Quick Summary:
For creating dependable and secure apps, Python’s secure coding techniques are crucial. The use of up-to-date frameworks, strong authentication, defense against widespread web vulnerabilities, input validation, secure storage of sensitive data, appropriate encoding, and regular security audits are among the key practices. By using these techniques, Python applications are more secure and robust overall.
When it comes to the development of software in today’s networked world, security is of the utmost importance. The need of maintaining the security of Python programs has grown as Python’s popularity due to its simplicity and adaptability has continued to grow. Building solid and reliable apps that safeguard user data and shield systems from flaws and harmful assaults requires secure coding techniques, which are essential.
Developers can defend your application against frequent security risks like authentication flaws, cross-site scripting (XSS), cross-site request forgery (CSRF), injection attacks, and unsafe configuration procedures by following secure coding practices. An application that secures user data and upholds user confidence can be created by starting with a security-centric mindset.
This can minimize the risk of breaches, maintain the confidentiality and integrity of sensitive information, and enhance the overall resilience of their software solutions. By following these secure coding standards, you can enhance the overall security posture of your Python framework-based application, reducing the risk of security breaches and ensuring the confidentiality, integrity, and availability of your application and its data.
The question here arises is why secure coding is important. Let’s look at the answer for the same. It is important that developers need to be vigilant and keep in mind the following things.
- Security & Safety of Code
- Application architecture & design requirements
- Efficiency & Optimization of Code
But what happens when you are not writing the secure code? If your application is not secure enough, it can create loopholes or backdoors for the security theft. Like this, the person with malicious intent can have direct access to the device or can provide access to the different devices connected to the same. The result can be any of the following:
- Compromised secrets
- Loss of Service
- Denial of Service Attack
- System Damage
- Loss of Reputation
There are number of frameworks and libraries available in python. But still there can be concerns of whether python is safe or not. So, Before diving in to the realm of Python Security, let’s answer this question for you.
Is Python Safe?
Python remains a highly regarded and secure programming language, with a thoughtful approach to addressing security concerns. Adhering to several best practices (mentioned in the blog) fosters a safe development environment. Regular code reviews and meticulous testing offer an added layer of protection by proactively identifying and resolving potential vulnerabilities. Implementing robust authentication, authorization mechanisms, and secure communication protocols further fortifies the protection of sensitive data. Python’s dynamic community and consistent updates affirm its reliability, positioning it as an excellent choice for secure and innovative application development.
Now that you have an idea about why it is important to write secure code and what happens when you are not writing the secure code. Let’s dive into Python secure coding guidelines. Let’s start with the OWASP the cyber security Python coding project and move on to the Python security best practices along with the popular frameworks.
OWASP Python Secure Coding Best Practices
Whenever there is a topic of security there is always a mention of OWASP. As a widely recognized organization that focuses on web application security. This organization focuses on web application security. They provide valuable resources, guidelines, and recommendations for secure coding practices in various programming languages, including Python.
The OWASP Python Secure Coding Practices provide developers with essential guidelines to build secure Python applications. These practices cover a wide range of security considerations, let’s take a look at a few of them.
Manipulating Time Object
import time
initial_struct_time = [tm for tm in time.localtime()]
# Example on how time object will cause an overflow
# Same for: Year, Month, Day, minutes, seconds
invalid_time = (2**63)
# Change ‘Hours' to a value bigger than 32bit/64bit limit
initial_struct_time[3] = invalid_time
overflow_time = time.asctime(initial_struct_time)This code example demonstrates how manipulating a time object can lead to an overflow error.
The code first imports the time module, which provides various functions for working with time-related operations. Next, it creates a list called initial_struct_time using a technique called list comprehension. This list contains different components of the current time, such as the year, month, day, hour, minute, and second. After that, it assigns a very large value (2^63) to a variable called invalid_time. This value is intentionally chosen to be larger than the limit that the system can handle.
The code then modifies the hour component of the initial_struct_time list and sets it to the invalid_time value. This step represents changing the hour of the time to a value that exceeds the limit of what the system can handle. Finally, it calls time.asctime() function, passing the modified initial_struct_time list as an argument. This function converts the time represented by the list into a human-readable string format.
Due to the invalid and extremely large value assigned to the hour component, an overflow error will occur when trying to convert the modified time into a string using time.asctime(). This happens because the value exceeds the maximum limit that the system can handle for representing time.
The maximum value for a 64-bit system would be [2^63-1], but different errors will be generated depending on the used values. Any number outside the valid range will generate an Overflow. The solution to this problem would be implementing proper data validation.
Using Pickle and cPickle
Let’s understand this concept with code.
Pickle
import pickle
import io
badstring = "cos\nsystem\n(S'ls -la /'\ntR."
badfile = "./pickle.sec"
with io.open(badfile, 'wb') as w
w.write(badstring)
obj = pickle.load(open(badfile))
print "== Object =="
print repr(obj)The specified Python “pickle” module is used in an unsafe manner in the submitted code. Pickle is a serialization library that enables the transformation of objects into byte streams and back again. Nevertheless, employing pickle insecurely can result in security flaws.
The pickle module and the io module are both imported in the code snippet. It begins by creating a string with the name “badstring” that is loaded with malicious code. This code tries to use the system function to run the shell command “ls -la /”. Due to the possibility of arbitrary commands being run on the system, this poses a security risk.
The next step is to use io.open in write binary mode (‘wb’) to create a file called pickle.sec. The file is then written with the malicious string badstring. Since the function writes untrusted data to a file without adequate validation or sanitization, this exhibits an insecure behavior.
The pickle.sec file’s contents are loaded using the pickle.load function. The malicious pickled string is present in the file, so loading it can run the injected code. This exhibits an arbitrary code execution security flaw that an attacker may use to run unauthorized instructions on the system.
The loaded object is then printed using repr(obj), which can show the outcome of the injected code’s execution. This demonstrates the possible consequences of using pickle to deserialize untrusted data.
It is important to note that using pickle with untrusted or unsanitized data from unauthenticated sources can lead to security breaches, as it allows arbitrary code execution. To mitigate these risks, it is recommended to avoid using ‘pickle’ with untrusted data or implement proper input validation, data sanitization, and deserialization techniques.
cPickle
import os
import cPickle
import traceback
import sys
# bignum = int((2**31)-1) # 2147483647 -> OK
bignum = int(2**31) # 2147483648 -> Max 32bit -> Crash
random_string = os.urandom(bignum)
print ("STRING-LENGTH-1=%r") % (len(random_string))
fout = open('test.pickle', 'wb')
try:
cPickle.dump(random_string, fout)
except Exception as e:
print "###### ERROR-WRITE ######"
print sys.exc_info()[0]
raise
fout.close()
fin = open('test.pickle', 'rb')
try:
random_string2 = cPickle.load(fin)
except Exception as e:
print "###### ERROR-READ ######"
print sys.exc_info()[0]
raise
print ("STRING-LENGTH-2=%r") % (len(random_string2))
print random_string == random_string2
sys.exit(0)The provided code shows potential problems while using ‘çPickle’ in Python. It demonstrates a scenario where attempting to serialize and deserialize large data can lead to crashes or errors. The code generates a random string of a large size and tries to pickle it. If an error occurs during the pickling or unpickling process, the relevant information is printed and the program terminates. The code serves as an example to highlight the challenges of working with large data sizes in cPickle and the potential limitations or exceptions that can arise.
The solution to this is to limit the data size to 32-bit sizes even in 64-bit systems and implement strong data validation to make sure that nothing dangerous will be processed.
Utilizing Proper Communication Channels
import SimpleHTTPServer
import SocketServer
PORT = 45678
def do_GET(self):
self.send_response(200)
self.end_headers()
Handler = SimpleHTTPServer.SimpleHTTPRequestHandler
Handler.do_GET = do_GET
httpd = SocketServer.TCPServer(("", PORT), Handler)
httpd.serve_forever()The library will allow it to conduct activities that are not safe and right, the core libraries are OS-independent, and the developer must understand how to construct the appropriate communication channel for each OS.
Socket. error: [Errno: 48] Address already in use
If a client connects to the HTTP server and then we close the server, python will not release resources, the OS will not release the socket.
import socket
import SimpleHTTPServer
import SocketServer
PORT = 8080
# ESSENTIAL: socket reuse is set up BEFORE it is bound.
# This will avoid TIME_WAIT issues and socket-in-use errors
class MyTCPServer(SocketServer.TCPServer):
def server_bind(self):
self.socket.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
self.socket.bind(self.server_address)
def do_GET(self):
self.send_response(200)
self.end_headers()
Handler = SimpleHTTPServer.SimpleHTTPRequestHandler
Handler.do_GET = do_GET
httpd = MyTCPServer(("", PORT), Handler)
httpd.serve_forever()A library that appropriately establishes and terminates communications and releases resources for each OS and each protocol should wrap the protocol library as the answer to this problem.
Also Read: – Python Best Practices to Follow
Python Security Best Practices
In addition to bolstering the overall reliability of its software solutions, this proactive approach contributes to minimizing the risk of breaches and safeguarding critical data’s confidentiality and integrity. By aligning with these secure coding guidelines, you not only enhance the security stance of your application but also cultivate an environment that discourages security breaches. This approach extends its significance across various domains of application development, including the intricate realm of Python GUI frameworks, where security is integral to creating robust and trustworthy user interfaces.

Use Latest Version
One of the most important components of secure coding practices is using the most recent version of Python. For developers, updating frequently to the most recent Python release has various advantages. The general security of the codebase is improved in the first place by making sure security fixes fixing flaws found in earlier versions are applied. The stability and effectiveness of the programs are also enhanced by bug patches and performance enhancements in more recent versions.
Another benefit is the ability to use new features and improvements thanks to compatibility with updated libraries and frameworks. In addition, the most recent Python versions’ language and grammar advancements make it easier to write code that is more legible, manageable, and secure. Developers may strengthen their programs, enhance performance, and take advantage of the newest security developments by remaining current with the most recent Python version.
Use Virtual Environment
For Python security, making use of a virtual environment is essential. Developers can separately manage dependencies and package versions thanks to the isolation and self-contained environment that a virtual environment generates for a certain project. Developers can prevent conflicts between other projects and guarantee the isolation and consistency of the project’s dependencies by setting up a virtual environment.
This method makes it simpler to replicate and deploy the program across several systems by granting better control over the project’s environment. Developers can keep their development workflow neat and orderly while reducing the possibility of compatibility problems and unwanted interactions between packages by encapsulating dependencies within a virtual environment. Overall, using virtual environments when developing Python code encourages modularity and maintainability, and it guarantees a more dependable and consistent development process.
Are you looking to hire Python developer?
Hire a dedicated team from Aglowid for high-quality python developers who are equipped with the latest Python skill-sets
Input Validation
The process of validating and cleaning up user input to make sure it adheres to the required standards and format is known as input validation. It is a fundamental secure coding practice. Security flaws like injection attacks, route traversal, or code execution can be avoided by verifying input, such as data type, length, or format, and sanitizing it to eliminate potentially harmful elements. XSS attacks, SQL and OS command injections, and unauthorized file access are hazards that can be reduced with proper input validation. To meet changing security threats and ensure application integrity, input validation should be carried out on both client-side and server-side components. It also needs to be continually reviewed and updated.
import re
def is_valid_email(email):
# Validate email format
pattern = r'^[a-zA-Z0-9_.+-]+@[a-zA-Z0-9-]+\.[a-zA-Z0-9-.]+$'
if re.match(pattern, email):
return True
return False
# Usage
user_email = input("Enter your email: ")
if is_valid_email(user_email):
# Proceed with the email
pass
else:
print("Invalid email!")We concentrated on email address verification in the given case. If the email address does not match the required format, the function is_valid_email will employ a regular expression pattern to check. The method either returns False if it doesn’t, or True if it does. You can reduce the chance of using malicious or deformed data by verifying user input before using it in your code.
Secure Password Storage
To safeguard user accounts and stop illegal access, secure password storage is crucial. Use powerful cryptographic hash algorithms like bcrypt, PBKDF2, or Argon2 to store passwords securely. Prevent the use of precomputed tables by using unique salts for every user. Apply key stretching techniques to make password hashing more computationally expensive, making it harder for hackers to guess passwords.
Aside from avoiding the storage of plain text values for the salt and hash values, it’s also a good idea to change hashing algorithms frequently. Using the previously stored salt and settings, recompute the hash when confirming passwords, then compare the results to the previously saved hash. Incorporate multi-factor authentication and consider educating users about the use of secure passwords. You may greatly improve password security by adhering to these guidelines, and you can shield user accounts from illegal access.
import hashlib
import os
def hash_password(password):
# Generate a random salt
salt = os.urandom(16)
# Hash the password with the salt
hash_value = hashlib.pbkdf2_hmac('sha256', password.encode('utf-8'), salt, 100000)
# Return the salt and hash value
return salt, hash_value
def verify_password(password, salt, hash_value):
# Verify the password by recomputing the hash with the provided salt
new_hash_value = hashlib.pbkdf2_hmac('sha256', password.encode('utf-8'), salt, 100000)
# Compare the computed hash with the stored hash
return new_hash_value == hash_value
# Usage
password = input("Enter your password: ")
salt, hash_value = hash_password(password)
# Store salt and hash_value securely
# Verify password
password_to_verify = input("Enter your password again: ")
if verify_password(password_to_verify, salt, hash_value):
print("Password is correct!")
else:
print("Password is incorrect!")To safeguard user accounts, it is essential to store passwords securely. Plain text password storage should be avoided at all costs. To securely store passwords, you should instead utilize cryptographic functions and salts.
The hash_password function in the supplied example accepts a plain-text password as input. It uses the PBKDF2 (Password-Based Key Derivation Function) technique with SHA-256 as the hash function after generating a random salt using os.urandom. The salt and the resulting hash value are safely kept.
The verify_password function compares the newly computed hash value with the hash value that was previously saved to validate a password. The password hashes are made to be computationally challenging to reverse or guess even if they are revealed thanks to this method. You can increase the security of password storage by employing powerful hashing algorithms and distinctive salts for each password.
Also Read: – Python Optimization: Performance, Tips & Tricks
Import The Packages Right Way
Writing secure and effective Python programs necessitates appropriately importing packages, whether through explicit imports or implicit imports. Developers may ensure appropriate module resolution, preserve code readability, and reduce potential security issues by adhering to best practices for imports.
With explicit imports, only the essential parts of a module are brought in, typically using expressions like from module import components. This method improves code readability and keeps extraneous symbols out of the global namespace. It makes the code clearer and simpler to maintain by indicating which components are being used.
Contrarily, implicit imports refer to the act of importing a complete module using the wildcard * symbol, as in from module import *. This might cause confusion and potential problems, even though it might reduce some typing. Implicit imports can cause naming conflicts if numerous modules define the same symbol, making it difficult to monitor which symbols are being used from a module.
Implicit imports should generally be preferred over explicit imports. Developers can more clearly define their dependencies, avoid name conflicts, and maintain better codebase control by explicitly importing only the necessary components.
Use Cryptography Libraries
Using Python’s well-known cryptography packages, secure password storage may be implemented successfully. These libraries offer powerful and tried-and-tested functions for key derivation and password hashing. Bcrypt and passlib are two popular cryptography packages for Python. Here is more information on how to use these libraries for safe password storage:
- Bcrypt
Bcrypt is a library specially designed for password hashing. It uses built-in salt and key starching mechanism to enhance security. Following is an example of using ‘Bcrypt’ in Python.
import bcrypt
# Hash a password
password = ‘my_password'
hashed_pass = bcrypt.hashpw(password, bcrypt.gensalt())
# Verify a password
entered_password = 'my_password'
if bcrypt.checkpw(entered_password, hashed_pass):
print ("Password is valid.")
else:
print ("Invalid password.")The password is hashed using a salt that is produced randomly in this case using the bcrypt.hashpw() method and the hashed password is then safely saved. Once the password has been entered, the saved hashed password is compared using the bcrypt.checkpw() function.
- Passlib
A more advanced interface for password verification and hashing is provided by the passlib package. Key stretching, additional password security features, and several hash algorithms, including bcrypt, are supported. An illustration of utilizing passlib and bcrypt is shown here:
from passlib.hash import bcrypt_sha256
# Hash a password
password = 'my_password'
hashed_password = bcrypt_sha256.hash(password)
# Verify a password
entered_password = 'my_password'
if bcrypt_sha256.verify(entered_password, hashed_password):
print("Password is valid.")
else:
print("Invalid password.")In this illustration, the password is hashed using the bcrypt_sha256.hash() method, which uses the SHA-256 hashing technique as its foundation. The entered password and the previously hashed password are compared using the bcrypt_sha256.verify() function.
Key stretching techniques are built-in to both bcrypt and passlib by default, and they both handle the creation of random salts. By encapsulating low-level cryptographic processes and guaranteeing recommended practices are followed, these libraries streamline the process of secure password storage.
To take advantage of any security updates or improvements, cryptography libraries must be kept current when being used to protect Python data security. To maintain the most secure password storage procedures, check for updates frequently and adhere to the instructions given by the library’s creators.
Use a Static Code Analyzer
Python secure coding benefits greatly from using static code analyzers like PyLint, Bandit, or SonarQube. These analyzers check your codebase for any security flaws and coding errors after installation and configuration. They produce thorough reports outlining problems discovered, such as security holes. You can eliminate risks early in the development process by analyzing and addressing the results. To enable continuous monitoring, it’s advantageous to automate static code analysis within your CI/CD workflow. Its effectiveness is further increased by routinely upgrading the analyzers and adapting rules based on changing security best practices. Static code analysis can help you design more secure Python apps, reduce security concerns, and enhance code quality.
Follow the Principle of Least Privilege
The Principle of Least Privilege (PoLP) is a crucial security principle that encourages giving users and processes only the minimal privileges required to carry out their necessary duties. By upholding this rule, you lower the possibility of unauthorized access, minimize the possible harm from security breaches or privilege abuse, and restrict the exposure of sensitive information or crucial activities. Applying the Principle of Least Privilege requires taking certain actions, such as putting in place stringent access restrictions, separating roles and responsibilities, frequently auditing rights, and using secure development techniques. Adopting this idea would help firms improve their entire security posture and reduce any dangers related to illegal access or excessive privileges.
Also Read: – Top Python Libraries & Web Scraping Tools
Secure Coding Practices in Python According to The Framework
For well-known Python frameworks like Django and Flask, secure coding techniques are important. You may improve the security of your online apps by implementing various best practices. The secure coding guidelines for Django and Flask are broken down as follows for each framework:
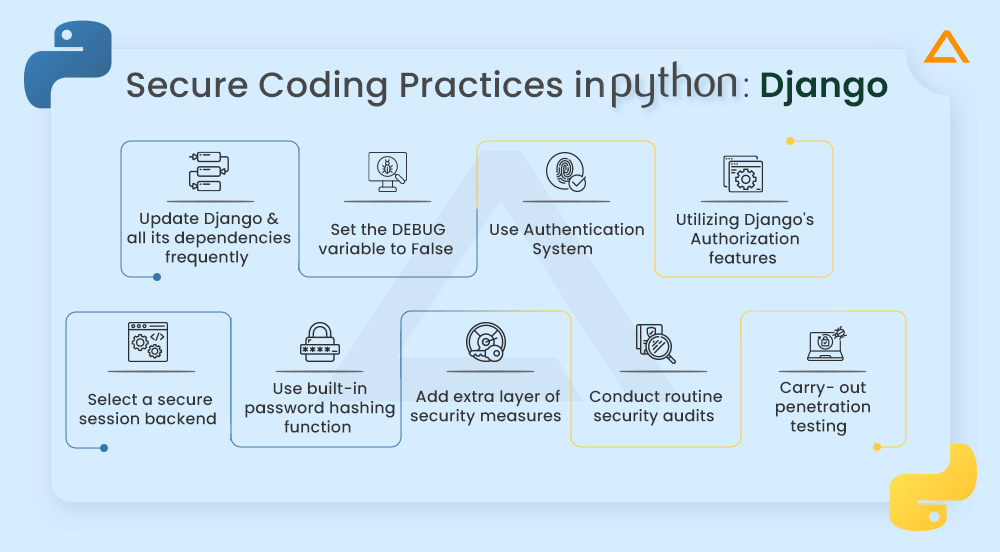
Secure Coding Practices in Python: Django
- For the most recent security updates and bug fixes, you should frequently update Django and all its dependencies
- To turn off debug mode and guard against exposing sensitive data in production situations, set the DEBUG variable in the Django settings file to False
- Make use of the authentication system built into Django, which includes tools for managing users and hashing passwords
- Control access privileges by utilizing Django’s authorization features, including groups and permissions
- Select a secure session backend—such as one that relies on signed cookies or database-backed sessions—and set up the Django settings appropriately
- Use the built-in Django password hashing function, which makes use of the PBKDF2 with HMAC-SHA256 cryptographic method
- Encourage users to use strong passwords, and think about adding extra security measures such as password complexity restrictions
- To find potential vulnerabilities in your Django application, conduct routine security audits using tools like static code analyzers (like Bandit) or security scanners (like OWASP ZAP)
- To examine the security posture of your application, think about participating in penetration testing or security assessments by experts
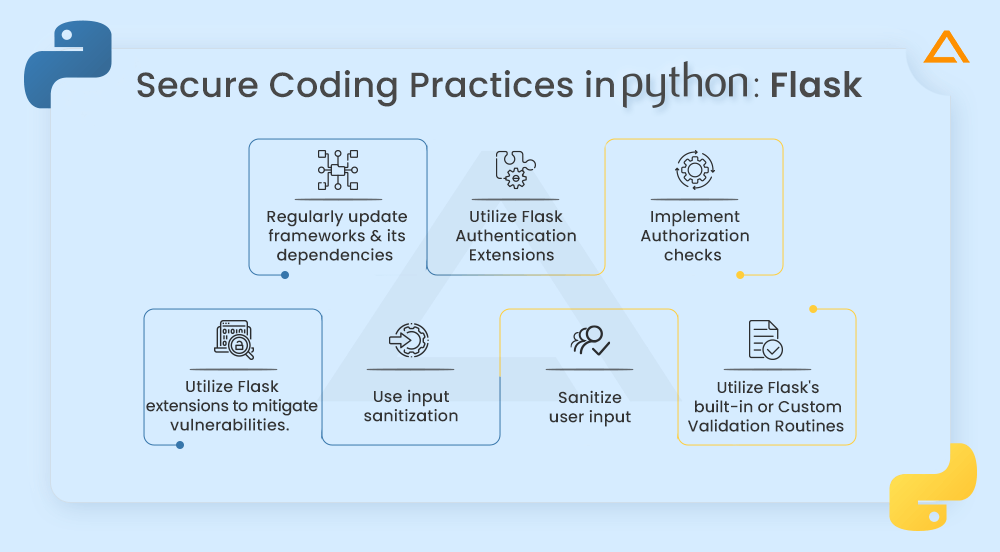
Secure Coding Practices in Python: Flask
- To guarantee you have the most recent security updates and bug fixes, regularly update Flask and its dependencies
- To build safe user authentication, utilize Flask authentication extensions like Flask-login or Flask-JWT
- To make sure users have the necessary permissions, implement authorization checks in your views or endpoints
- Use Flask extensions or libraries to reduce the risk of common vulnerabilities like SQL injection, cross-site scripting, and CSRF
- To thwart such attacks, adhere to Flask’s recommendations for input sanitization and request validation
- To validate and sanitize user input in forms, utilize libraries like Flask-WTF or comparable ones
- Use Flask’s built-in or custom validation routines, then apply the required validation criteria
Python Secure Coding Checklist
When it comes to secure coding practices in Python, following a checklist of best practices can help developers to ensure the security of the applications. Here is a Python secure coding checklist:
- To protect your sensitive data start using these python secure coding practices mentioned above. You can look for suspected areas in your code where there can be the possibility of a security breach
- To guarantee that only authorized users can access critical resources, enforce appropriate permission restrictions, and implement robust authentication techniques, such as multi-factor authentication
- Avoid creating queries by concatenating user input by using parameterized queries or prepared statements to minimize SQL injection vulnerabilities
- It is also important that you perform regular security assessments, penetration testing, and code reviews to identify issues in Python for security
- Another thing that you need to keep in mind is that you should follow the security guidelines such as OWASP and Python Security project for detailed guidelines and best practices specific to Python security
Wrapping Up!
In summary, adherence to secure coding standards is essential for creating robust and reliable Python programs. Developers can reduce vulnerabilities and defend against attacks by adhering to best practices, such as utilizing the most recent Python version, implementing strong authentication and authorization, implementing user input validation, preventing frequent attacks like XSS and CSRF, securely handling sensitive data, and relying on secure coding frameworks.
Ongoing security is made possible by performing regular security testing, reviewing the code, and maintaining current with security recommendations. The confidentiality, integrity, and availability of data can be maintained by developers by giving secure code priority, helping to build trust among users and protect against potential threats.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites.
Also Check:




 Say
Say