Quick Summary:
Microservices architecture provides flexibility, scalability, and the ability to add, remove, or modify software components without affecting the rest of the program elements. Despite their many advantages, microservices are still prone to security vulnerabilities. In this article we will discuss the challenges faced while developing secure microservices as well as best techniques for addressing them.
Enterprise and industry leaders have been increasingly adopting secure microservices to propel their businesses forward over the last few years.
According to Statista, 37% of respondents say they use microservices occasionally, while 34% say they use them frequently.
At this point, tech giants such as Amazon and Google must admit that microservice-style architecture is far more than a fad.
Microservices are becoming increasingly popular as a way to handle complicated, dynamic problems. Secure Microservices make it considerably easier to swap or upgrade components in the middle of a project. It also enables numerous developers to work on separate elements of the project without interfering with one another.
Unfortunately, securing microservices has not progressed at the same rate as their widespread usage. Security risks that develop with microservices provide a challenge to engineers and architects. If these risks are not addressed within the SDLC, the product may become vulnerable.
Let’s start with a definition of microservices before moving on to “How to Secure Microservice Architecture.”
What are Microservices?
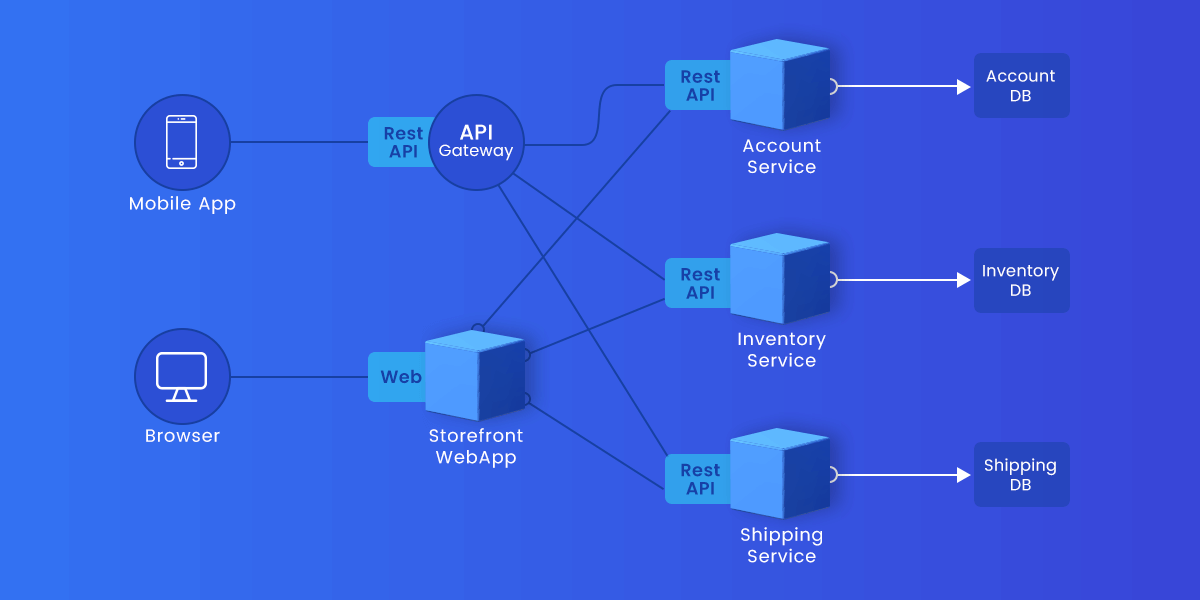
Microservices are a design pattern for developing apps. Microservices are a distributed and loosely connected architectural framework. As a result, modifications made by one team member have no bearing on the entire team’s work. Using safe microservices has the advantage of allowing development teams to build new app components to suit changing business needs quickly.
A microservice is a core function of an application that runs independently of other services. However, a microservice architecture is about more than just loosely coupling the app’s core features; it’s also about restructuring development teams and inter-service communication in a way that accounts for inevitable failures, future scalability, and new feature integration.
What are the Main Benefits of a Microservices Architecture?
Through distributed development, Secure Microservices gives your teams and procedures a boost. You can also work on numerous microservices at the same time. This means that more developers will be working on the same software simultaneously, which will result in a shorter development period.
Advantages of Secure Microservice Design
1. Faster Market Time
Microservices design allows for more agile deployment and upgrades because development cycles are shorter.
2. Highly Scalable
As demand for certain services grows, you can deploy across multiple servers and infrastructures to meet your needs.
3. Resilient
When properly developed, these autonomous services do not affect one another. Unlike the monolithic app approach, this implies that the entire app does not go down if one piece fails.
4. Easy to deploy
Because microservice-based programs are more flexible and smaller than traditional monolithic apps, the concerns associated with their deployment are eliminated. More coordination is required, which a service mesh layer can assist with, but the benefits can be enormous.
5. Accessible
Because the bigger software has been split into smaller bits, developers can better understand, update, and upgrade individual pieces, resulting in shorter development cycles, especially when using agile development approaches.
6. More Open
Because multi-user APIs are used, developers have the freedom to use the best language and technology for the task at hand.
Microservice Architecture vs. Monolithic Architecture
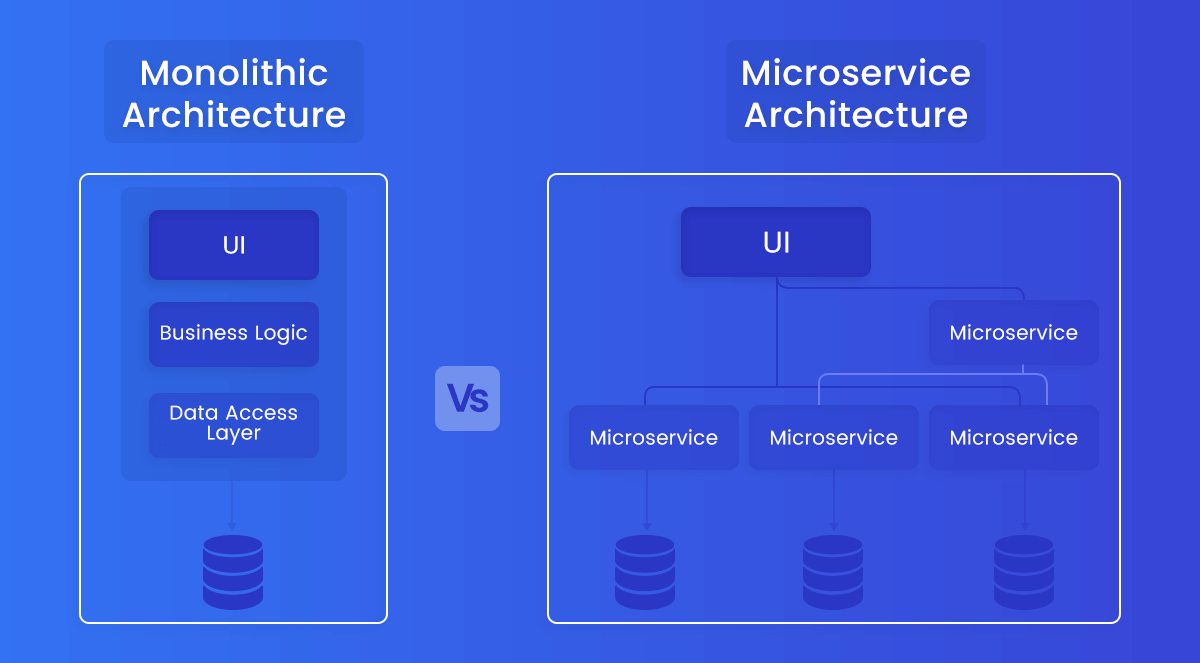
Microservices architectures contract with traditional monolithic application models. Monolithic applications are structured as a single-tier, making them easier to set up quickly and integrate reliability with the well-known integrated development environment (IDEs), framework, and tools.
Microservices architecture, on the other hand, breaks it down into a collection of smaller independent units. These units carry out every application process as a separate service. As a result, all the services have their logic and database and perform specific functions.
However, these smaller independent deployable distinct services increase the number of components hence complexity and difficulty securing them. Usually, a typical microservices deployment will have the hardware, service or application, communication, c; loud, virtualization, and orchestration layers. Each of these has specific security requirements, control, and challenges.
Security Challenges Associated With Microservices / Privacy Issues In Microservices Architecture
If you are thinking about shifting to the microservices architecture, the following are the security challenges that you should keep in mind.
1. Organizational & Cultural
If the organization is shifting towards microservices, it will change how people work, not just apps. These are recognized as challenges as each team will have its deployment cycle and responsibility for unique services. It may not look typical developer’s concern, but it is essential for successful, secure microservices architecture.
2. Building
You must devote time to identifying interdependencies among your services. Because of the interdependence, the compelling one build may activate numerous more builds. It would be best if you also thought about how microservices will affect your data.
3. Testing
End-to-end testing, as well as integration testing, might become more challenging and crucial than ever before. Know that depending on how you’ve designed your services to support one another, a failure in one section of the architecture could cause anything a few hops away to fail.
4. Versioning
Keep in mind that updating to newer versions may compromise backward compatibility. You can manage this with conditional logic, but it quickly becomes bulky and ugly. You may also set up various live versions for different clients, but this might be more difficult to maintain and manage.
5. Deployment
Yes, this is a challenge, at least in the beginning. To make deployment easier, you’ll need to invest in a lot of automation because the complexity of microservices is too much for humans to handle. Consider how and in what order you will roll out services.
6. Logging
To bring everything together in distributed systems, you’ll require centralized logs. The scale would otherwise be hard to manage.
7. Monitoring
To spot sources of problems, it’s necessary to have a centralized perspective of the system.
8. Debugging
Remote debugging through your local integrated development environment (IDE) isn’t possible, and it won’t operate over dozens or hundreds of services. At present, there is no one-size-fits-all solution for debugging.
9. Connectivity
Consider consolidated or integrated service discovery.
Best Practices in Implementing a Secure Microservices Architecture
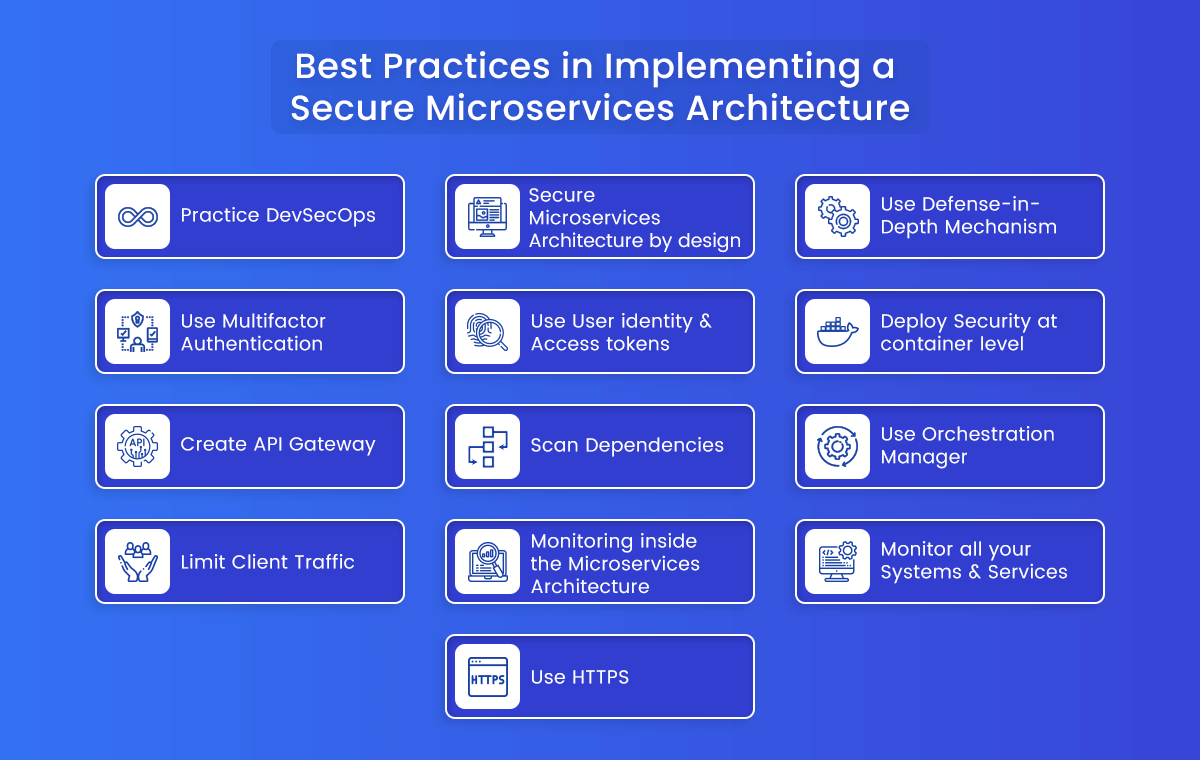
1. Practice DevSecOps
Integrate Security into the development and deployment of microservices from the beginning. This addressing security method is simple, effective, and less expensive than waiting until the program development is nearly complete. Like all the components in the DevSecOps approach, microservices Security requires practice and DevSecOps tools. This includes shifting Security left by integrating application security testing tools into the entire DevSecOps process.
2. Secure microservices architecture by design
Developers must integrate layers of Security in applications to protect the data they carry, just as building workers must strategically stack and build a robust foundation. Creating a secure microservices architecture necessitates keeping Security in mind at all stages of development. This entails establishing a type of continuous stress testing on architecture while writing code, and this entails continuous integration (CI) and continuous delivery (CD).
This can be accomplished by running security unit tests like static analysis security testing (SAST) and dynamic analysis security testing (DAST) at the same time:
- SAST will find vulnerabilities in both your code and the libraries you use. It works from the inside out, and therefore you’ll need a scanner that supports your programming language.
- DAST identifies weaknesses by simulating hostile attacks from the outside. It does not require a specific language, unlike SAST.
3. Use Defense-in-Depth Mechanism
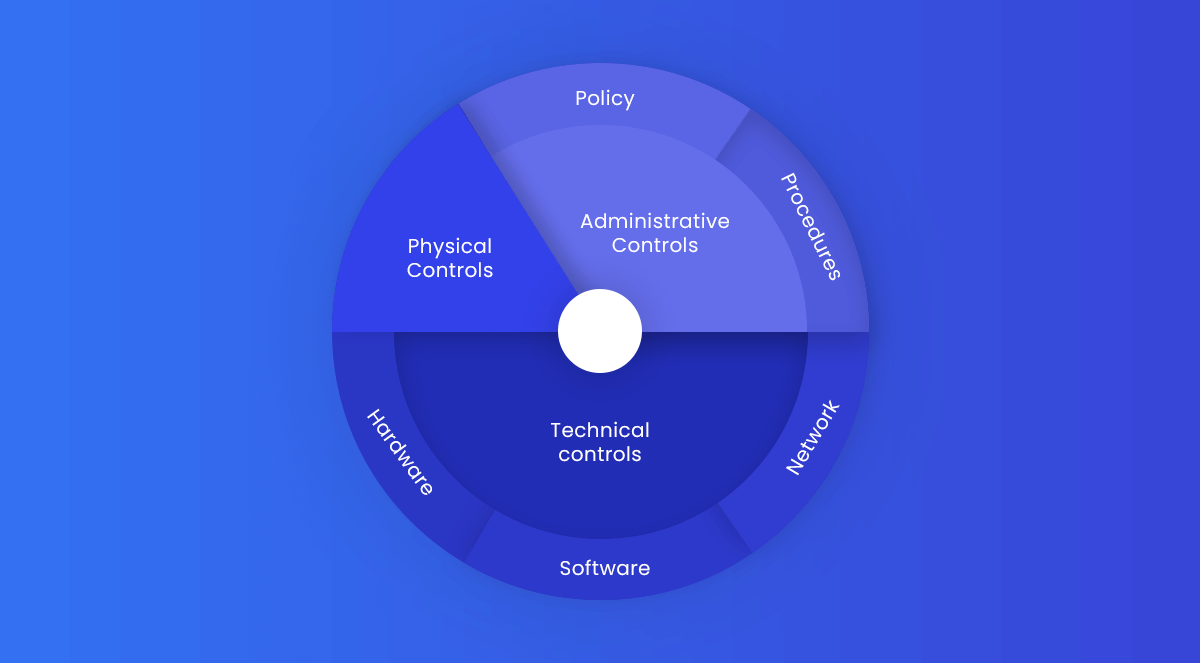
Defense in depth is an important approach to employ. Gone are the days when a single firewall-protected your monolithic system. Defense in depth is a security technique in which many layers of security controls are implemented throughout an organization’s software systems. The services with the most sensitive data require several and variable layers of protection in the context of microservices.
4. Use Multifactor Authentication
The front-end security is improved by enabling multifactor authentication. Users will be required to provide their login and password, as well as an additional form of verification, such as a code issued to their phones or an email address. Because they won’t be able to give the second authentication, attackers who may be utilizing stolen or hacked credentials will have difficulty accessing the microservices. Authentication and authorization in a microservices architecture create an extra layer of Security on the architecture.
5. User identity & Access tokens
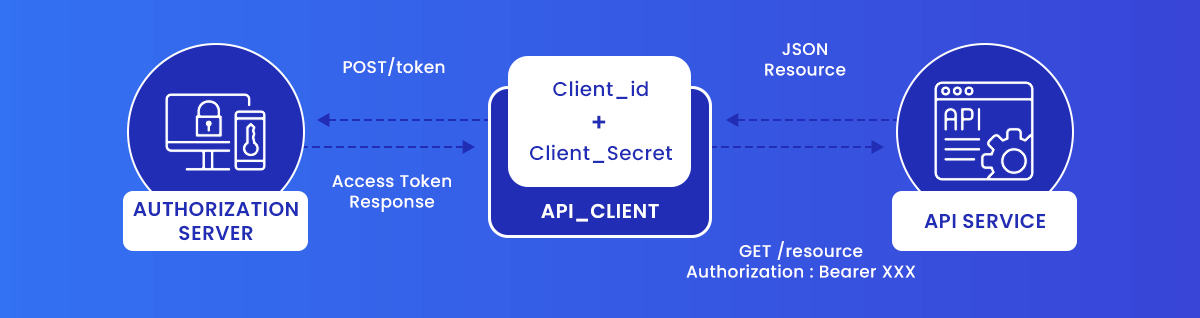
When it comes to securing microservice endpoint security, authorization in a microservices architecture, and authentication are all vital components of a solid microservice strategy. In a microservices architecture, using OAuth/OAuth2 in microservices architecture for user authorization is suggested. Multifactor authentication is also vital for both prevention and detection when it comes to securing your application. It assists in blocking malicious players and offers information on when the breach occurred.
6. Deploy Security at Container Level
Microservices often use container technology. As a result, one method of decreasing the attack surface and risk is to secure the container internally and externally. Aiming for the least privileged security concept is a desirable practice that necessitates a combination of tactics that include, but are not limited to:
- Limiting authorization to the bare minimum
- Avoid utilizing Sudo or privileged accounts to launch services or anything else.
- Avoid data theft or compromise by limiting access to available resources.
- Secrets should not be kept on the container disc.
- Isolate access to resources using appropriate rules.
7. Create API Gateway
APIs are one of the most susceptible aspects of microservices design. Building API gateways is crucial for putting together microservices. Security best practices, especially when dealing with several microservices. These APIs provide a single entry point for external requests, preventing bad actors from gaining direct access to microservices and preventing potential attacks.
8. Scan Dependencies
The majority of today’s software is made up of third-party and open-source components. Various dependencies are included, which are impossible to track manually. When a dependency contains a security flaw, this becomes a problem. To detect and resolve security vulnerabilities as quickly as possible, it’s critical to track third-party and open-source components, as well as all of their dependencies.
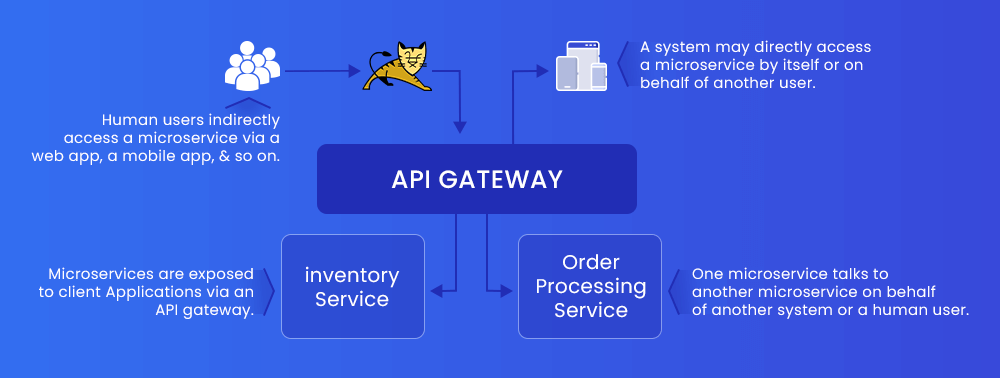
Typical API gateways include NGINX, Kong, Tyk, Ambassador, AWS API gateway, and more.
9. Use Orchestration Manager
In addition to boosting security, orchestrations managers allow you to automate configuration, coordination, and other microservices administration duties. The tools usually let you manage many containers, limit metadata access, different workloads, collect logs, and so on. In addition to boosting security, orchestrations managers allow you to automate configuration, coordination, and other microservices administration duties. The tools usually let you manage many containers, limit metadata access, different workloads, collect logs, and so on.
The following are the two most regularly utilized methods:
- Using microservices to code the orchestration.
- Using API gateways to give a layer of orchestration
Due to the challenges of scaling services, orchestration using an API gateway is not recommended. Typical orchestration management tools include Kubernetes, Istio, Azure Kubernetes Service (AKS), etc.
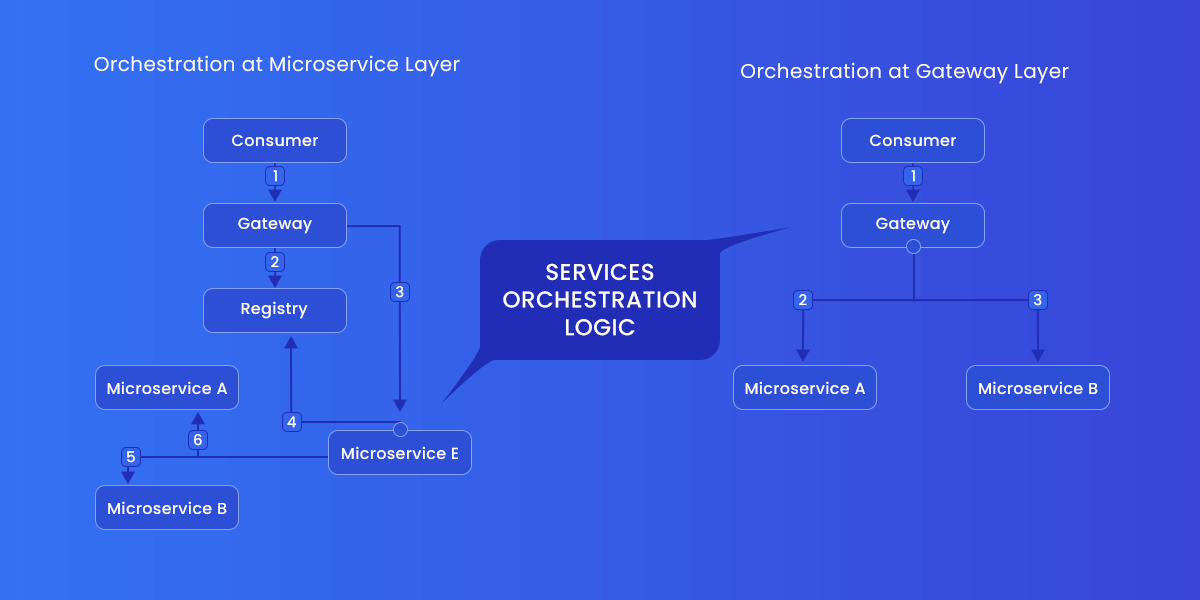
10. Limit Client Traffic
Denial-of-service attacks can be avoided by limiting external traffic. Also, there are times when a few clients absorb all of the bandwidth. One method uses multiple policies to monitor and regulate the amount of traffic transmitted and received from a client based on IP, time, and other factors. It’s a good idea to set your services to slow down if they notice several failed API login attempts or other suspicious activities.
Due to the slow system, an attacker may abandon their effort to access the service. You can use code or other methods to rate limit your API, and most SaaS setups have API rate limitations in place to prevent both user and attacker abuse.
11. Monitoring inside the microservices architecture
Monitoring internal systems and services using some of the best practices and techniques. The following are some of the best practices:
- Logging should be enabled in the application layer. Splunk, Graphana, the ELK stack, and other log collection tools can be used at the application, container, network, and infrastructure levels.
- Keep track of the utilization statistics.
- Look for patterns in metrics such as CPU, RAM, response time, faults, notification, and others to spot abnormal activity or possible attacks.
- Examine logs in incoming client requests, database records, containers, and others to look for abnormal or inconsistent behavior.
12. Monitor all your systems and services
Because microservices are based on a distributed system, you’ll need a dependable and effective monitoring method for each component. Continuous monitoring enables you to spot and respond to security threats before they cause harm. A wide range of monitoring solutions is available to detect and address the security risk, including Prometheus, Statsd, InfluxDB, Logstash, etc.
13. Use HTTPS
Enforce HTTPS for all communication to protect data in transit and encrypt data at rest. Avoid sending sensitive data, passwords, and other data in plain text that is stored in code. The ideal technique to become more cloud-native and distributed. Although this may appear to be a basic idea, it is critical to constantly apply it as a foundational aspect to both internal and external networks.
When it comes to implementing security infrastructure, common attacks such as phishing and credential stuffing are on top of IT professional’s minds. While mitigating the attacks that originated within your network is also important, this can be achieved by implementing HTTPS across the microservice architecture.
Officially known as Transport Layer Security (TLS), HTTPS ensures privacy and data integrity nu encrypting communication over HTTP. HTTPS requires a certificate to authenticate your identity and provide access to encrypted communication via Public key infrastructure. Once the certificate is acquired, you can continue to enhance your Security using automatic certificate generation and renewals, keeping attacks at bay.
When To Go For Microservices Architecture?
- Building a microservice application without the right skills and knowledge is extremely dangerous. Even yet, having a basic understanding of architecture is insufficient. Because DevOps and Containers are so closely linked to microservices, you’ll require professionals in both. Expertise in domain modeling is also required. When dealing with microservices, the system is divided into different functions, and responsibilities are divided.
- An application that is both complicated and scalable. Scaling and adding new capabilities to your program will be considerably easier with the microservices design. So, if you’re planning to build a massive app with several modules and user journeys, the microservice paradigm is the way to go.
- There are sufficient engineering talents. You’ll need adequate resources to manage all of the activities in a microservice project because it involves many teams that are accountable for different services.
When Not To Use Microservices Architecture?
Extra complexity
Because a microservices architecture is a distributed system, you must choose and configure all modules’ and databases’ connections. Furthermore, if an application includes independent services, each one must be deployed separately.
System distribution
Because a microservices architecture is a complicated system with many modules and databases, all connections must be carefully managed.
Cross-Cutting concerns
You’ll have to deal with a variety of cross-cutting issues when developing a microservices application. Externalized configuration, logging, metrics, health checks, and other features are among them.
Testing
Testing a microservices-based solution is substantially more difficult due to a large number of independently deployable components.
Also Check:


 Say
Say