lives. Given all this, website security testing is now a requirement, not a luxury.
Web application security is a computer program that operates on a web server. Web application security safeguards your servers, services, and web applications against online threats and attacks. This covers everything, from the procedures and regulations you put in place to the technologies you use to mitigate vulnerabilities that threat actors can exploit.
To respond to this increasing demand, web developers and security experts have developed a range of tools and techniques designed to protect users from various online threats, including SQL injection, CSRF, XSS, malware infection, and data breaches. These security measures include encryption protocols. Apart from this firewall is also used to provide another layer of protection to safeguard the sensitive data and prevent unauthorized access. As the internet continues to evolve, the importance of web security will only grow, making it a critical area of focus for businesses and individuals alike.
Now that you have comprehensive knowledge about web security, let’s see What is the risk of not having application security?
What does a lack of web application security cause?
It is important to have secure web application penetration testing as more people rely on the internet and web applications for their daily needs. With such enormous use, it is important to have web application security measures in place. Though its quiet challenging to secure web application, we have listed down some of the web security issues you may likely to encounter

Customer Data Breach
You must keep the data secure within your application once the clients have given it to you. It includes ensuring that the data is safely stored in your application and that no flaws could act as the entry point for any data breaches. You can use the example of Ford to understand this better. Employee data leaked from Ford’s website due to a vulnerability. In the best-case scenario, this vulnerability would not have existed with a properly set up customer management system.
Revenue Loss
Your online application could have significant service interruptions and downtime if you don’t take the essential precautions, which could cost you sales and income. Imagine if a data breach caused an e-commerce site to be offline for hours, potentially ruining the company. For instance, the flash loan attack targeted the hacker who stole $197 million in cryptocurrency from Euler Finance.
Loss of Customer Trust
Customers are increasingly more concerned about Security due to the daily news stories about cyber-attacks. As a result of cyberattacks like data breaches and ransomware attacks, people are increasingly considering Cyber Security when providing personal information on an online service. A hack can seriously damage your brand’s reputation and customer’s faith in you.
Inadequate Security Standards
The government is stricter with companies that need more security measures considering data and privacy breaches. Regulations like GDPR, HIPAA, PCI, ISO/IEC 27001, and others have taken effect to ensure that businesses cannot get away with lowering security standards and protecting user privacy. If the Security of web applications is not handled seriously, there may be issues with violations of these regulations, which could lead to harsh fines, penalties, and legal action.
After this, you would have a comprehensive knowledge of what happens when there is a lack of Security, but how will you do a website Security check? The next section will look at web application security solutions to check website vulnerability.
Popular Web Application Security Testing Tools
Web application security tools are designed to help an organization identify and address vulnerabilities in web applications. These tools can be either open source or commercial, varying in complexity and capabilities. We have curated a list of web app security tools to help you check if the website is safe.
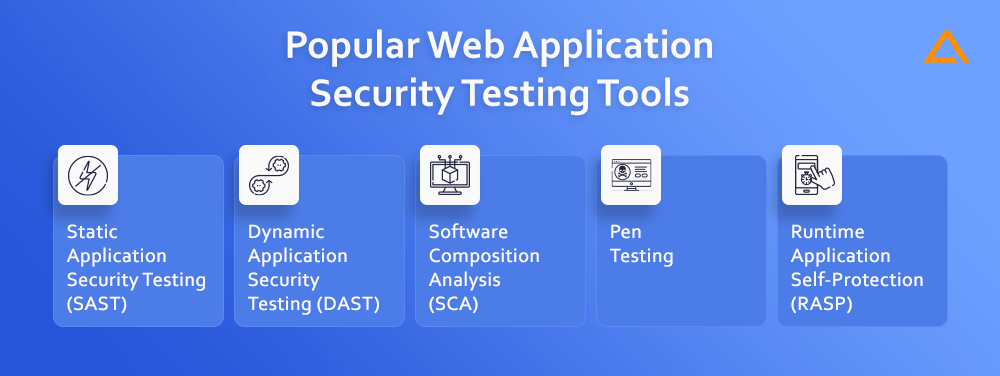
SAST
White-hat or white-box testing techniques compare to static application security testing (SAST) methods. The tester has access to details about the program or system under test, including the architecture diagram and source code, among other things. These technologies can scan against established best practices to find problematic coding patterns.
DAST
Black-box testing and black-hat testing are both forms of dynamic application security testing (DAST). Instead, they look for conditions that indicate a security flaw in an application’s current operation state. The test is administered in a dynamic setting, as the name would imply. DAST testing occurs while a program is running, unlike SAST.
Also Read: – App Security: Vulnerability, Best Practices, Testing Tools & Checklist
SCA
Software Composition Analysis (SCA) tools examine web applications with external code dependencies. SCA is a useful weapon in a security team’s toolbox because open-source libraries are widely used in current application development.
Pen testing tools
Penetration testing, a task performed by an ethical hacker, aims to identify and fix any attack vectors that could be exploited to compromise a web application. All web apps should undergo regular pen testing, which some legislation requires, such as PCI DSS.
RASP
The “runtime application self-protection” (RASP) technique is integrated to the application and is constantly checking for its actions. It is possible that some authentication-based attacking techniques may not be picked, although it complements perimeter solutions like WAFs. To leverage the full potential of RASP it should be used with tools like SAST and SCA.
These are some of the web app security testing tools that will help you with WAF security. Let’s move on and see why web applications and APIs are more vulnerable to cyber-attacks.
PLANNING TO HIRE WEB APP DEVELOPMENT COMPANY?
WE OFFER WEB APPLICATION DEVELOPMENT FOR ALL KINDS OF BUSINESSES THAT ARE EASY TO SCALE, HIGH-PERFORMING, INTUITIVE, SECURE, AND BEST-IN-CLASS.
Why Web applications and APIs are attacked?
Given the exponential growth of online applications and APIs, understanding the dangers of web apps is crucial. A web application threat (WAT) targets an enterprise through its website or applications. Organizations should address these security issues at every stage of development. The wide varieties of WATs are categorized. Among the most typical ones are:
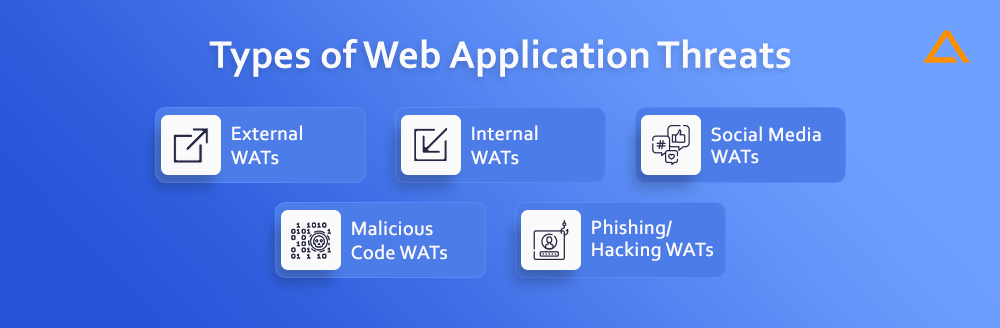
- External WATs
- Internal WATs
- Social media WATs
- Malicious code WATs
- Phishing/Hacking WATs
A web application’s Security can be compromised, posing major risks and causing long-term harm. The same is true for APIs. The emergence of freely available APIs for public usage has made it possible for almost the whole computer community to use them to enhance communication between programs and data. Although this may have many benefits, their availability often makes them a potential target for attackers.
Attackers have developed sophisticated techniques for building code designed to abuse APIs over time. An attacker can use a piece of malware to perform the same task as developers who build programming to retrieve data from a system belonging to an organization. They can employ malicious apps and APIs to inflict damage on unsuspecting consumers. To start assaults against companies or even specific people, it is intended to infect innocent users with malware.
Attackers can quickly obtain data when a web application or API is compromised. Also, the attackers can access confidential information and distribute malware across numerous devices. Organizations must implement stringent security controls to safeguard themselves against such attacks. The danger and sophistication of WATs and API threats will only increase over time.
Let’s take a closer look at the typical web application security flaws you can encounter to learn more about threats.
Common Web Application Security Vulnerabilities
A web application can face various challenges regarding web application security. Although it is important to consider that the attacks depend on the various factors affecting the website security. Security Experts often go for OWASP top 10 vulnerabilities, for a better understanding of the non-technical person, we have curated the list of common web application security vulnerabilities.
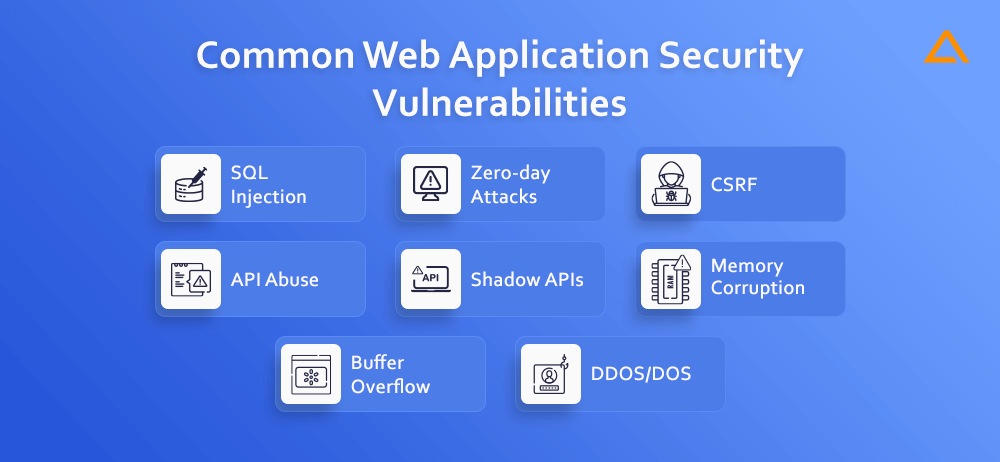
SQL Injection
A database’s search request processing weaknesses can be exploited by an attacker using the SQLi approach. SQLi is a tool malicious attackers use to access personal data, change it, or even delete it.
Zero-day attacks
These flaws are unknown to the developers of a program, and as a result, there is no patch for them. The most recent annual figure with the highest reported number of vulnerabilities was 22,514 found in 2022, according to Statista. Attackers frequently start by trying to swiftly attack these weaknesses and then move on to circumvent any security measures put in place by security companies.
CSRF
The goal of cross-site request forgery is to deceive a victim into sending a request that uses their authorization. An attacker can send a request pretending to be a user using the user’s account rights. When a user’s account is compromised, the attacker can access crucial data and exfiltrate, delete, or alter it. Targets often include executives or other highly privileged accounts.
API Abuse
The software that enables two apps to communicate with one another is known as an API or application programming interface. They might have flaws, like any other kind of software, that let hackers insert destructive code into a particular application or eavesdrop on private information sent between applications. As API usage rises, this attack type is becoming more widespread. Key API security vulnerabilities that organizations are currently facing were clearly outlined in the OWASP API Top 10 list.
Shadow APIs
Fast-moving development teams frequently create and publish APIs without consulting security teams to satisfy commercial objectives. These unknown APIs, which operate in the “dark” because security professionals responsible for protecting APIs are unaware of them, may expose important company data.
Memory Corruption
The software could exhibit unexpected behavior due to memory corruption, which happens when a position in memory is accidentally changed. Bad actors will try to detect and exploit memory corruption using exploits like code injection or buffer overflow attacks.
Buffer Overflow
A memory anomaly known as a buffer overflow happens when a region in memory is deliberately changed, potentially leading to unexpected behaviour in the software. Bad actors will try to identify the memory corruption exploit using exploits like code injection or buffer overflow assaults.
DDOS/DOS
Through a variety of vectors, attackers can overload a targeted server or its surrounding infrastructure with different types of attack traffic. When a server can no longer effectively process incoming requests, it begins to behave sluggishly and eventually deny service to incoming requests from legitimate users.
Also Read: – Web App Development Cost
Web App Security Mitigation
A vast and dynamic field, web application security. So, as new attacks and weaknesses are discovered, best practices for the discipline are updated. Nonetheless, the contemporary Internet threat landscape is sufficiently dynamic that no firm will be able to survive without a few security services that correspond to their particular business needs:
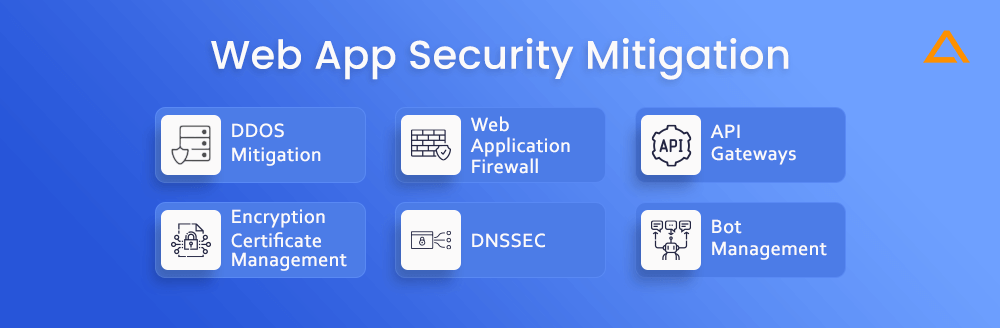
DDOS Mitigation
For DDOS mitigation, you can use various DDOS mitigation services available and put them between the server and the public internet. This mitigation should have specialized filtration and extremely high bandwidth capacity to prevent surges of malicious traffic from overwhelming the server. These services are important to prevent surges of malicious traffic from overwhelming the server. These services are important because many modern DDoS attacks deliver enough malicious traffic to overwhelm even the most resilient servers.
Web Application Firewall
The web application firewall, also known as WAF, can block traffic that is known to exploit web application vulnerabilities or is suspected of doing so. The rapid and stealthy emergence of new vulnerabilities makes WAFs crucial because almost no organization can detect them independently.
API Gateways
By limiting traffic known or suspected to be aimed at API vulnerabilities, this workaround aids in detecting the ignored shadow APIs (described above). Additionally, they aid in managing and keeping track of API traffic.
Encryption Certificate Management
This workaround works where the third party manages key elements of the SSL/TLS encryption process, such as generating private keys, renewing certificates, and revoking certificates due to vulnerabilities. This removes the risk of those elements going overlooked and exposing private traffic.
DNSSEC
To add a layer of Security for the DNS, DNSSEC is a protocol that guarantees a web application’s DNS traffic is safely routed to the correct servers, so an on-path attacker does not intercept users.
Bot Management
You can also include the Bot management system to distinguish between human users and automated traffic. The ability to prevent automated traffic from overwhelming your web application will also help you take action.
7 Web App Security Best Practices
The ideal solutions for the most challenging problems are occasionally the simplest ones. You are aware that protecting your website from hackers and other bad actors is important, but once you start looking into website vulnerabilities, you will encounter difficult ideas and arduous solutions. The Security of your website can be enhanced by adhering to some fundamental best practices. Immediately, you may secure your website by doing the following seven crucial things:
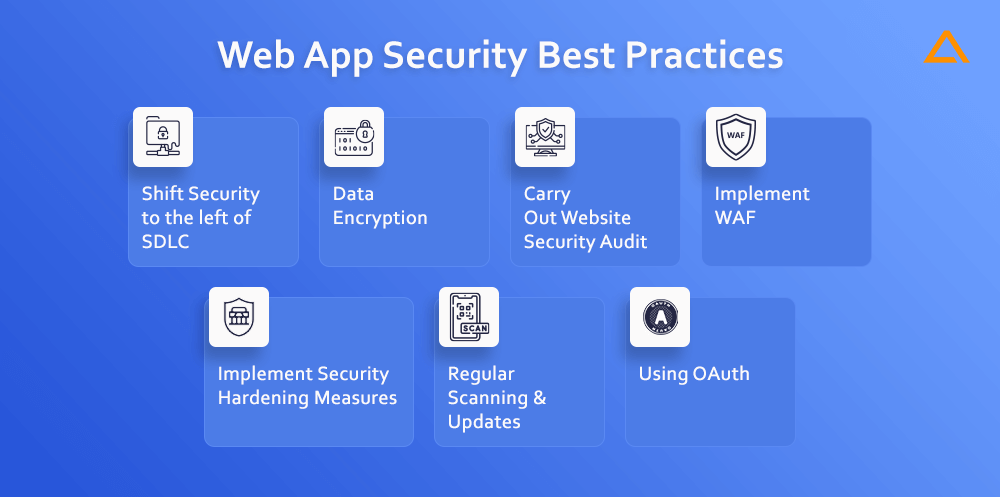
Shift Security to the left of SDLC
Shift-left Security replaces legacy security processes and tools designed for waterfall release methodology by moving Security as early as possible in the software development lifecycle. The following methods can help you with this:
- Use of threat modelling
- Security considerations while coding and architecture
- Code Testing while writing
Data Encryption (In Rest & Transit)
Visitors to your application may disclose sensitive information that has to be kept private. It becomes crucial to ensure that data is encrypted between the visitor’s browser and your server while in transit.
SSL/TLS encryption is used in this situation. All communications between site visitors & your website that use the encrypted HTTPS protocol are encrypted using SSL/TLS. In addition to building confidence with website visitors, encrypting this data in transit has SEO advantages. This is so because Google favours SSL-encrypted websites. (Google includes using HTTPS among the ranking elements in their search engine.) According to BuiltWith, SSL/TLS is now used by 65.76% of the top one million websites.
Nonetheless, some websites continue to operate with insecure encryption or without SSL. To guarantee that consumer information remains confidential when they browse your website, it is past due to begin using an SSL.
Carry Out Website Security Audit
Regular security audits are the greatest approach to ensure you’re following best practices for web application security and finding security flaws in your systems. You may stay safe from targeted intrusions and stay on top of any potential security flaws that may be present in the web application by doing this.
You can opt for the third-party testing team for an unbiased assessment. They’ll be better prepared to do website penetration testing and assist your team in identifying flaws that need to be patched or otherwise addressed because they have experience with professional Security and haven’t had much contact with the code. The following categories of website security audits are typical:

Black Box Security Audit
This security audit can be called “hacker style.” As this security audit is one in which the online application is evaluated for exploitable security flaws without any information about it being requested. You essentially provide the appropriate URL of the web application to the black box audit team.
White Box Security Audit
Opposite of Black box testing, this approach has all the important information, often shared before performing the audit. The objective of the white box audit is to verify that all best practices, including secure coding procedures and the best configurations for cloud infrastructure, are being followed.
Gray Box Security Audit
As the name implies, a grey box audit combines black box, and white box audits by requiring access to some crucial data, such as test account credentials, before beginning the security audit.
After a security audit is complete, any discovered vulnerabilities must be fixed. Prioritizing the patching is best done by classifying the vulnerabilities according to their impact and starting with those with the greatest potential for harm.
Also Read: – Web App Ideas
Implement WAF
All the facets of real-time monitoring of the security posture of your online application are covered by a web application firewall (WAF). Using a WAF, you may instantly stop any activity that appears to be dangerous on your website or web application, including XSS, SQL Injection, or malicious bots attempting to extract information from your website or conduct DDoS assaults).
Nonetheless, there may be instances where WAFs report false positives while omitting warning indicators of security breaches. As a result, you could also employ a WAF in conjunction with an Application Security Management Platform (ASMP) such as Sqreen or a Runtime Application Self-Protection (RASP) solution. Real-time threat monitoring and protection are features of these solutions, which adapt to your security requirements.
Implement Security Hardening Measures
A few of the following components will require Security hardening steps above and beyond their default configurations:

Script execution time: The maximum script execution time specifies the maximum time a specific script can run on your server. It’s a smart option to customize this based on the use case for your application. It could be a good idea to set the maximum execution time to a low value because doing so would limit the attack options available to attackers.
Disable modules: It’s usually a good idea to turn off any web server modules or extensions the application isn’t using. As a result, the assault surface area is smaller.
Content Security Policy: Including a content security policy By defining trusted redirect URLs, a robust content policy stops dangerous attacks like redirection malware from gaining ground.
Regular Scanning & Updates
Manual application penetration testing is one of the safest defense methods against API and WAT attacks. It is strongly advised that you speak with a security professional if you still need to get one on hand. The primary responsibilities of a security specialist include monitoring hostile activity, executing security audits, and scanning for vulnerabilities. Automation can be used in conjunction with manual assessments by a security expert to help guarantee dangers are not overlooked. This gives the company access to accurate expert input and information about the areas that attackers are most likely to target.
Using OAuth
It is also possible to implement security measures within the system itself. This can be done using two-factor authentication. The key aim of this is to keep unauthorized users out. In addition to this, you can also opt for time-based one-time passwords (TOTPs). The use of this kind of authentication has increased in recent times. This authentication technique is used in various sectors.
Allowlist and Denylist the employees will also ensure access is only granted to the trusted systems. Because of this, you can watch for and be alerted if a stranger secretly tries to access your internal network through an external server.
Wrapping up!
In conclusion, web application security is an important component of any organization’s overall security posture that depends on web applications to provide services to its users. To safeguard sensitive data and uphold customer trust, enterprises must prioritize strengthening web application security in light of the rising number of cyber threats and attacks.
Generally, strengthening web application security necessitates a mix of technical and non-technical actions that entail cooperation and coordination amongst many organizational stakeholders. Organizations can reduce the risk of security events, defend their reputation and brand, and safeguard their clients’ private data by adopting a proactive approach to web application security.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites
Also Check:



 Say
Say