Quick Summary:
Over the past decade, globalization has become a term firmly embedded in our vocabulary. One of the things in which globalization has rapid growth is when a company wants to expand its services but is on a tight budget and can go for its services, functions, or production processes outside its home country. The popularity of growing outsourcing trends can be seen in some stats provided below:
According to the report generated by fortunly,
- Every year, some 30,000 jobs are exported from the US.
- 71% of CEO’s in the financial services industry outsource or offshore some of their services.
- 78% of companies throughout the world are pleased with their outsourcing partners.
- More than 93% of businesses are either exploring cloud services or have already started using them to improve outsourcing.
- Data security is the top issue for 68% of outsourced organizations considering switching to cloud technology.
- Over 44% of chief intelligence officers claim that compared to five years ago, they are now more likely to use outsourced sources.
- The percentage of their IT departments’ budgets on outsourcing increased from 12.7% in 2019 to 13.6% in 2020, maybe despite or perhaps as a result of the COVID-19 epidemic.
The process of offshoring an IT Services is not straightforward it requires rigorous planning and management to ensure that the risks and expenses do not outweigh the advantages offered of offshoring.
There is a chance for significant financial savings. Still, these benefits must be balanced against the dangers, including information security and privacy, IT offshore outsourcing defective service or loss of service completely, and legal and political problems that can occur when conducting business operations across international borders.
If these security threats materialize, they could endanger current business ties and result in serious issues for both the client and the offshore provider. However, let’s first evaluate all the stages of an outsourced project and adopt a holistic viewpoint before delving into the major offshore outsourcing security risks.
Outsourcing Security Risks: FMEA Analysis
FMEA, or failure mode and effects analysis, is also a critical analysis and potential failure modes and effects (FMECA). It is a step-by-step method for locating potential design flaws, manufacturing errors, or poor services; the US army pioneered this. Let’s take a closer look at each stage, leading to the strategic planning stage.
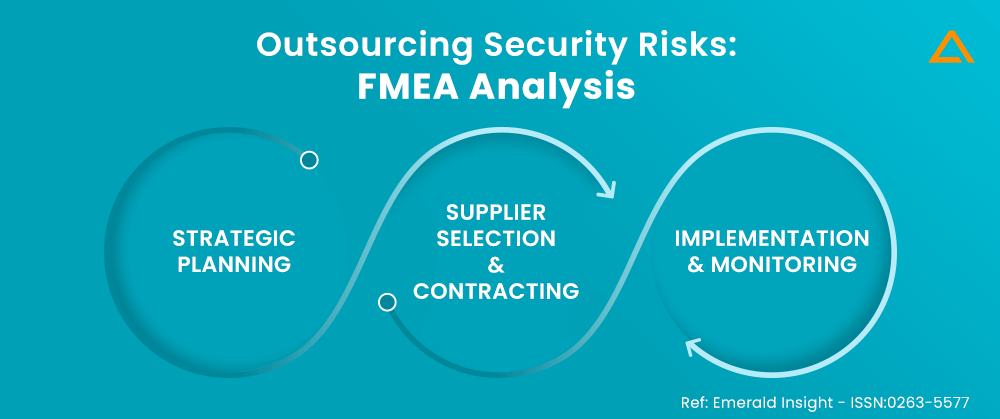
Phase: Strategic Planning
Activities included: Activity Selection, Entry Mode Choice, Location Choice
This sub-phase includes the company’s outsourcing goal which helps in analyzing business process to identify the processes which are adaptable being outsourced or can be localized.
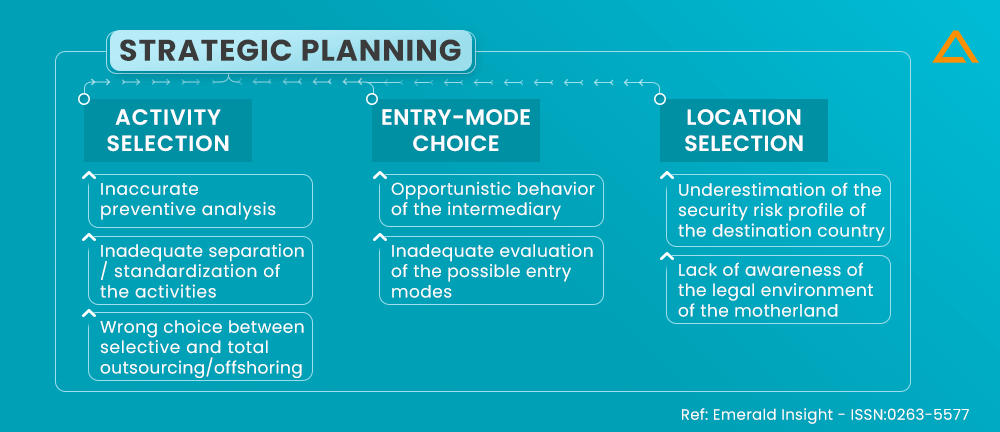
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ Inaccurate preventive analysis. | ✤ Picking outsourced-incompatible activities. | ✤ Decrease in security and key competencies. | ✤ To build a team for business process studies and to extensively evaluate the business process. |
| ✤ The activities were not properly broken down and assigned. | ✤ Activities that are connected but distinct from one another are separated and developed. | ✤ Wrong results additional expenses and ongoing information flow. | ✤ To implement company restructuring. ✤ Dividing up commercial operations into their constituent parts. |
In this section, we’ll talk about how to handle offshore outsourcing, which calls for choosing the best strategy for breaking into international markets.
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ Inadequate examination of all possible entrance mechanisms. | ✤ The entry mode was not the right one. | ✤ Actions within your management that are localized and externalized lessen. | ✤ It is crucial to assess the entry tactics used in foreign markets carefully. ✤ Look out for the qualities of the activity that can be transferred. ✤ Your initial move needs to be straightforward activity transfers. |
| ✤ Mismanagement of middlemen and their selection. | ✤ Mediators’ shady behavior. | ✤ When private information is given to opportunistic third parties, there is a risk that it may be misused and that intellectual property will be compromised. | ✤ It’s crucial to carefully assess intermediate reliability before making a decision. ✤ It is required to create statutory, administrative, and technical controls to restrict the intermediary’s opportunistic behavior. |
In this stage, the common blunders made while deciding where to outsource the project are discussed. Consideration should be given to industrial policies, the legal and political climate, cultural differences, and more.
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ A low estimate of the destination countries’ security risk landscape. | ✤ A dangerous country was chosen using protection measures that are insufficient for a foreign environment. | ✤ IP protection is insufficient in the country of destination. | ✤ To thoroughly assess each potential host country’s qualities. ✤ A thorough examination of efficient national protection measures. |
| ✤ Lack of knowledge of the environment in the origin. | ✤ Limitations on moving the chosen activities. | ✤ The offshoring project can’t be managed as planned. ✤ Increased susceptibility to data and intellectual property. |
✤ Must agree with the domestic labor unions on every facet of the outsourcing project. ✤ To investigate all potential delocalization restrictions. |
Also Read: How to Setup an Offshore Development Center in India?
Phase: Supplier Selection and Contracting
Activities included: Supplier Selection, Contract Drafting
The only project activities discussed in this phase are those that have been handed off to an offshore development firm.
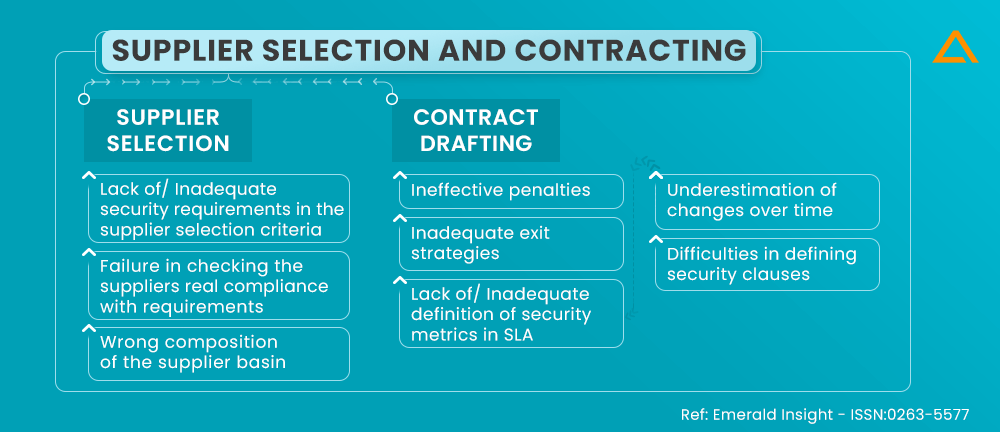
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ The supplier selection criteria’s inadequate security requirements. ✤ Failures to verify suppliers’ actual adherence to security requirements. |
✤ Choosing a provider who is unable to comply with the set security criteria. | ✤ Inadequate security of the provider’s received data and resources, loss of essential skills. | ✤ Incorporating security elements into the supplier selection criterion. ✤ To thoroughly instruct the quality inspectors. |
| ✤ Unsuitable supplier quantity. | ✤ The supplier receiving pertinent know-how. ✤ Costly transactions. ✤ Managing relationships poorly has problems. |
✤ Higher contractual power for suppliers. ✤ Prospective opportunistic actions. |
✤ Confirming the information gathered. ✤ The number of supplier basins should be carefully examined |
Contract drafting can cause various security issues, as it is considered to be the main legal protection tool as it allows the parties to assign responsibilities and obtain an adequate compensation when IP breaches occurs.
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ Defining security provisions might be challenging. ✤ Security metrics are not adequately defined in SLA. |
✤ Security issues aren’t adequately covered by contracts. | ✤ Possibility of opportunity seeking. | ✤ To precisely describe the security provisions. ✤ SLA should be updated to include the proper security metrics. |
| ✤ Non-working sanctions. | ✤ Breaking contracts is not expensive. | ✤ Clauses being violated. | ✤ Adding sanctions that are in line with the risks. |
| ✤ Underestimating the period’s changes. | ✤ Insufficient contract reviews contractual rigidity. | ✤ Exposure to new dangers. | ✤ To plan for annual evaluations of the contract. |
| ✤ Inadequate escape mechanisms. | ✤ When the connection ends, it’s unclear. | ✤ Sensitive data and expertise lost when operations are moved back to the corporation or another provider. | ✤ Use flexible contracting. ✤ Determining the best practices for concluding each commercial relationship. |
Phase: Implementation & Monitoring
Activities included: Management of the Transaction
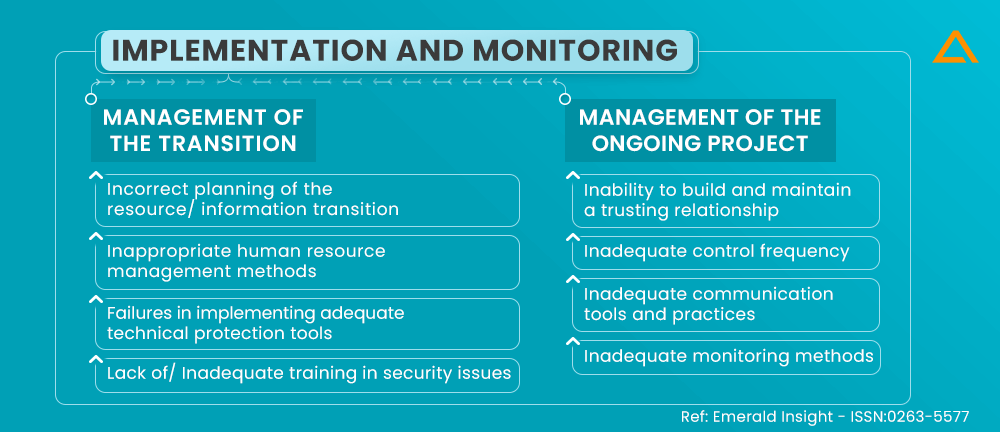
This can be broken down into two steps to make it easier to understand. The first is a transitional stage from the organization’s initial solution to its ongoing operations and new configuration.
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ A lack of proper planning for the shift of resource information. | ✤ Data, technology, and hardware losses, modifications, and deterioration. | ✤ Increased vulnerability as a result of inaccuracy of findings for which additional funds were invested. | ✤ To establish a thorough transfer strategy. ✤ To plan a trial project. |
| ✤ Techniques for managing human response that is insufficient. | ✤ A drop in staff confidence and motivation. | ✤ An increased security vulnerability is a result of higher personnel turnover. | ✤ To assemble a group that includes the client and the employees. |
| ✤ Insufficient knowledge of security matters. | ✤ Employees that are not aware of the security requirements, secret information, or procedures. | ✤ Heightened vulnerability brought on by staff mistakes or ignorance. | ✤ To organize employee training on security matters. |
| ✤ Inadequate analysis of the new buyer-supplier configuration | ✤ Inadequate protection tools in the link between buyer and supplier | ✤ Opportunistic behaviors | ✤ Using technical protection tools ensures that the provider or the subsidiary can only access the right information. |
As Discussed above, the first section is transitional stage, this stage deals with any damages caused in terms of data and hardware.
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ Incorrect planning of resource information transition. | ✤ Losses, changes, and damage of data, information, software, and hardware. | ✤ Increased vulnerability due to wrong results on which extra money was spent. | ✤ To set up a detailed transfer plan. ✤ To organize a pilot project. |
| ✤ Inappropriate human response management tools. | ✤ Decrease in personnel confidence and motivation. | ✤ An increase in staff turnover leads to an increase in a security vulnerability. | ✤ To form a team that involves both the client and the staff. |
| ✤ Lack of training in security issues. | ✤ Employees unawareness of the security/ confidentiality data/ procedures to be preserved. | ✤ The increased vulnerability caused by employee’s errors or unawareness. | ✤ To plan the staff training on security issues. |
| ✤ The new buyer-supplier structure has not been adequately analyzed. | ✤ Inadequate security measures between the buyer and supplier. | ✤ Opportunistic attitudes. | ✤ Must employ technical security measures to guarantee that the supplier or subsidiary can only access the appropriate information. |
Looking for Offshore Development Center Company?
Aglowid offers robust and customized offshore development services for your business
Once the transition phase is over, the company has to deal with the ongoing management of the activates outsourced and localized aboard. This section gives you an insight on the same.
| Causes | Failure mode | Negative impact | Actions to avoid |
| ✤ Inadequate surveillance techniques | ✤ Weak security control over subsidiaries and suppliers | ✤ Inability to consistently identify suppliers or opportunities | ✤ To assign skilled personnel to the operation control and to carefully establish the monitoring tools |
| ✤ Improper management frequency | ✤ Failures to sustain the security objectives over time | ✤ Vulnerability to emerging risks | ✤ To periodically check if the management frequency is sufficient |
| ✤ Inability to establish and sustain a trusted relationship | ✤ Lack of cooperation | ✤ The business partners’ opportunistic behavior | ✤ To bridge the gap between cultures to plan team-building exercises |
| ✤ Weak communication techniques and tools | ✤ Interpretations and misperceptions | ✤ Inconsistency between the security objectives that must be met and those that are being implemented | ✤ To give the other parties precise and unambiguous information to deliver reporting on results that were anticipated and attained |
This was the security analysis on the basis of FMEA analysis, let’s take a look at the key risks associated with the cybersecurity when you are planning for offshore outsourcing.
Key Threats & Mitigation of Outsourcing Cybersecurity Risks
Because of the benefits it may provide, outsourcing is becoming more popular among many businesses, but it is also associated with several risks that must be addressed. In contrast, if they are not controlled, they could result in significant issues affecting several projects inside a single enterprise, not just one. In the early phases of improvement projects that increase their first impressions, third parties may benefit from the advantages claimed by some organizations.
Early on, the organization can start to ignore ineffective risk management and identification of identified hazards, which can reduce costs since the majority of these dangers could occur. As a result, outsourcing’s projected benefits may be significantly impacted.
Aside from all this, everything as service, often known as XaaS, has revolutionized the cybersecurity industry by allowing enterprise firms to outsource their development needs to outside providers, including software-as-a-service. To target the outsourced service, exploiters utilize both ransomware and artificial intelligence as a service. Malware outsourcing to a professional hacking outfit is also occasionally utilized. Now that you have an idea about some cybersecurity risks in outsourcing let’s take a look at the factors that can play crucial role in having a security loophole as well as their mitigation’s.

Also Read: IT Staff Augmentation vs Managed IT Services
Unencrypted Data Exchange
There are various ways in which organization can decrease the chances of being victim of various cyber-attacks possible. One of those loopholes is Unencrypted data exchange between the companies. There are various instances where companies are providing unnecessary access of the resources to the third-party organization. It is advisable that companies provide only the required access to the resources. Even in this age where it is important to keep security risks in the mind. Even so, many of these vendors frequently receive full access to a company’s administrative functions and servers.
It is recommended by the experts that whenever any sensitive information is needed to be exchanged it should be exchanged in encrypted form using various industry standard protocols such as AES, SHA-256, RSA, DES, Triple DES and more.
Third-party Data Breach
As a result of the reliance on third parties by businesses today, outsourcing sizable portions or entire modules to specialized suppliers in the IT industry is becoming more and more common. Contractor, third-party service provider, or SaaS vendor are all possible options. Consumer confidence has been harmed by the rising number of unauthorized third-party security breaches as well as the sensitive material they reveal. When sensitive information is taken from a third-party vendor or when their systems are exploited to access and take sensitive information housed on your systems, third-party breaches have taken place.
It is doubtful that these third parties will fully disclose all of their security measures since they are often not within your organization’s control. While some vendors might not, others might have strong security guidelines and effective risk management procedures. The actionable strategy must cover the information which 3rd organization they use, how and where to supervise which access, and precisely what will happen in the event of a breach.
Malicious Insider
The possibility of anyone having a personal malicious vendetta for your IT company is one of the hazards of outsourcing IT services. When you choose to use outsourced IT services, you have little control over the team members that handle your account. Every team member can be interviewed and given references when you employ an internal IT team, but this is only useful if you have the expertise to confirm the experience of new hires.
When you choose to use outsourced IT services, you have little control over the team members that handle your account. Verifying the experience and competence of the outsourced IT company is more crucial. Read internet reviews, make calls to references, and look for case studies. After doing all this, once you’re satisfied, you can assign the rights based on their roles.
Insecure Screening Process
Sometimes when the organization are hiring a third-party organization on the review of some known person they generally don’t do through research as they should before selecting anyone. It can lead the organization to become vulnerable to the various cyber-attacks if the preferred company is not taking necessary precautions.
It is wise to check out third-party organizations. Before contracts are signed, screening must take place. It must also be a continuous process. Establishing if the third-party organization’s activities are secure will be made possible by conducting independent audits of its operations. Once you are sure that organization is following a secure process then you can go for the selected organization.
Improper Authentication
Some businesses grant access to a single account for all of their representatives to a third-party service. The security of the organization’s data is substantially jeopardized by doing this, despite the fact that it might seem quick and easy. It could be difficult to find the source of a cyber security problem if the account is shared. Separate accounts contribute to greater security by making it harder for former employees to access the account after leaving the organization.
Lack of required Skillsets
Setting up a third-party group to work takes a lot of work, but that doesn’t imply that there are times when it’s preferable to walk away. It is not always possible that the person who is acquiring for outsourcing to control the skillsets of the person working on the project. It can also affect the project if you don’t know when to stop in the project. Having The management team from the main organization will have to decide whether moving forward as a unit is the best course of action if third-party IT security outsourcing risks such as data breach has occurred.
How to control the risks associated with outsourcing information security?
- Establish a full set of service level agreements (SLAS), including org charts, roles and duties, tasks, and deadlines, and specify the outsourced scope in the contracts.
- The agreements mention important personnel management problems like hiring, training, resolving conflicts, terminating employees, and access control.
- Check for compliance with established procedures by auditing against SLAS. Comparable with any vendor assurance audit, this should be carried out either by the internal supervision team or by an impartial organization unaffiliated with the provider of the services.
- To ensure security is thoroughly tested before deployment, ask the oversight team for approval before deploying any tools, systems, or changes.
- Please ensure that social engineering tests and simulated situations are administered to all internal and service provider workers to ensure that their responses are appropriate.
- Before penetration testing, include known app vulnerabilities to guarantee that the service provider discloses all discoveries.
- Finally, keep operations and security separate.
- As a result, significant information security outsourcing concerns are related to SOD and COI. It is advocated that businesses take responsibility for security governance and supervision and keep this job separate from all IT and business processes.
Wrapping up!
While weighing the many advantages and appeals of offshore outsourcing, IT organizations must weigh the outsourcing information security risks against the possibility of labour arbitrage. The breach might not have been the third party’s fault, but it can affect the organization’s credibility. Another possibility is that an outsourced company will strengthen its cyber security following a hack to avoid a repeat of the incident. Before making a choice, leaders must weigh all the relevant factors.
have a unique app Idea?
Hire Certified Developers To Build Robust Feature, Rich App And Websites
Also Check:


 Say
Say