Quick Summary:
Java applications can be vulnerable to various security threats if not properly secured. This blog covers a wide range of secure coding guidelines that equip developers and organizations with the knowledge and strategies to protect their Java applications. Which helps them against common vulnerabilities and Zero-day attacks, fostering a robust and secure software environment.
In this digital landscape, security is paramount, and Java applications are no exception. Ensuring the security in java applications is a critical concern for developers and organizations. This blog explores Java coding best practices, offering insights and recommendations to fortify your applications against a wide range of threats. From authentication and secure communication to handling error correctly and monitoring, these safe coding practices are your foundation for creating robust and secure Java software. Whether you’re a seasoned developer or just starting, understanding, and implementing these secure coding practices checklist is essential in safeguarding your Java applications and the data they handle.
However, security in Java coding is just one piece of the puzzle, there are many software platforms which rely heavily on Java for there tasks and can only be protected if they are properly patched or updated.
For example, there is a common theme across the popular platforms such as Java RMI (it’s a function available over a network), Atlassian Confluence (a collaboration platform), and VMware Horizon (a virtualization platform). What you might ask? The answer is they all are victim of attacks exploiting Java Vulnerabilities.
It is important to note that they all provide vital services but they all have been subject to numerous exploits over the year, and allowing remote code execution (RCE) specially confluence and horizon. This highlights the role that Java security plays in their operations.
Let’s look at the stats to understand the severity of these vulnerabilities better.
- According to Checkpoint 2022, can be known for the massive Java zero-day vulnerabilities. With vulnerabilities such as Log4Shell & Spring4Shell (also known as younger sibling of Log4Shell). Usually, Java vulnerabilities exploits the loop holes in widely used Java libraries and make them vulnerable to the attacks such as Remote Code Execution (RCE). Once the application is vulnerable to the attack, it opens the backdoor for various threats that bring down the entire organization.
- According to Statista, The average cost of a data breach in the United States rose from 9.05 million dollars in 2021 to 9.44 million dollars in 2022. In 2022, the average cost per data breach throughout the globe was 4.35 million dollars.
These stats will help you understand the significance of security in SDLC, if you’re overlooking the security while developing an application it can seriously affect the robustness of the entire application.
We have compiled the list of top Java Security Best Practices. To provide a foundation for secure programming in Java. By following these secure coding guidelines, you’ll be well on your way to building secure software that will stand up against vulnerabilities in development stage or even after will provide you an extra layer of security.
Let’s begin with the Java Security Best Practices!
Java Security Best Practices
By keeping in mind, the following techniques, Java developers will be less likely to introduce security flaws, and they will also aid in preventing known malicious attacks.
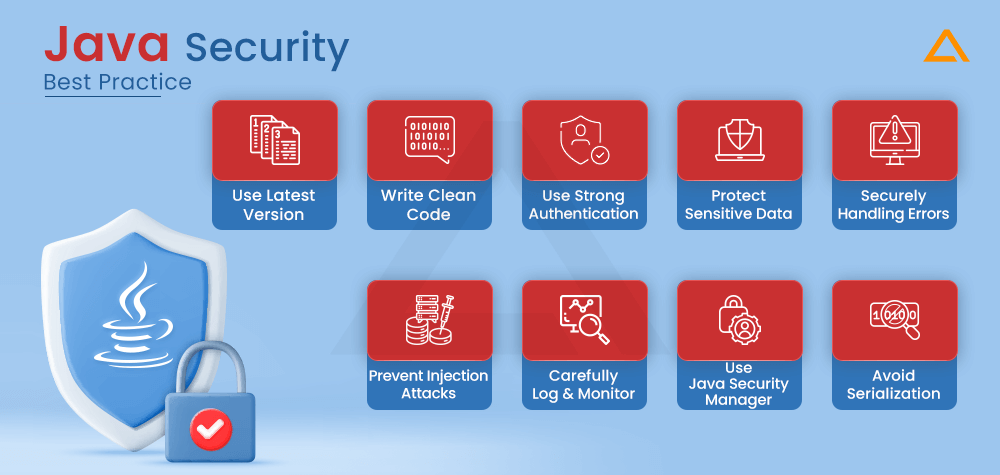
- #1. Always use the latest version & Update Regularly
- #2. Write Clean and Concise Java Code
- #3. Establish Robust Authentication Measures
- #4. Safeguard Sensitive Information
- #5. Securely Handling Errors
- #6. Prevent Injection Attacks
- #7. Comprehensive Logging & Monitoring
- #8. Harness the power of Java Security Manager
- #9. Avoid Serialization
Let’s look at them in detail starting with the first on the list of Java secure coding practices.
#1. Always use the latest version & Update Regularly
First in the list of Java best practices is always using the latest version of Java. Using the most recent stable and supported version of Java is one of the most important best practices for securing Java applications. Older, outdated versions of Java contain many known vulnerabilities that attackers can exploit. New versions typically include the security patches to address the latest vulnerability related to the version. Therefore, all developers must upgrade to the new Java versions as soon as possible whenever updates are available. It will provide you with an extra layer of protection against the security threats.
Additionally, you should subscribe to Java security bulletins and mailing lists to stay informed about new threats and available patches. Staying completely up-to-date with Java releases is the easiest and most effective way to ensure you are protecting against the latest security risks.
#2. Write Clean and Concise Java Code
Next, on our specially curated list of Java best practices is writing the clean code. Writing clean, concise Java code is critical for developing secure Java applications. Be sure to follow secure coding best practices like input validation and principle of least privilege to avoid introducing vulnerabilities. Refactor continuously to remove unnecessary code and minimize attack surface area.
Modularize code into small, focused units that do one thing well. Use descriptive naming conventions and proper formatting to make code self-documenting. Avoid over-complex code with deeply nested conditionals and loops as it conceals logic and hides bugs. Regularly use dependency checking tools to identify outdated libraries with known flaws.
To find issues proactively, perform code reviews, static analysis scans, and dynamic analysis frequently. Well-structured, minimal code is easier to analyze for security bugs and maintains a smaller surface area for attacks. With some diligence, you can prevent many vulnerabilities through proper secure coding techniques that optimize Java code for simplicity, readability, and security.
#3. Establish Robust Authentication Measures
Next in the Java best practices list is using access control. Implementing secure authentication is critical to ensure only authorized users can access protected resources and functions. Use robust protocols like TLS 1.2+ with modern ciphers for encrypting all authentication data in transit. Require strong passwords hashing adhering to complexity rules with a minimum length, expiration, and account lockouts to prevent brute force attacks.
Enable multi-factor or two-factor authentication for accounts whenever feasible. Issue unique session IDs on each new login, bind them to the authenticated user, and set short timeout periods before expiry. Renew session IDs periodically to mitigate session hijacking risks. Disable caching and autofill for password fields. Log all authentication events like failed logins for analysis and intrusion detection.
With proper authentication you can effectively verify users and defend against account takeovers, replay attacks and other identity-based vulnerabilities.
#4. Safeguard Sensitive Information
Properly protecting sensitive data is imperative for security is one of the most important Java best practices. Start by classifying data as sensitive or non-sensitive to determine appropriate protection levels. Avoid collecting and storing sensitive data like passwords, encryption keys, PII, etc. unless necessary for business functions.
If required, encrypt such data at rest and in transit using strong standard algorithms like AES-256 and secure key management. Hash passwords with bcrypt or similar adaptive algorithms. Mask or truncate sensitive data when displayed. Enforce need-to-know access controls through roles, groups, privileges etc. Restrict access to only authorized individuals.
Disable caching for secure pages containing sensitive info. Regularly remove the data no-longer needed for compliance. Applying robust data protection measures through encryption, hashing, key management, access controls and secure cleansing will help mitigate the impact of data breaches involving sensitive information.
#5. Securely Handling Errors
Proper error handling is vital for maintaining security. Do not expose technical details like stack traces or debugging information to end users – these aid attackers. Display generic error pages and log any errors with sufficient context for investigative purposes, but scrub any sensitive data that could lead to exploits. Additionally, ensure that you have robust practices in place to debug Java applications efficiently when necessary.
For potential leaks, examine error handling in all components including app servers, databases, APIs, etc. Handle exceptions cleanly within the application code to avoid revealing internal structure. Monitor for any sharp spikes in different error types that could reflect reconnaissance. Log errors securely and analyze them regularly to identify suspicious anomalies proactively.
Follow secure coding best practices and apply well-designed error handling mechanisms that avoid information leaks while providing support teams the right insights make applications more resilient and harder to penetrate. Think through error handling just as carefully as any other security mechanism.
#6. Prevent Injection Attacks
Injection attacks like SQL injection and cross-site scripting can severely compromise Java application security. Always use prepared statements with parameterized queries to prevent embedded SQL injection attacks. Validate and sanitize all user-supplied input before passing it to queries. Encode or escape special characters when outputting data to prevent XSS attacks.
Utilize the secure coding best practices in your Java application and set security headers like XSS-Protection. Limit use of interpreters and disable unused ones to protect against command injection. Implement input validation libraries and scanner tools to catch issues early. Monitor for errors and anomalies that may indicate injection attack attempts. Well-structured code and vigilant input handling will stop malicious input from being interpreted as commands or code. It’s worth considering the option to hire Java developers who are well-versed in secure coding practices, testing, and monitoring to further strengthen your defense against code injection. Protecting against code injection should always be a top priority.
Also Read: – Top Java Framworks to use
#7. Comprehensive Logging & Monitoring
Robust logging and monitoring are crucial for detecting and investigating security events. Log key events like sign-ups, high value transactions, logins and policy change,etc. but avoid sensitive data like passwords. Stream or ingest logs from all systems and layers into a secured central log management system. Enable active monitoring capabilities like IDS/IPS systems to check for anomalies and known attack patterns in real-time.
Configure alerts to notify on potential security events like bursts of failed logins, rate limit violations etc. Perform log analysis regularly to identify unusual access patterns that may reflect attacks. Retain activity trails per compliance requirements but purge old logs periodically.
Comprehensive activity logs provide visibility into user actions and application usage that is essential for swift incident response, forensic analysis and identifying emerging threats.
#8. Harness the power of Java Security Manager
The Java Security manager is a powerful tool that enforces the access control at run-time-based security policies. It determines which resources code executing in Java can access such as files, network connections, external processes, etc.
Sandbox the untrusted code and run it under the restrictive security policy that blocks permission. Developing the fine-grained security policy that grants only permission required by the code to function properly is advisable. Disable access to sensitive APIs and libraries if not expressly needed. Set specific runtime permissions for code based on factors like its source and whether it is digitally signed.
Extend the security manager by writing custom permission checks where required. To Leverage the Java Security Manager and its ability you should hire Java developers who can put constrains on untrusted code through strict policies is a key safeguard against malware and unauthorized resource access
#9. Avoid using Serialization
It is a practical choice to avoid serialization in software development, especially for applications requiring efficiency, security, and long-term maintainability. Serialization is a process that converts the complex data structures into the format suitable for transmission and storage, but it also opens doors to some problems.
- First, it can be resourcing consuming operation, as it can eat up your valuable resources such as CPU cycles and memory.
- Second, it can lead to compatibility issues sue to the older version program. Most importantly it can cause a serious security concern if not implemented correctly. This can make them vulnerable for the potential data tampering and injection attacks. Because of this oracle has also announced their long-term plans to drop the functionality, emphasizing the importance of adopting the more efficient and robust alternatives.
Let’s move towards the TL;DR version and review what we have understood till now !
TLDR version
You can turn your plain old Java code into the secure code using the following Java secure coding practices. Implement these top Java best practices and secure your app against the security threats that may arise.
| Java Secure Coding Practices | Description |
| Use latest version and update regularly | ♣ Use latest and stable version of Java ♣ Update it with security patches |
| Write clean and concise code | ♣ Keep interactions limited ♣ Use tested libraries & frameworks ♣ Refactor your code ♣ Minimize your code size |
| Use Robust Authentication measures | ♣ Use security protocols such as TLS ♣ Utilize password hashing ♣ Use multi-factor authentication ♣ Renew session IDs periodically ♣ Log all authentication events |
| Protect sensitive information | ♣ Classify your data ♣ Use encryption ♣ Hash the passwords ♣ Do secure cleaning ♣ Apply key management |
| Proper Error Handling | ♣ Keep error messages generic ♣ Monitor different error types ♣ Handle exceptions cleanly ♣ Log messages wisely |
| Prevent Injection attacks | ♣ Sanitize user input ♣ Limit interpreters use ♣ Implement input validation ♣ Set security headers |
| Comprehensive Logging & Monitoring | ♣ Use Log Management Systems ♣ Utilize IDS/IPS ♣ Perform log analysis ♣ Purge old logs periodically |
| Use Java Security Manager | ♣ Access control tool ♣ Restrict the permissions |
| Avoid using Serialization | ♣ Can introduce vulnerabilities ♣ Be careful while using it ♣ Switch to another alternative |
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites
Wrapping up!
This brings us to the end of Java Security best practices; we have curated list of 9 top secure coding practices that should be kept in mind while developing a secure Java application. In summary, it’s crucial to prioritize Java best practices to ensure the safety of your applications and data.
This involves:
- Keeping Java Updated
- Employing Secure Coding Techniques
- Establishing Strong Authentication And Authorization Protocols
- Configuring Components Correctly
- Effectively Implementing Encryption
- Following The Principle Of Least Privilege
Above all are indispensable components of a robust security strategy. Lastly, pay attention to the significance of maintaining dependency security and practicing secure coding practices to achieve comprehensive protection.




 Say
Say