Quick Summary:
IT risk management is an imperative process that needs to be strategized alongside your digital transformation journey. To truly get the most out of cloud hosting services and enterprise mobility solutions, you must set up a proper enterprise risk management program. Here is a definitive guide on risk identification, assessment, mitigation and other relevant processes to ensure proper enterprise risk management for your IT processes.
Information risk or IT risks refer to any potential threats or vulnerabilities that can adversely impact any business’ information technology infrastructure, data, intellectual property and operational capabilities.
IT risk management is identifying, assessing and controlling such potential IT threats and vulnerabilities to minimize the impact, ensure improved resilience towards cyberattacks, stabilize business operations, and safeguard sensitive organization & customer data.
The cost borne by the victims of cyber-attacks or IT risks are limited to the investment needed in setting up ITRM (IT Risk Management) best practices and processes and the time it takes to recover from the loss of data, infrastructure, time and other such aspects.
Stats Showing the Importance of IT Risk Management in Today’s World
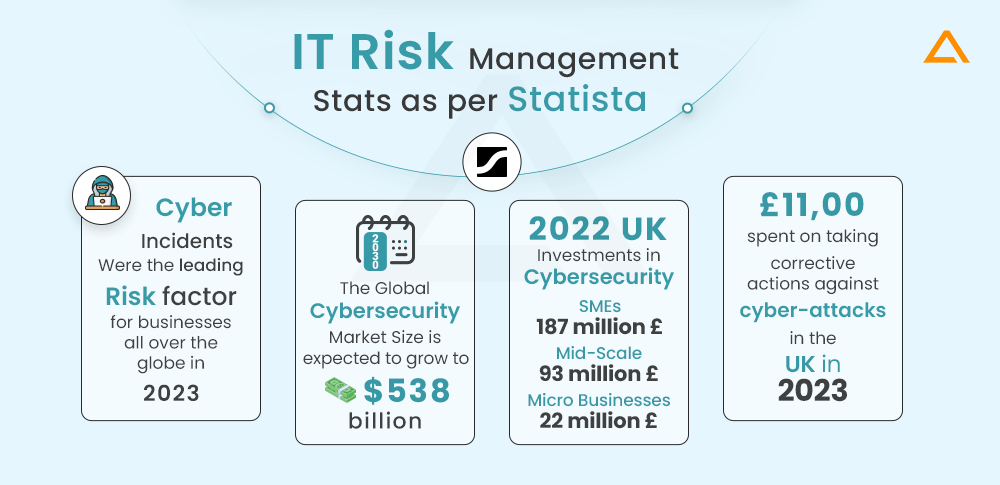
IT Risk Management Stats as per Statista –
- Cyber incidents were the leading risk to global businesses in 2023, as per a survey conducted by risk management experts in late 2022
- The Global Cybersecurity Market is forecasted to grow to $538 billion by 2030
- In 2022, small companies in the United Kingdom invested over 187 million British pounds in the cybersecurity sector. Mid-scale businesses spent 93 million, whereas micro-businesses spent around 22 million
- The cost of taking corrective actions against cyber-attacks in the UK totalled 11,00 British Pounds across all businesses in 2023
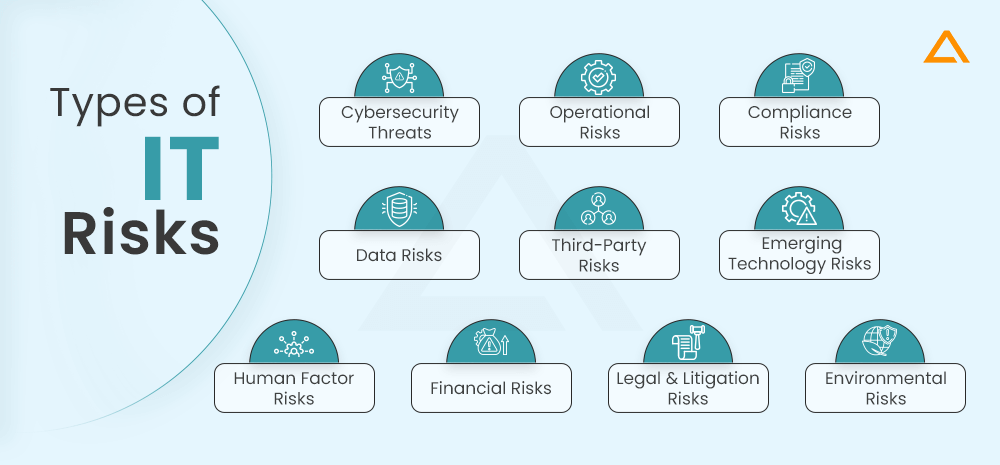
Information Risk Categorization – Types of IT Risks and Level of Risk Control
Information Risks are generally categorized as – Cybersecurity Threats, Operational Risks, Compliance Risks, Data Risks, Third-Party Risks, Emerging Technology Risks, Human Factor Risks, Financial Risks, Legal and Litigation Risks, and Environmental Risks. Such categorization can help in the Risk Identification process, allowing cybersecurity experts to match the right IT risk management solutions, including Risk Management Tools and Software, to your project.
Here is a quick explanation table to get a basic idea about different types of Information Risks –
| Types of IT Risks | Explanation | Intent | Risk Control Assessment |
| Cybersecurity Threats | Risks regarding hacking, malware, and phishing attacks | To compromise confidentiality, availability or integrity of targeted IT data and systems. | Moderate to High |
| Operational Risks | Risks arising from internal processes, human errors or system failures. | Unintentional, no malicious intent. | Moderate |
| Compliance Risks | Risks emerging from non-compliance with relevant industry-specific or regional regulations like HIPAA and GDPR. | Oversight, inadequate IT risk management processes in place. | High |
| Data Risks | Risks regarding security, privacy and integrity of data. Possibility of data loss, breaches, privacy violations and quality issues. | It could be intentional, like data breaches, oversight, or data quality issues. | Moderate to High |
| Third-Party Risks | Risks associated with dependency on external sources such as third-party vendors, suppliers, and service providers may cause vulnerabilities or operational hurdles. | Their security standards are unintentional, resulting from the performance or oversight of associated third-party vendors. | Moderate |
| Emerging Technology Risks | Risks arising from improper adoption of next-gen technologies such as IoT, AI and cloud-based computing. Vulnerabilities can arise from integration challenges and potential technology obsolesce. | Unintentional, impacted by improper digital transformation solutions. | Moderate |
| Human Factor Risks | Risks result from employee actions such as oversight, poor performance, insider threats, etc. | It could be intentional or unintentional. | Moderate |
| Financial Risks | Risks of exceeding the pre-defined IT project budget or not matching the expected ROI mark. Effective IT strategy and consulting are needed to mitigate such risks. | Mostly unintentional due to improper financial planning or sudden budget constraints. | Moderate |
| Legal and Litigation Risks | Risks arising from Legal disputes, IP rights violations, and regulatory fines related to IT services. | Could emerge from disputes, violations, and IP infringement. It could be intentional or unintentional. | Moderate to High |
| Environmental Risks | Risks associated with environmental factors or unforeseen natural disasters that could impact IT infrastructure. | Unintentional and mostly beyond human control. | Low |
What is IT Risk Management? Benefits of Implementing IT Risk Management Solutions
IT Risk Management, often regarded as ITRM, applies best risk management practices to manage IT security vulnerabilities and risks and reduce their impact on your IT infrastructure, sensitive data and other business processes. It focuses on implementing various IT risk management methods to mitigate, manage and foresee potential IT threats.

There are essentially four broad categories or processes in an effective IT risk management process – Risk Identification, Risk Assessment, Risk Mitigation, Risk Monitoring and Reporting.
You can also leverage some of the most established IT Risk Management frameworks to ensure comprehensive coverage of your IT risk management efforts. In the coming sections, we will discuss the processes and these risk management frameworks in greater detail.
But before we get to that, let’s address Why IT risk management is critical. What is its purpose?
Benefits of Investing in IT Risk Management for Businesses in 2024
As we already saw, businesses across the globe are investing heavily in IT risk management practices. Also, since almost all business practices and industries depend heavily on technology, the significance of effective IT risk management practices has increased tremendously. From data breaches to cyberattacks and regulatory compliance, businesses need to safeguard their digital infrastructure proactively. Moreover, implementing IT risk management best practices also helps improve business efficiency and other benefits such as –
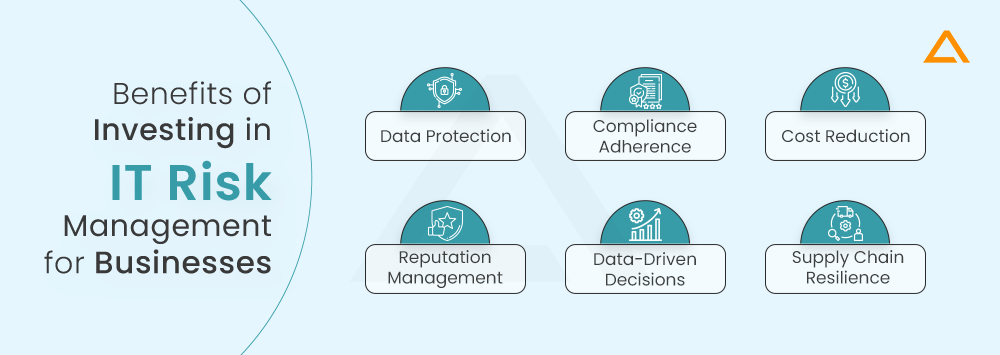
Data Protection
IT Risk Management helps safeguard sensitive data from unauthorized access, data loss, security breaches and more. This helps protect and uphold the integrity and confidentiality of sensitive information.
Compliance Adherence
Proper IT risk assessment and management ensures compliance with relevant industry regulations, data protection laws and security standards, which helps reduce the risk of penalties and legal consequences.
Cost Reduction
Proper IT security assessment can help identify key problematic areas in your business processes that might be the most vulnerable to threats and attacks. Proactively finding such loopholes and weak spots can significantly prevent costly IT incidents, reducing the chances of unforeseen and expensive repairs.
Reputation Management
Effective Information Security Risk Management protects a company’s reputation by preventing data breaches and other IT-related attacks like man-in-the-middle, cross-site scripting, etc. This helps maintain trust and reliability with other stakeholders regarding clients, partners and others.
Data-Driven Decisions
Effective IT risk mitigation strategies provide significant insights regarding IT-related decisions that help the top-level management make data-driven decisions based on organization goals and focus areas.
Supply Chain Resilience
If your business has a supply chain, your data or business processes can be compromised due to different vendors involved in the supply chain if any of their data gets compromised. Hence, effective Vendor IT Risk Management processes help to reduce business disruptions significantly, ensuring a smoother flow of business processes.
Steps of Implementing Information Security Risk Management Process
IT risk management is a systematic process that follows an overall flow of identifying, assessing, and monitoring potential risks associated with any organization’s IT infrastructure and business operations. Let’s break down the process of implementing a comprehensive, practical and fully covered IT risk management process –
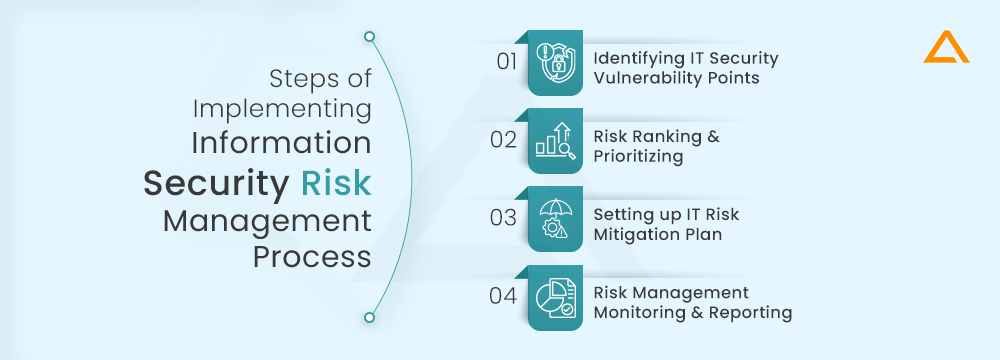
Step 1 – Identifying IT Security Vulnerability Points (Risk Identification)
![]()
Things to know about IT Risk Identification
1. What happens in IT Risk Identification?
IT professionals collaborate with business owners/stakeholders to identify risks like cybersecurity threats, software vulnerabilities, hardware failures and compliance gaps.
2. What kind of IT Risks can be identified?
IT Risks can be both internal and external. Internal errors can be employee or system failures, whereas external IT risks can be malware, cyber-attacks and other exploitations.
3. What are the most common IT Risks Approaches?
Surveys, Audits and Analysis of Threat Intelligence.
How to Conduct a Successful IT Risk Identification Analysis?
Just like an effective healthcare diagnosis and identification of the root cause that’s causing the problem, finding the vulnerable areas in your IT infrastructure and digital processes is the first step towards a successful IT risk management effort. Here are a few steps you can undertake to ensure complete coverage of your IT infrastructure inspection –
- Make a list of all IT asset inventory – hardware, software, systems and sensitive data that needs to be protected. This will be the base of your IT security assessment
- Next, identify all entry and access points to all the networks, systems and applications. Exploiters can use such places as entry points for potential attacks. Hence, you need to monitor and safeguard these points proactively
- Assess the effectiveness of your current cybersecurity risk assessment processes. These could be firewalls, accessibility controls, data encryption and other forms. Understanding gaps in your IT risk management strategy can help improve those focus areas
- Review the system configurations and software security settings. Correct or optimize any locations that are not properly established
- Scan your IT infrastructure, codebases, websites and systems for security vulnerabilities using automated vulnerability scanner tools
- Review previous incident reports and learn lessons from earlier weaknesses and attacks
- Interview the employees to understand any possible workflow gaps and better the chances of human errors or malicious attempts by someone with system access
Also Read : How to Reduce Risk of Outsourcing IT Services?
Step 2 – Risk Ranking and Prioritizing (IT Risk Assessment)
![]()
Things to know about IT Risk Assessment
What happens in IT Risk Assessment?
After risk analysis, you need to analyze and evaluate each identified risk for its likelihood of occurring and its possible impact on your business processes. This is known as security risk assessment and risk priority ranking. Each risk can be assessed based on three significant basepoints based on their impact on – confidentiality, integrity and availability of systems and data.
What factors should be considered in the Risk Assessment Process?
- Likelihood of occurrence
- Operational impact
- Financial impact
- Reputation impact
- Regulatory complications
What is a Risk Analysis Assessment Matrix?
You can create a Risk Assessment Matrix such as –
| Risk Rating/Likelihood of Occurrence | Priority Level |
|---|---|
| Highly Likely (60-100%) | Critical – 1st Priority |
| Moderate (20-60%) | Major |
| Unlikely (0-20%) | Last Priority |
Here, the risk rating shows the severity of the identified risk, and the likeliness of occurrence shows the probability of that risk occurring in your IT infrastructure. This can be an excellent guideline to honestly assess and rank your risks to see where to focus efforts first and what can be avoided or delayed. Categorizing risks into different levels can help better understand the overall task and optimize resource utilization and project completion time. However, it only provides a theoretical perspective, and practical aspects sometimes favour lower-priority tasks.
What is the Process of IT Risk Assessment?
- Prioritise risks using Risk Matrix Systems or other alternatives
- Assess the severity of each risk based on factors like financial impact, operational disruption and data sensitivity
- Assign numerical values to risks for quantifying their impact and likelihood, if possible
- Determine your risk tolerance levels for IT-related risks. This would help later in the IT risk mitigation decision-making process
- Create real risk scenarios to model high-priority tasks’ potential consequences and impacts
- Estimate the probability of each risk occurring by leveraging previous records and data or/predictive algorithms
- Combine the values of likeliness and severity to get overall ratings for each high-priority task
- Visually represent this risk priority chart using charting libraries or data visualization tools
- Categorize each risk by category – compliance, cybersecurity, compliance, strategic or operational
- Maintain proper documentation of the IT risk management process with all the calculations, assumptions and assessments
- Share the result of the security risk assessment process with all involved stakeholders to enable data-driven decisions
- Start preparing the IT risk mitigation plan for all the high-priority risks. Make sure to reassess and reevaluate the mitigation plan periodically
- Ensure all risk mitigation and assessment plans align with the needed regulatory and industry requirements
Step 3 – Setting up IT Risk Mitigation Plan
![]()
Things to know about IT Risk Mitigation
What is Risk Mitigation in IT?
Risk Mitigation refers to the corrective actions taken to reduce the impact of potential IT threats on the business’s IT infrastructure, processes and sensitive data. The purpose is to minimize the adverse effects of such hazards and disasters, especially on business processes and continuity.
What are the four popular Risk Mitigation Strategies?
The popular types of risk mitigation techniques are –
- Risk Avoidance
- Risk Acceptance
- Risk Transfer
- Risk Reduction
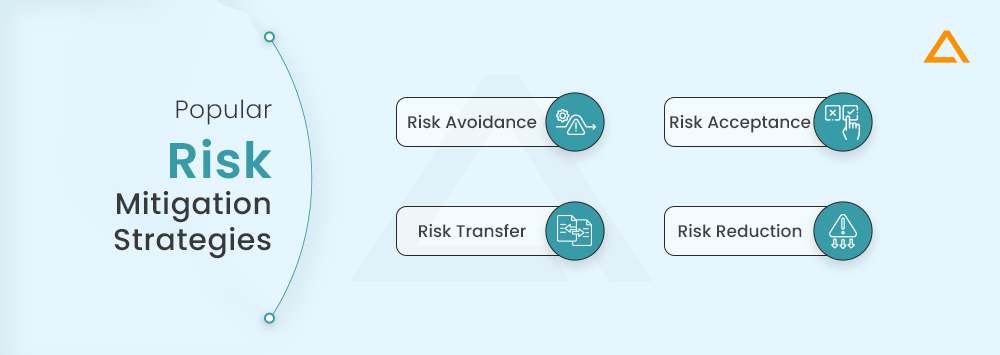
Risk Avoidance: Actions taken to eliminate or avoid a particular risk. Here, you accept the call to discontinue a specific service, product, feature or aspect of your project that can expose your IT infrastructure and operational processes to a particular risk. For instance, you may want to avoid using a specific software solution with questionable security standards.
Risk Acceptance: When you are willing to acknowledge the existence of an IT risk but not take an active interest in resolving it or mitigating it. When you conduct a risk assessment, the risks identified and valued at low Priority would generally not be worth the cost, time and investment to outweigh the mere impact it has on your business processes. So, such risks can be pushed for later.
Risk Transfer: If you have many processes to handle and care for, you can consider transferring some of the load to third-party vendors and service providers. For instance, you could outsource your risk management project to an offshore development centre with talented risk mitigation experts who could manage end-to-end risk management services for you.
Risk Reduction: For IT security risks that cannot be avoided or transferred, you will aim to reduce the likelihood of it happening or minimize its expected impact. You must implement controls, security best practices and proper measures to mitigate identified risks. Unlike other IT mitigation strategies, this is a proactive approach.
How to Mitigate Information System Risks?
- Improve your security controls like firewalls, data encryption standards, 2-factor authentication and other such practices. Make sure to hold back power enough to reduce the chances of IT risks arising
- Establish proper access controls and follow the principle of least privilege to ensure limited authorization and access
- Provide proper cybersecurity training and raise awareness regarding phishing, safe internet usage and other cyber threats
- Develop comprehensive IT risk management security policies and procedures and ensure they comply with your industry standards and compliances
- Regularly backup critical data and keep backups available offline for better recovery
- Separate high-risk systems from the other parts of your IT infrastructure to reduce the spread of compromise
- Leverage data loss prevention tools for detecting unauthorized access or attempts to access sensitive data
Step 4 – Risk Management Monitoring & Reporting
What is risk monitoring and reporting in IT?
Any risk assessment methodology followed needs to be cross-verified for results, outcomes and efficiency to honestly know how our efforts impacted the overall IT infrastructure security standards.
What do you mean by risk monitoring?
Risk monitoring is keeping track of the level of risks and their impact on any organization. It is a systematic approach to track and evaluate risks and the applied risk management strategies to overcome them.
What are the three objectives of IT Risk Reporting?
IT Risk reporting is mainly used for checking the outcome of the entire risk identification, assessment, mitigation and monitoring efforts to check its impact and resilience.
How frequently should we conduct Risk Assessment and Monitoring activities?
This depends on the basis and nature of your IT risks and the availability of talents and a dedicated development team to carry out these activities. You can outsource IT risk assessment to a reliable Enterprise Mobility Solutions Provider with experience in risk management solutions.
How do you create a proper IT Risk Assessment Report?
- Start by defining the report’s scope with your primary objectives, an overview of current risks, continuous updates of risk mitigation efforts and highlighting any emerging risks
- Next, identify the key stakeholders – board members, IT teams, external stakeholders and regulatory bodies
- Gather all risk data in a concise document that records risk assessments, security audits, incident reports and vulnerability assessments
- Group the risks into similar categories to provide a structure that makes the IT risk report easy to understand
- Explain each risk’s severity and context so the stakeholders understand the possible impact and importance of addressing or not addressing a particular risk
- Establish performance metrics and KPIs to assure quality insights that help improve the overall security of IT processes
- Visualize these heavy data sets into easy-to-understand tabular formats or charts and graphs
- Offer risk mitigation recommendations as a TL; DR section for those stakeholders who can’t spend enough time reviewing the entire report
- Properly document the report with title, date and version number. Include details of the person who created the report for accountability and accessibility
- Validate the report before submitting it to the stakeholders
- Schedule a follow-up to address any questions, queries, concerns or plans of action for phases 2, 3 and so on
- Keep the loop going and aim for continuous improvement
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites
Wrapping Up!
This is a quick guide on IT risk management explaining the importance of setting up a proper risk management strategy and discussing the step-by-step implementation process. If you need help handling your IT risk management solutions, you can leverage our IT strategy and consultation services to secure your IT infrastructure and improve its performance.


 Say
Say