The rise of internet consumption has reached more than 4 million users. That means the world’s half of the population uses internet and more than two-thirds of the world population now have smartphones.The high rise of mobile users has laid various organizations to optimize their websites for mobile users.
On the other hand, it has also pressurized many business and enterprises -especially from service sector who do not have built mobile applications, to develop mobile apps for users. That’s how began the rise of “On Demand Apps.”
Mobile Uses at Glance
Mobile is everywhere right from the time we wake with its alarm till we sleep while watching our favourite shows, reading news, or even chatting to friends.People use a cell phone for various purposes whether it is to order food, breakfast, book tickets, shopping, socializing and even staying up-to-date with news.
On Demand App – A Need of Time
On Demand App is now spread over all business sectors. However, it is highly beneficial for service sector industries such as food, banking, travel, ticket booking industries, just to name a few.
Take a look at the list of some top industries to make the most out of the ‘On-Demand Apps.’
-
- Food Delivery Services
- Grocery Delivery Services
- Job Searching Sector
- Home Services
-
- Tourism & Travel Services
- Healthcare Services
- eCommerce Services

The most interesting part is that the mobile searches have over passed desktop searches, now. That means mobile users do not just surf social media but also services and products.
That has resulted in many companies to re-think over their strategy and keep mobile users as a primary point in your strategy.
Challenges of On-Demand App
In fact, it has taken a revolutionary step now. But, talking about the development side, it has raised some big challenges before developers and development company too.
The demand for “On-Demand App” has also increased security concerns and that’s the primary selling point today. Every business owner begins with the security features in the app.
Even if they inquire, they never forget to ask about the security for the application.
According to stats by Varonis – A data Security company, more than 60% of companies and business organizations believe that ransomware is the biggest threat for them.
This is obvious that secrecy is the power of business and a little breach of data can make a huge difference.
Most of ‘On-Demand Apps’ saves important data such as Customers’ details, Credit/Debit Cards and much more. Therefore, the quality of the demand app is mandatory while the app must be cost-effective as business enterprises don’t want to invest any extra penny on the app.
Top Data Breaches – Importance of Security for On-Demand Mobile App
One of the most significant issues that a developer has to focus more is the security of the app. Security is the most crucial aspect of judging reliability, authenticity and performance of the app. Various things could increase the chances of an app’s vulnerability.
I have gone through various examples of data breaches which occurred in past that endangered the sensitive data of millions of users. I am giving you a glimpse of some of the top incident of data theft as well as malware attacks that made headlines. They are shocking yet good for learning.
Equifax Data Breach
Equifax is one of the leading consumer credit reporting agencies in the US which suffered a massive data breach in September 2018. Attackers stole sensitive information that includes credit-card, driver’s license, and Social Security numbers, date of birth, phone numbers, and email addresses of over 148 million users by exploiting the security flaw. The company had to face the consequences.
Uber Data Breach
Hackers accessed Ubers AWS account after getting access to login credentials. It stole away customer information of more than 57 million users. However, the Uber did not take legal way to short out the issue; instead, it paid $100,000 to the hackers to delete the information. However, it is not clear if the data has been actually deleted. (Inputs from Bloomberg)
UNC Healthcare
The healthcare university named the University of North Carolina Health Care System also got hacked that led 24,000 pre-natal patients data such as names, addresses, races, ethnicities, Social Security numbers and a variety of health-related information got hacked. (Source : Databreaches.com )
Common Attack
Recently, you may have heard the ‘The Wannacry Ransomware’ attack that scared users around the work and lead to 19,494 hospital appointment cancelled in the USA.
Various such incidents have taken place across the world. However, it’s the hack that was performed by hackers while there are breach threats examples found that were installed on your mobile phone too. Let’s figure them out what.
Copycat & ExpensiveWall
You may have heard Copycat? Oh! I am not talking about the most famous song sung by Billie Eilish from the album ‘Don’t Smile at Me’! I am talking about the malware which affected more than 14 million devices around the world which helped hackers to earn more than $1.5 million just in two months. It used outdated devices with fake apps. Other than this, the malware dubbed ExpensiveWall which automatically registered millions of users paid service without their permission. It affected more than 50 apps that were in Google Play Store. By the time Google removed them, it was downloaded between 1 million and 4.2 million times.
Lazarus Group Goes Mobile
This was the case with Samsung devices when a new cluster of malware samples attacked. The Lazarus Group is said to be behind the attack as there were Korean language speakers. The intention of the malware to affect the population of South Korea. It was earlier targeting PC and laptops too.
Pre-Installed Mobile Malware
Malware has affected almost all top mobile devices in the past years. The malware in the question came pre-installed with devices which users were not allowed to uninstall it. It had to send for re-flashed. That apparently means that this malware had access to the system privileges. Some reports state that most of the top Smartphone companies were a victim of it. However, it not clear yet whether how far the matter has been solved.
Some of the independent states also suggest that more than 300 apps in the Google Play Store were affected with malware. Those apps were even downloaded by approx 106 million users across the world.
Types of Security Threats on “On-Demand App”
In the paragraphs, you have through various data breach examples, but this does not occur automatically. It cannot happen unless we have left some loopholes in our app. Now, I would explain you the type of threats that may occur within your On-Demand App. Those are the threats which can be avoided (I have explained which you will read later in this blog).
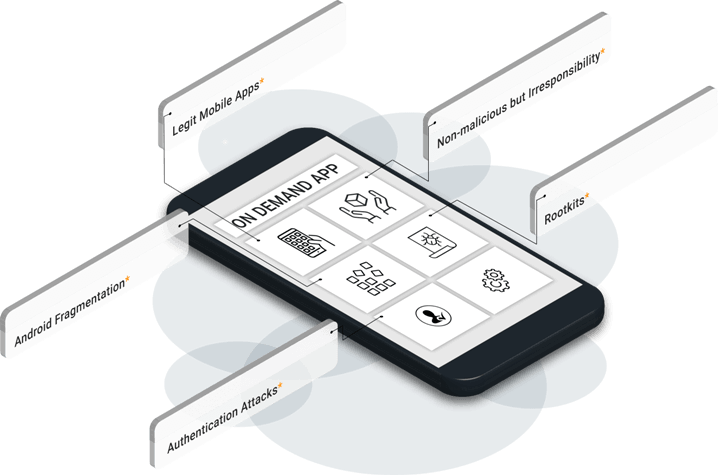
Legit Mobile Apps
According to Dave Jevans of Marble Security, enterprises face data breach threats from their employees who already installed apps than mobile malware. When you distribute your app to your employees, the app information may be accessed by the other app in the device and it could be sent to the app admin who can misuse it for personal gain.
Non-Malicious vs Irresponsibility
A survey conducted by CoSoSys says that 35% of employees think data security is no more the responsibility of employees. That makes them quite irresponsible and that is found that employee may leave their laptop or mobile devices opened publically.
Android Fragmentation
Installing or upgrading any updates that are in its beta version may not be beneficial for devices as initially the security patches are not given priority unless the final version is released.
Rootkits
They are highly untraceable but can give access to attackers, due to the nature of the Rootkits.
Authentication Attacks
Cyber-criminals are not only interested in getting information from your device storage; rather they steal away the information from the cloud as well.
In short, many other types of attacks could be explored. However, why not keep more focus on your security patch and educate your employee about the significance of data and what would be the consequences if lost.
Reasons for Security threats on ‘On-Demand App.’
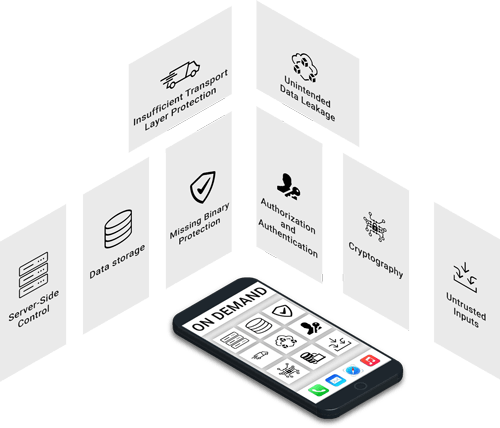
Server-Side Control
The backend web endpoint is not secure and that could result in insecure web application development.
Data storage
The app you install in your device may be vulnerable to breach. All this happens due to insecure encoding.
Missing Binary Protection
If binary protection is missing, it could increase the chances of data breach. Anyone can engineer the app steal the useful data.
Insufficient Transport Layer Protection
Attackers may eavesdrop when finds a loophole in the communication channel between the app and the server.
Unintended Data Leakage
Your device may leak sensitive data which could be accessible other apps in the same device.
Authorization and Authentication
It Authorization and Authentication is poorly implemented, it could lead to a sensitive data breach.
Cryptography
The insecure encryption algorithms lead to broken cryptography that results in a breach of data.
Untrusted Inputs
If the hidden fields, values or functionality are not properly implemented, it could help the third party to steal data.
Honestly Speaking
Why I am talking all these at the time when I am talking about ‘On-Demand App,’ its security and safety futures. I am a developer and understand every pros can cons of technology. I know that what would be the consequences of having an infected ‘On-Demand App.’ Your business, whatever it may be, is everything for you if I am not wrong. Getting your strategy leaked to your competitors could lead your business in a destructive direction.
In fact, ‘On-Demand App’ is very helpful but it could be equally dangerous if not properly developed while keeping all these security concerns.
Believe it or not, 100% of businesses, knowingly or unknowingly, have faced mobile malware attack. However, most of them are not so harmful as even the service provider or device manufacturers use malware to get information or detect problems with the device. However, all are not equal; you must be aware of everything happens with the device through the app.
Don’t Take me Wrong
What I have explained so far suggests how dangerous it is to have ‘On-Demand App.’ However, other phases also suggest that how important it is to have this app. For example, you can fulfill every expectation that you have regarding your business. However, again, the question would how to get the right solutions. As developer and tech enthusiast, I believe that everything holds two sides of a coin. The same thing is here with ‘On-Demand App.’ The threat is there, but it has more benefits than it carries risks. Importantly, if you are alerted, the threats can be avoided. In the following paragraphs, I have explained every possible thing that developers should do eliminate the chances of any vulnerability.
Solutions – How to secure On-Demand app?
As I have already mentioned that everything has solutions provided that how careful you are about everything, ‘ On-Demand App’ is the need of time and you will not want to miss the important opportunity offered by the trending technology. So, why not find a solution instead of ignoring it?
Let’s begin with the reasons that increase the chances of threats vulnerability.
High-Level Authentication
Always use high-level authentication as it contains password and other valuable information of your clients.
Hire a Trusted Developer
It goes without saying that how important it is to hand over your project to the trusted development company or developers. When you get your project developed through the trusted company, it ensures that the developer uses proper technology platform with all required tools to make your app lighter, faster, stronger and reliable.
Frequent Testing
You will come across some new each time you test your app. So, do it frequently.
Cryptography Tools
Best Cryptography tools ensure that your app pays off. It would be best if you used secure containers instead of storing keys in hard-code. It could lead to hacking.
Don’t Just Use API
Never even try to use unauthorized APIs as it could lead to hacking.
Write Secure Code
Application building process starts with coding. It has been written in a very secure manner as it could lead to data breach too. Some researches reveal that more than 11.6 million hacks occurred due to malicious code.
Data Encryption
Encryption helps developers to convert the data in such a form that hacker won’t be able to read the information.
Encryption protects many things including
- Databases
- Files on servers
- Entire communication channels
- Hard drives
- Email messages
- And other potentially sensitive transmissions or storage of data
Be Careful While Using Third-Party Library
Never use a third-party library without testing the code as it may contain malware.
Wrapping up
Last but not least, I hope the article would meet your expectation regarding the security concerns that you have for ‘On-Demand App Development.’ There could be more options to explore about the safety features of the ‘On-Demand App.’ So, you also come across some new and exclusive ideas. We expect your valuable suggestion if you have. We are also open to provide all given or even not given information on the blog. Don’t shy to ask.
Boost your Business with
Highly Profitable On Demand Apps

 Say
Say